BestCrypt, developed by the Finnish company Jetico, is a cross-platform commercial disk encryption tool directly competing with BitLocker, FileVault 2 and VeraCrypt. Volume encryption is available for Windows and macOS. Learn how to break BestCrypt full-disk encryption by recovering the original password!
Full-disk encryption and crypto-containers
When it comes to disk encryption software, there are generally two major options. One encrypts the entire disk or partition; this is how LUKS works in Linux, BitLocker in Windows, and FileVault 2 in macOS. The other creates a virtual disk image (a so-called “crypto-container”), usually stored on existing disk volumes in a single encrypted file or a set of files. For this purpose, many users choose VeraCrypt. BestCrypt offers a commercial, cross-platform alternative to these encryption tools. Currently, BestCrypt comes in two separate editions, BestCrypt Volume Encryption offering full-disk encryption and BestCrypt Container Encryption encrypting virtual disk volumes stored in files.
We already had support for BestCrypt containers; more on that in Breaking Jetico BestCrypt. Today, we’re adding support for Jetico’s full-disk encryption tool, BestCrypt Volume Encryption 5.
What about the previous version of BestCrypt Volume Encryption, version 4? There are two notable differences between BestCrypt Volume Encryption 4 and BestCrypt Volume Encryption 4. First, the v5 adds a new encryption option: the ARIA-256 algorithm. Second, the developers enabled a custom number of hash iteration, but for some reason only for the newly added ARIA-256 encryption algorithm. This does not change the attack or the workflow; the same principles and steps of password recovery apply to both generations of BestCrypt Volume Encryption.
Encryption
Similar to open-source encryption tools such as TrueCrypt/VeraCrypt, BestCrypt supports multiple encryption algorithms including AES, ARIA, Camellia, Serpent and Twofish. According to BestCrypt developers, every algorithm is implemented with the largest possible key size defined in the algorithm’s specification, all available with the most secure XTS encryption mode. In our experience, the choice of the encryption algorithm does not affect the speed of attacks. Choosing any encryption algorithm other than AES dramatically reduces the speed of data access for the end user, without delivering any tangible increase in security. If anything, choosing the wrong algorithm may hinder security by exposing the encrypted data to any vulnerabilities that may be discovered in such algorithms.
What does affect security (and the speed of the password recovery attack) is the choice of the hash algorithm and the number of hash rounds (iterations) used in the corresponding Password-Based Key Derivation Function.
Hash function
It is important to understand that the data on the encrypted disk is never encrypted directly with the user’s password. You may be surprised to learn that the data is encrypted with a long, binary, randomly generated key that has zero dependence on the user’s password.
Moreover, that encryption key is stored in the encryption metadata alongside with encrypted information. Naturally, a question arises: can we extract that key from the encryption metadata and use it to decrypt the files and folders? No we can’t: the key (often called a Media Encryption Key, or MEK) is encrypted with yet another key, the Key Encryption Key (KEK). The Key Encryption Key, in turn, is encrypted with the user’s password – but not directly.
The password is transformed into a binary key with numerous rounds of a certain one-way mathematical function, which is called a “hash function”; the correct name for the transformation function is PBKDF, or Password-Based Key Derivation Function. The resulting key is then used to encrypt (or decrypt) the Media Encryption Key, which we need to decrypt the data.
Traditionally, disk encryption tools make use of one or more well-known hash functions to perform the encryption. The most common choices are SHA-512, SHA-256, Whirlpool (512-bit), while the older SHA-1 should no longer be used due to the recently discovered collision. These hash functions are extremely fast to calculate, which would mean an extremely fast attack. In order to slow down potential attacks, developers of encryption tools use multiple thousands of rounds (or iterations) of the hash function to calculate the final encryption key.
Developers of password recovery tools, such as us, are well aware of that approach. We are using hardware acceleration, utilizing the massively parallel GPU cores found in today’s video cards to speed up the recovery by the factor of 50 to 500 compared to a CPU alone.
No GPU attacks
BestCrypt developers seem to be aware of the fact, and, instead of bumping the number of hash rounds to the million, decided to go with a hash function that cannot be accelerated with a GPU. The hash function used in BestCrypt full-disk encryption is called Scrypt. This algorithm is as fast as SHA-256, yet by design it makes it very costly to perform large-scale hardware-accelerated attacks by requiring large amounts of memory. Scrypt is also very common in newer crypto currencies.
