The latest update to iOS Forensic Toolkit brought bootloader-level extraction to a bunch of old iPads, Apple TVs, and even the first-gen HomePod running OS versions 17 and 18. This enabled full file system and keychain extraction on a those older Apple devices that can still run these versions of the OS.
Why old devices still matter (a lot)
This update is important for several reasons. First, it restores complete access to a group of devices that continue to sync large amounts of user data with iCloud, making them valuable secondary evidence sources. Second, it demonstrates how legacy vulnerabilities remain relevant even as those devices are updated to the latest generations of their respective operating systems. Finally, while a seven-year-old iPhone may seem old, many households are still using the 2025 version of Apple TV, which was later rebadged as Apple TV HD, and only discontinued seven years past its original release date. The more recent original Apple TV 4K is still widely used. iPads generally have a longer life than iPhones, too, often used for many years. As a result, devices based on aging hardware but running recent firmware can now be acquired and extracted.
checkm8 exploit explained
checkm8 is a well-known exploit targeting the unfamous bootrom-level vulnerability discovered in multiple generations of Apple devices. checkm8 lets an attacker run unsigned code very early in the device’s boot sequence. Because the bootrom is read-only code, the vulneratbility cannot be patched by an OS update, which is why checkm8 remains relevant years after it was disclosed. Practically speaking, the exploit is executed from DFU/bootloader mode and gives offline, bootloader-level control over affected devices – enough to load a custom ramdisk, dump memory, and perform low-level extraction workflows that bypass normal OS protections entirely. It applies to multiple generations of Apple SoCs (the older A-series family up through the A11), and enables full file system and keychain extraction on those models.
That said, checkm8 is powerful but far from a silver bullet: other platform components can still block extractions. A notable example is the A11 SoC: on iPhone 8, 8 Plus and iPhone X Apple introduced SEP firmware mitigations that prevent an attacker from using DFU-mode access to unlock the encrypted disk even though the underlying bootrom exploit still functions and remains unpatchable. No other affected devices received similar treatment regardless of the version of OS they were running.
Beyond iPhone
While iPhones remain the primary focus of most forensic workflows, Apple’s broader ecosystem includes several checkm8-compatible devices that are often overlooked yet can hold valuable data. The iPad 6 and 7, iPad Pro 2, Apple TV HD and first-generation Apple TV 4K, along with the original HomePod, all share hardware roots with older A-series chips affected by the exploit. These devices can run fairly recent – or even modern – builds of iPadOS, tvOS and audioOS, which are closely related to iOS. These devices synchronize with the user’s iCloud account, iPad tablets featuring the complete set of data while Apple TV and HomePod having a limited sync based on their feature set (and no keychain). This means that these devices can provide an alternative entry point when a user’s main device cannot be accessed.
Nitably, Apple TV and HomePod devices cannot be protected with a passcode, which eliminates one of the major barriers to data acquisition. Their storage can be accessed at the file-system level without facing user authentication restrictions, making extractions faster and more predictable. Although their market share is smaller compared to iPhones, these devices often replicate key information from other Apple hardware, turning them into important secondary sources of evidence within the same ecosystem. The Apple Watch presents a related but narrower case: checkm8 applies only to older S3-based models, and newer generations have moved beyond its reach, leaving extraction possibilities limited to partial logical or paired-device approaches (see Forensic Insights into Apple Watch Data Extraction).
Processors and OS version realities
It’s tempting to assume that major OS releases map neatly onto specific SoC generations, but real-world compatibility is messier. Apple’s iPhone lineup often shows a tighter correlation between new features and newer chips, because performance and security features are tightly coupled with SoC capabilities; however iPads, Apple TV and HomePod follow different product roadmaps and firmware branches. As a result, a given OS major version may run on a wider or different set of silicon across device families than an iPhone-centric model would predict. For example, the ancient Apple TV HD first released in 2015 with Apple’s A8 SoC (the same processor powering the iPhone 6) can run the current tvOS 26, while the iPhone 6, which was the donor of the SoC, only received iOS 12. It’s not just the iPhones, however. iPad 6 and 7 are based on the same SoC (Apple A10), yet the latest version of the OS for iPad 6 was iPadOS 17, while the iPad 7 received iPadOS 18, and the iPhone 7, which has the same chip, was only updated to iOS 15. This seemingly reflects Apple’s view on how long a typical consumer keeps using the various types of devices.
For forensic specialists this matters because the presence of a vulnerable bootrom is a hardware property, while the ability to mount and decrypt a file system depends on how that OS release interacts with SEP, key derivation and other features on that specific product. Some older chips can still host surprisingly recent OS builds, which expands the set of targets for checkm8-backed extraction but does not guarantee it. For example, while affected Apple TV and HomePod devices can run tvOS/audioOS 26, out toolkit currently does not support checkm8 extractions on these OS builds.
