In the world of digital forensics, there are various ways to analyze computer systems. You might be familiar live system analysis or investigating forensic disk images, but there’s yet another method called cold system analysis. Unlike live analysis where experts deal with active user sessions, cold system analysis works differently. It’s like a middle ground between live analysis and examining saved images of a computer’s storage. But why and when would someone use cold analysis? What can you do with it, and how does it compare to the usual methods?
What is cold system analysis?
Cold system analysis is frequently used in the field, yet the term itself is not quite as common as “live system analysis”, so it needs a bit of an explanation. The term was born after the “cold boot attack”, which in turn defines a very specific kind of attack allowing to extract secrets (such as encryption keys) from the system’s volatile memory. In the course of a cold boot attack, the expert boots the computer from a portable media (typically a USB flash drive). This is exactly what is used during the cold system analysis: the examiner boots the computer from a portable USB drive and attempts to gain access to the system and/or extract evidence from the computer.
What is “live system analysis” then? In live system analysis, the examiner attempts to gain control over an authenticated user session. This is only possible if the computer being investigated is turned on, and at least one user has an active session. The cold system analysis presumes that the initial state of the computer is powered off or hibernated, and no authenticated user session is available.
The opposite of live system analysis is the examination of forensic disk images, which are bit-precise captures of the user’s physical storage devices. Even if something happens to the data stored in the disk image during investigation, it is always possible to go back to the original file.
The risks of cold system analysis
Live system analysis is the riskiest of the three methods. An authenticated user session may be full of surprises. There may be unknown (and potentially dangerous) background processes running, and any available evidence can potentially self-destruct at any time. If the computer is connected to the network, much worse can happen, while breaking the network connection may trigger unknown, potentially dangerous tasks. Live system analysis is never forensically sound, and should be only performed after carefully weighing the risks.
Working with forensic disk images is the safest method, which at the same time is the most labor-intensive and time-consuming. This is the most forensically sound method.
Cold system analysis sits in between. By booting the user’s computer from a known good portable media, experts have access to a clean system with familiar forensic tools. However, it’s still the suspect’s computer, and user mistakes make room for irreversible accidents. One of the most common mistakes, by the way, would be hasting to reset the user’s Windows account password, which instantly and permanently locks the ability to access EFS encrypted files and any passwords stored in Web browsers such as Google Chrome or Microsoft Edge. However, when used carefully, cold system analysis can deliver significant benefits over the analysis of forensic disk images without most of the risks associated with live system analysis. Results obtained with cold system analysis may or may not be forensically sound depending on the tools and techniques you used.
Cold system analysis step by step
We made forensically sound cold system analysis easy with Elcomsoft System Recovery (ESR). Unlike competing tools, most of which are Linux-based, Elcomsoft System Recovery is based on the familiar Windows environment, thus being an ideal tool for investigating Windows computers.
Once you prepare a bootable USB drive by running the Elcomsoft System Recovery installer, you will be able to perform a wide range of tasks depending on whether or not the system partition is encrypted.
Two modes are available: the forensically sound, write-blocking “read only” mode, and the other mode in which you can modify user accounts by resetting passwords, assigning administrative privileges, and so on.
Once you boot into ESR, you’ll be able to choose between disk tools and account tools (SAM database).
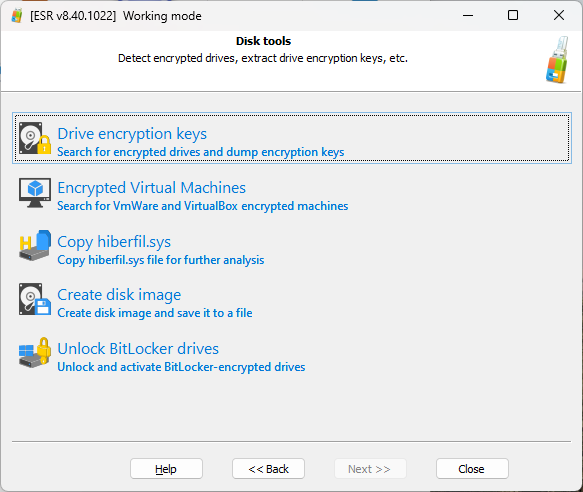
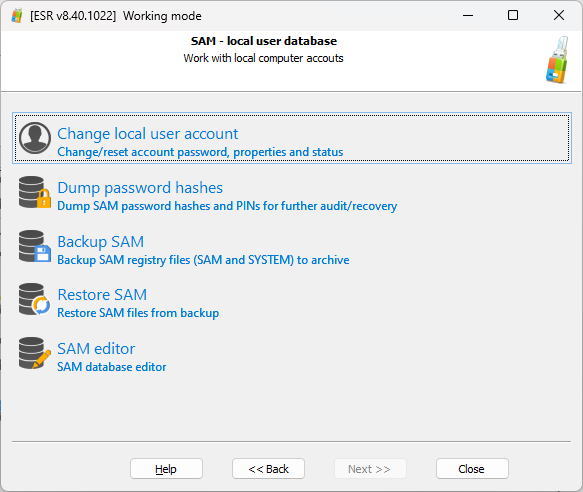
Remove BitLocker protection
If the system partition is encrypted with BitLocker, there is very little you can do before unlocking the volume. In this scenario, you can boot into Elcomsoft System Recovery, capture the volume’s encryption metadata, bring the data to the lab and attempt to recover the original BitLocker password by running Elcomsoft Distributed Password Recovery.
Depending on the configuration of protectors used on the particular BitLocker volume (which mostly depends on whether or not the system has a TPM module), you may or may not be able to unlock the volume. More in Unlocking BitLocker: Can You Break That Password?
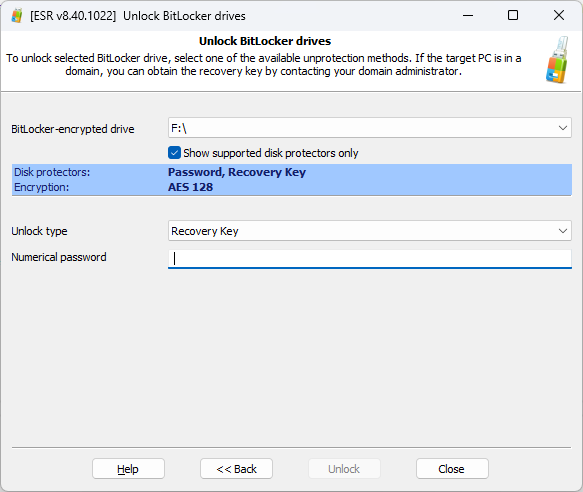
If you have a password or BitLocker recovery key to the system volume, ESR can unlock and mount the volume using the built-in BitLocker functionality of Windows PE. Once this is done, you can continue analyzing the disk, which is a huge time saver compared to the traditional imaging and decrypting workflow.
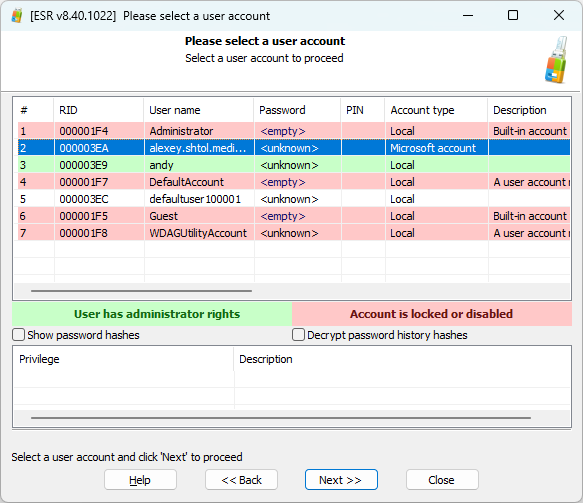
Collect existing passwords
Once you boot into Elcomsoft System Recovery, the tool will probe existing Windows account for common passwords. If a password is discovered, it will be displayed to allow further analysis.
Break Windows account passwords
What if the passwords are unknown? If this is the case, you will need to run an attack to recover the original passwords. To do that, you’ll need to extract encryption metadata (hashes), and use that data in Elcomsoft Distributed Password Recovery to launch the attack.
Unlock disk encryption
If the computer had not been shut down but was discovered in a state of hybrid sleep or hibernation, you may be able to find on-the-fly encryption keys (OTFE keys) to disk encryption tools such as BitLocker, TrueCrypt, VeraCrypt or PGP. These keys may be found in hibernation or page files. During cold system analysis, you can extract these files and save them on external media for further analysis with Elcomsoft Forensic Disk Decryptor.
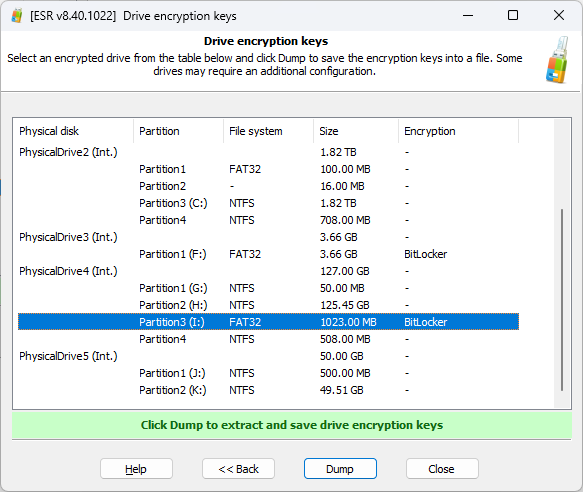
Search for encrypted disks
Speaking of disk encryption, cold system analysis with ESR allows finding encrypted disks by running a thorough automated search.
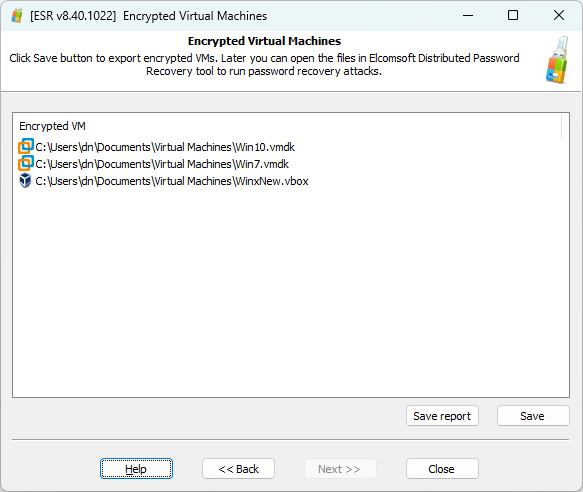
Search for encrypted virtual machines
Along with disk encryption tools, encrypted virtual machines are among the most common cover-up tools. You can look for encrypted virtual machines in ESR, which, again, is an automated process. Once the tool finds an encrypted VM, it automatically saves the encryption metadata that you can use in Elcomsoft Distributed Password Recovery for breaking the original password.
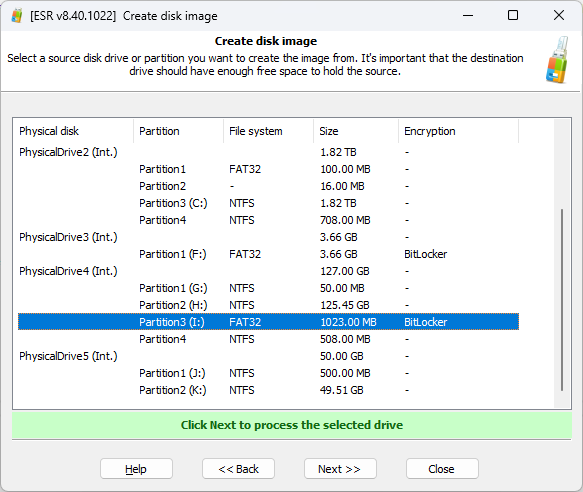
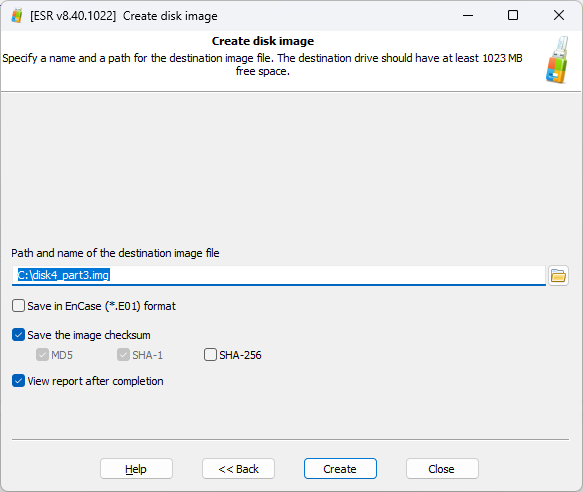
Create forensic disk images
There is only so much you can do at the cold system analysis stage, and making disk images is one last shortcut you can take to speed up the investigation. Traditionally, experts would disassemble the computer, take the disks out and make their images with a specialized write blocking disk imaging device. ESR offers a shortcut, allowing to make forensic disk images without taking the drives out.
The quick and dirty of cold system analysis
Cold system analysis is as forensically sound as you make it. In certain cases, you may afford losing the “forensically sound” part for the sake of efficiency. A good example is emergency unlock of ex-employees’ Windows accounts, re-assigning administrative privileges or simply restoring the computer’s functionality by removing maliciously or accidentally set Syskey protection.
Unlock Windows accounts
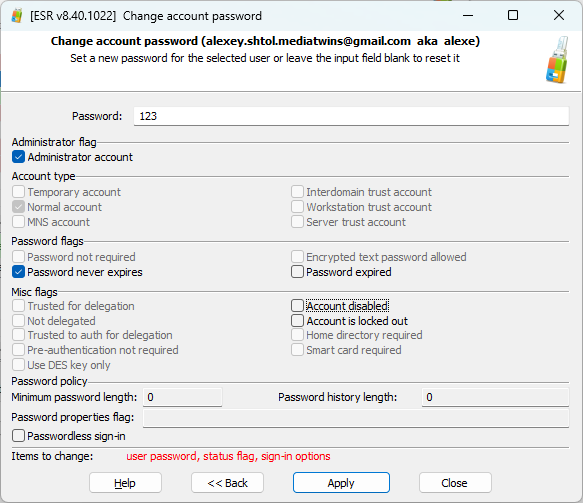
The need for unlocking accounts of Windows users is common in organizations with under-administered networks. ESR makes this extremely easy to do; changing a password of any Windows user is literally a matter of several clicks. Note, however, that this is far from being forensically sound: if you reset a user’s password, any data encrypted with Windows DPAPI (e.g. encrypted file system, stored passwords etc.) will be permanently lost. This may still be acceptable in many cases, so here is the how-to article: How to Unlock Windows Systems with a Bootable Flash Drive
Assign administrative privileges
Assigning administrative privileges to a certain Windows account may be needed to restore full access to the system if the administrative password is lost or unknown. ESR makes this possible in a few clicks. The feature also works for accounts for which you’ve reset a password with Elcomsoft System Recovery.
Remove Syskey protection
If you haven’t heard about Windows Syskey protection, you are not alone. This feature does not provide any real security, but has the potential if becoming a great hassle if someone who knows about the feature accidentally or maliciously sets a Syskey password. We have an article on Syskey passwords: How to Reset or Recover Windows SYSKEY Passwords.