The choice of the hash function makes GPU acceleration impossible since each thread would require a massive amount of memory, which the GPUs simply do not possess. As a result, you’ll be restricted to CPU-only attacks, which may be very slow or extremely slow depending on your CPU. To give an idea, you can try 18 passwords/sec on a single Intel Core i7-7700HQ CPU @ 2.80GHz (8 threads), or about 25 passwords/s on a single Intel Core i7-3930K CPU 3.20GHz (12 threads). Modern CPUs will deliver a slightly better performance, but don’t expect a miracle: BestCrypt’s PBKDF using the Script hash algorithm is made deliberately slow.
To give a point of reference, the same Intel Core i7-3930K 3.2GHz x12 CPU delivers a higher recovery speed for BestCrypt Container Encryption, which uses more traditional hash functions.
BestCrypt Container Encryption, Intel Core i7-3930K CPU 3.20GHz (12 threads):
- sha3-512 53 p/s
- Whirlpool-512 150 p/s
- sha-512 196 p/s
- Skein-512 262 p/s
- sha-256 273 p/s
BestCrypt Volume Encryption, Intel Core i7-3930K CPU 3.20GHz (12 threads):
No OTFE keys
For many encrypted disks, extracting the encryption key directly from the device’s RAM, its page or hibernation file is the way to go. If live system analysis is performed while the encrypted container is mounted, one may be able to dump the content of the computer’s RAM into a file and scan that file for on-the-fly encryption keys, which can be used to mount or decrypt the data without attacking the original password. Breaking VeraCrypt: Obtaining and Extracting On-The-Fly Encryption Keys describes the benefits of this approach, which can be summed up as guaranteed, near-instant access to encrypted data without the need for a lengthy attack on the password.
At this time, we do not support the extraction of on-the-fly encryption keys from the device’s RAM, hibernation or page files. The function is currently under development.
Breaking BestCrypt Volume Encryption 4 and 5 passwords
Our tools can break BestCrypt Volume Encryption 4 and 5 passwords that are protected with password based encryption. Follow these steps to set up an attack.
Step 1: Extract encryption metadata
During the first step, you must extract encryption metadata from the encrypted disk or virtual volume. Unlike TrueCrypt/VeraCrypt, BestCrypt stores information about the encryption algorithm, hash function and the number of rounds in the disk header. This encryption metadata helps set up an attack by automatically applying the correct settings. The encryption metadata can be extracted with Elcomsoft Forensic Disk Decryptor, which is included with Elcomsoft Distributed Password Recovery and available separately.
Elcomsoft Forensic Disk Decryptor is a powerful tool for accessing encrypted disks. A limited version of this tool included with Elcomsoft Distributed Password Recovery. You can use Elcomsoft Forensic Disk Decryptor users to set up attacks on a tiny file instead of the original encrypted container. Since no raw or encrypted data is included in encryption metadata, the hash files produced with Elcomsoft Forensic Disk Decryptor offer significantly higher level of privacy, allowing remote and cloud processing without the risk of a data leak.
To extract encryption metadata, do the following.
- Launch Elcomsoft Forensic Disk Decryptor.
- Specify the BestCrypt disk to extract encryption metadata from.
- Save the encryption metadata.
Once you are done, collect the extracted hash files and open them in Elcomsoft Distributed Password Recovery to set up the attack.
Alternatively, you may use Elcomsoft System Recovery to extract encryption metadata from the target computer by booting from the USB media. In this case, use the following workflow:
- Prepare bootable USB media with Elcomsoft System Recovery on your computer (not the target computer).
- Boot the target computer from that USB media.
- In Elcomsoft System Recovery, specify the BestCrypt disk to extract encryption metadata from.
- Save the encryption metadata.
Once you are done, bring the extracted hash files to your computer and open them in Elcomsoft Distributed Password Recovery to set up the attack.
Step 3: Use Distributed Password Recovery to break the password
Launching an attack against a BestCrypt disk is as simple as opening the encryption metadata you obtained in Step 1 with Elcomsoft Distributed Password Recovery. However, you may want to modify the attack as opposed to using brute force.