What’s new in the Toolkit (technical summary)
Speaking of iOS Forensic Toolkit 8.81, the update extends bootrom (checkm8) extraction to cover iPadOS, tvOS and audioOS builds from the latest major families (17 and 18) on a defined set of older devices, adding the ability to perform full file system dumps and decrypt the keychain. To achieve this the Toolkit’s disk unlock pipeline was reworked to accommodate the new key management workflow Apple introduced in OS 17; the underlying bootrom exploit remains the same, but the post-exploit steps now follow a different, device- and OS-specific sequence to recover the necessary cryptographic keys.
Functionally, the Toolkit now offers complete filesystem images and keychain contents on supported models while familiar limits still apply: success depends on the exact SoC and OS version, and on the presence of the passcode (on iPad models) that cannot be bypassed by a bootrom exploit alone.
Step by step instructions (cheat sheet)
We’ve described checkm8 extractions in previous blog posts, so just a quick cheat sheet here as a reminder. Everything past “//” is a comment; do not include these lines in your workflow.
Place the device into DFU, connect it to the computer, and run the following commands:
./eift_cmd boot -w // boot the device and run the exploit
./eift_cmd loadnfcd // load necessary libraries
./eift_cmd unlockdata -s // unlock data
./eift_cmd ramdisk keychain -o {filename.xml} // extract and decrypt the keychain
./eift_cmd ramdisk tar -o {filename.tar} // extract and decrypt full file system
./eift_cmd ssh halt // turn the device off
These commands will extract and decrypt the keychain, then pull the image of the file system.
When you unlock the data partition, you’ll see the following output:
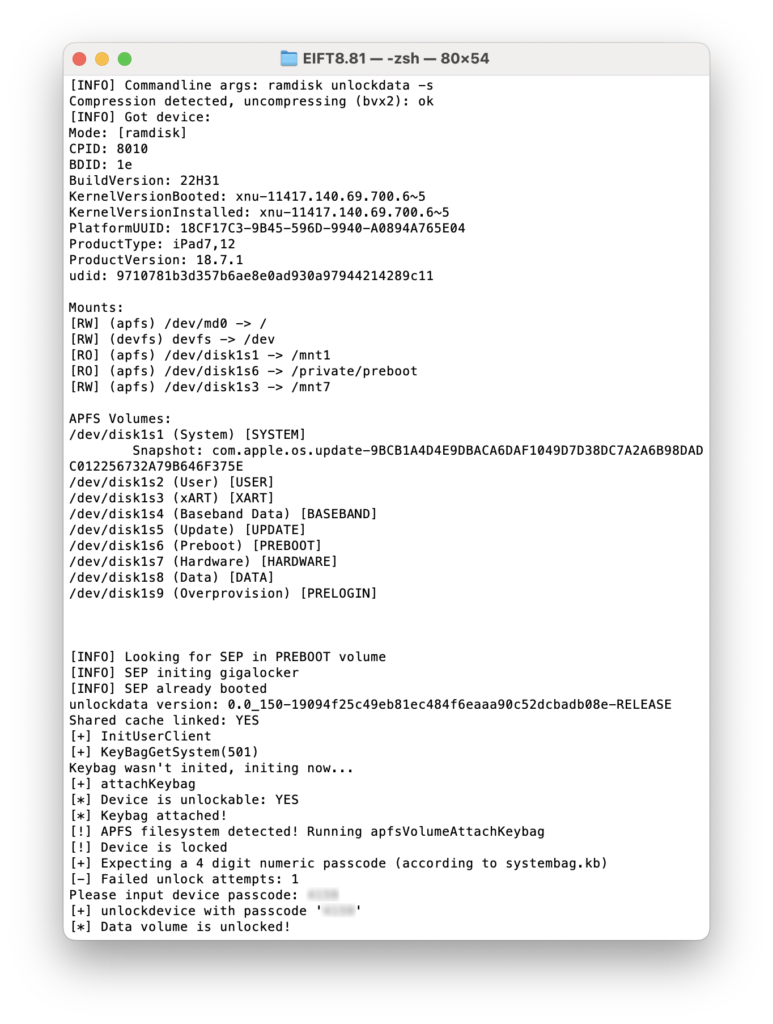
And this is how keychain extraction works:

Conclusion
Older hardware, such as older iPads, Apple TVs and HomePods, is still relevant, and older exploits retain practical forensic value: they can unlock access to devices that still run modern software but built with vulnerable silicon. It is important to inspect the whole Apple ecosystem, not just phones, because Apple TV and HomePod often contain synchronized or complementary evidence. Legacy iPads running recent versions of iPadOS can contain nearly as much information as an iPhone thanks to iCloud sync. A comprehensive, cross-device approach will yield better reconstructions than focusing on a single handset. File system images extracted from devices running iPadOS 18 are valuable by themselves as they offer a peek into Apple’s evolving data structures.