While BestCrypt does its best to protect encrypted disks against GPU-accelerated attacks by choosing Script as a hash function, you can still use the power of distributed computing by splitting the task to multiple computers on the local network or over the Internet. We have significant advances in password recovery attacks. Breaking a password today involves the use of targeted dictionaries and smart attacks supported by Elcomsoft Distributed Password Recovery. The user’s existing passwords are an excellent starting point. These passwords can be pulled from the user’s Google Account, macOS, iOS or iCloud keychain, Microsoft Account, or simply extracted from the user’s computer. The user’s existing passwords give a hint at what character groups are likely used:
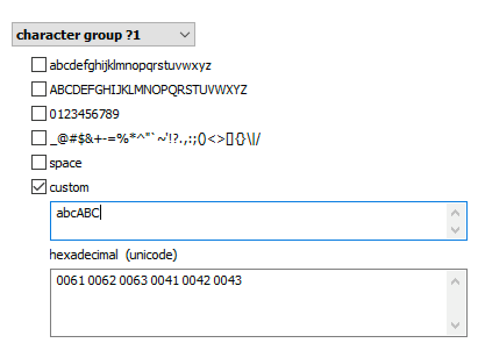
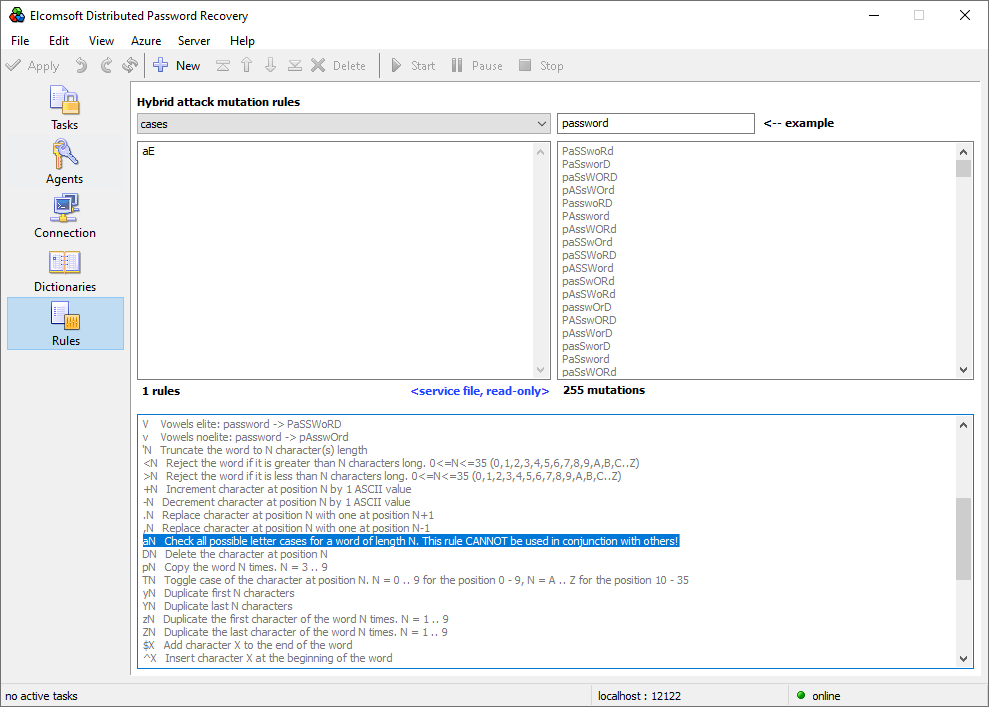
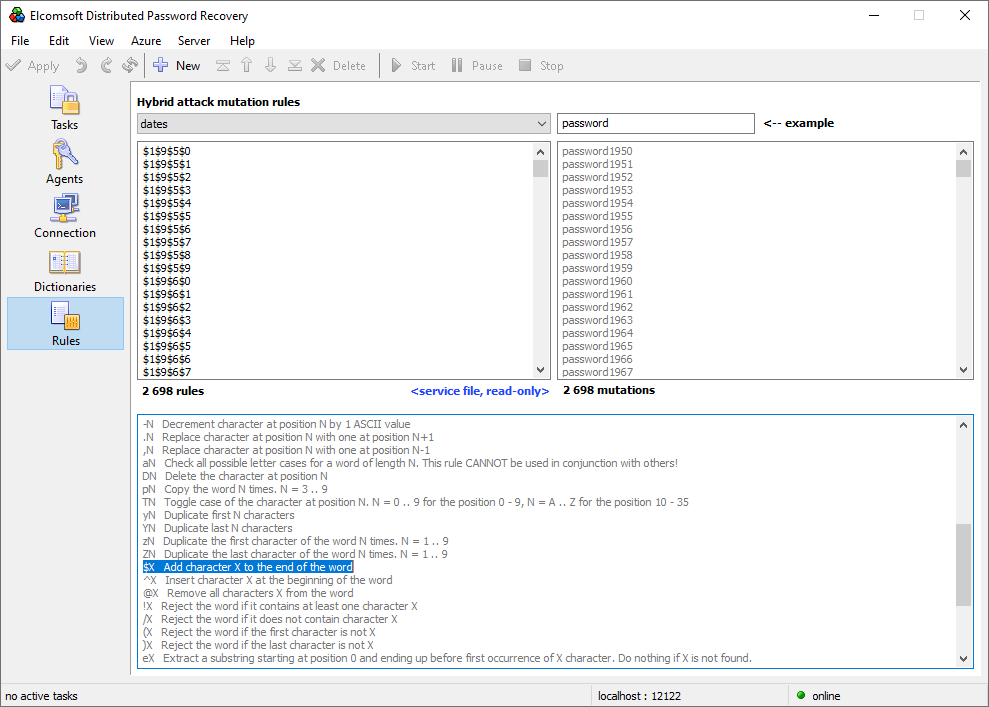
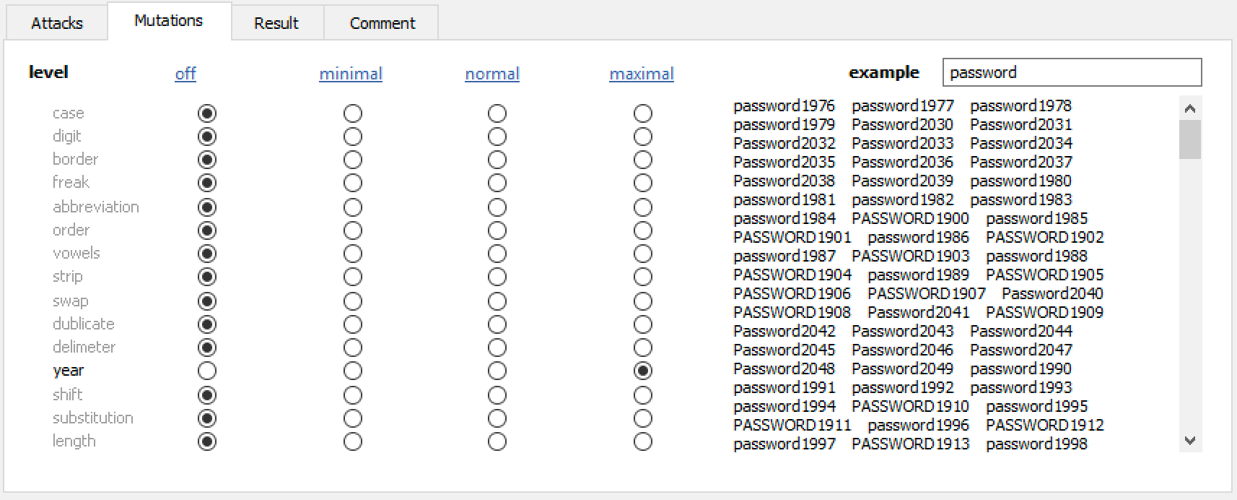
Elcomsoft Distributed Password Recovery offers a number of options to automatically try the most common variations of your password (such as the Password1, password1967 or pa$$w0rd):
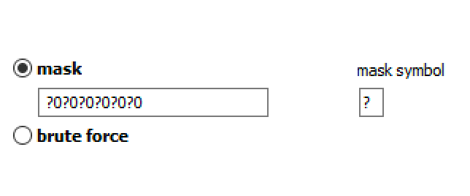
Masks can be used to try passwords matching established common patterns:
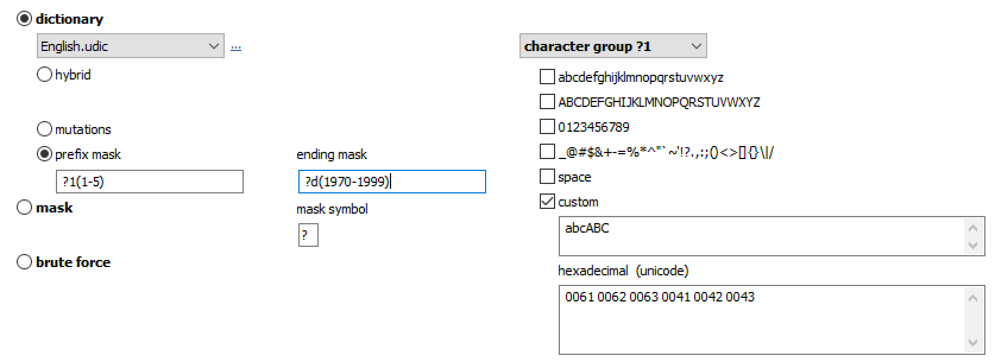
Advanced techniques allow composing passwords with up to two dictionaries and scriptable rules: