Legal Disclaimer
The information provided in this article is strictly for educational purposes. Therefore, you confirm that you are not going to use it to break into someone else’s Apple account. If you wish to apply ideas described in this article, you are taking full responsibility for your actions.
Non-Legal Disclaimer
Just relax. It’s not like we’re giving away tips on how to download celebrities’ photos or hack the prime minister’s iPhone.
If You Are The Rightful Owner
If you forget your very own Apple ID password, you can reset it at My Apple ID or by contacting Apple Support and verifying your identity.
The Danger of Buying Used iOS Devices
If, however, you purchased a device that is still linked to the previous owner’s account, all you can do is contact the previous owner as soon as possible and ask them to erase the device and remove it from their account. This is especially true if the phone’s Find My Phone option is activated and/or if the phone is in the Lost mode (this is often called the “iCloud lock”).
When purchasing a used iPhone, iPad, or iPod touch from someone other than Apple or an authorized Apple reseller, it is really up to you to ensure that the device has been erased and is no longer linked to the previous owner’s account. There is nothing you can do to unlock such a device. You can check the current Activation Lock status of a device by visiting icloud.com/activationlock.
Acquiring Apple ID Passwords from a PC (or Mac)
If you have access to the computer that was originally used to sync with the iOS device, there is a chance you might be able to retrieve the Apple ID and its corresponding password from that computer.
Password acquisition from a Mac computer. If an Apple account has been accessed from Mac, there is a good chance that the password is stored (cached) on that computer. Mac OS X stores cached passwords in the system’s secure storage called the keychain. To access the keychain, run the following:
[Applications] | [Utilities] | [Keychain Access]
Once there, filter all records by Apple ID by entering the email address in the top-right corner:
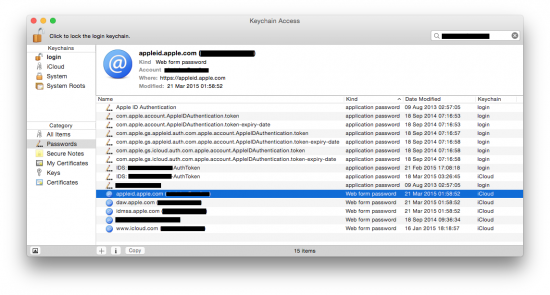
Many of the records contain will only contain authentication tokens that cannot be used to recover the original password. However, the password itself is sometimes present in other records. You will have to double-click on each and every item in the list to get more details:
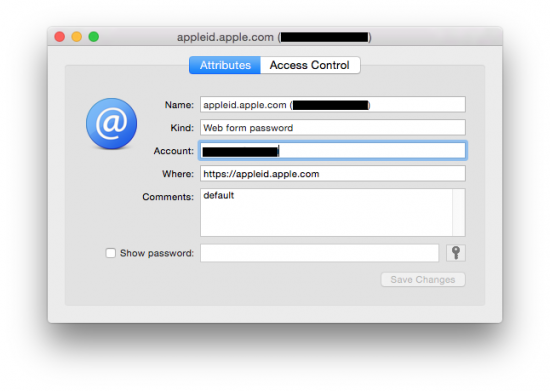
Check the Show password box (you will have to enter Mac login password), and the password (or some useless binary data) will be shown.
Password acquisition from a Windows computer. In Windows, there is no such thing as a free lunch keychain. You can only recover cached passwords stored in popular browsers such as Google Chrome, Mozilla Firefox, Internet Explorer or Opera. There are many free tools that can do that, e.g. ChromePass:
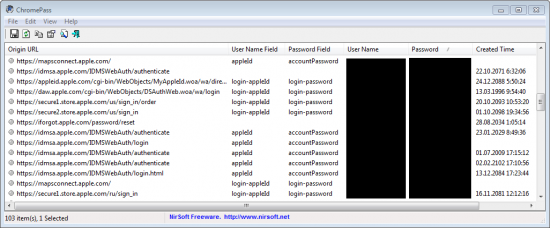
Note that, unlike on Mac OS X, you won’t even need a Windows password to retrieve cached form data. In Windows, cached passwords are not encrypted or secured in any way, just scrambled.
Password acquisition from an iOS device. In order to retrieve an Apple ID password from an iOS device such as an iPhone or iPad, you’ll either need the physical device or its encrypted backup (made with iTunes). It is really important that the backup is password-protected, and you know the password to that backup (if you don’t, use Elcomsoft Phone Breaker to recover).
In iOS, all passwords are also stored in the keychain (similar to MacOS X). The keychain is included with iTunes backups. However, if the backup password is not set, the keychain will be encrypted with the device’s unique hardware key, which is extremely difficult to obtain, especially for late iPhone/iPad models. In the meantime, if the backup is password-protected, the keychain is encrypted based on the key derived from the backup password. We won’t go deep into technical detail; more information is available here.
Anyway, once you have that password-protected backup, use the Explore keychain feature in Elcomsoft Phone Breaker (you will have to open the backup file and provide – or recover – the password). Here is what you get:
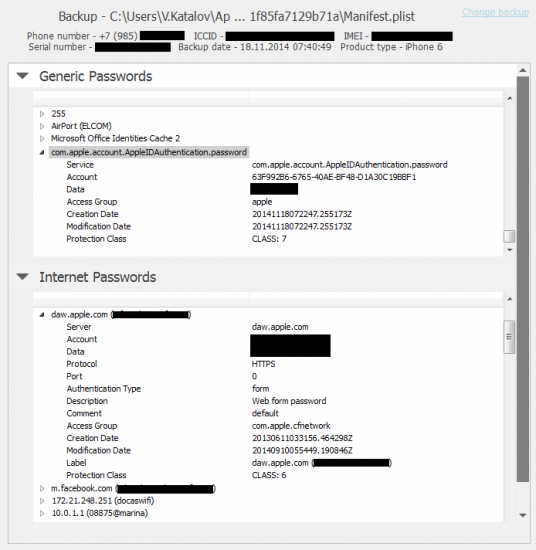
The iOS keychain consist of two groups: Generic Passwords and Internet Passwords. The first group contains passwords to Wi-Fi networks and different services. The second group includes passwords to mail accounts and Web sites including form autocomplete data.
In the Generic Passwords section, the data of interest are:
- apple.account.iTunesStore.password
- apple.account.AppleAccount.password
- apple.account.AppleIDAuthentication.password
Here is an example:
<item>
<Name>com.apple.account.AppleIDAuthentication.password (UUID)</Name
<Service>com.apple.account.AppleIDAuthentication.password</Service>
<Account>UUID</Account>
<Data>PASSWORD</Data>
<Access Group>apple</Access Group>
<Creation Date>20141118072247.255173Z</Creation Date>
<Modification Date>20141118072247.255173Z</Modification Date>
<Protection Class>CLASS: 7</Protection Class>
</item>
Note that no email address appears there; just the password.
In the Internet Passwords section, simply search for the Apple ID (by email). You will find several records that look like this:
<item>
<Name>daw.apple.com (EMAIL)</Name>
<Server>daw.apple.com</Server>
<Account>EMAIL</Account>
<Data>PASSWORD</Data>
<Protocol>HTTPS</Protocol>
<Port>0</Port>
<Authentication Type>form</Authentication Type>
<Description>Web form password</Description>
<Access Group>com.apple.cfnetwork</Access Group>
<Creation Date>20130611033155.507844Z</Creation Date>
<Modification Date>20130611033155.507844Z</Modification Date>
<Label>daw.apple.com (EMAIL)</Label>
<Protection Class>CLASS: 6</Protection Class>
</item>
Typically, you can find the password in the following records:
- daw.apple.com
- appleid.apple.com
- www.icloud.com
- idmsa.apple.com
- itunesconnect.apple.com
Sometimes the password is also listed in other records, e.g. those related to iMessage, FaceTime and some other services.
Please note that if the device has been reset, the keychain (as well as all other data) is completely lost, and cannot be recovered even theoretically.
How Hackers Get Your Passwords
Now, you’ve struggled enough to recover your very own password, but hackers don’t seem to have a problem breaking into people’s accounts. What do they do, exactly, and can you make use of their techniques while protecting yourself against them?
Phishing. This is the most common method to steal Apple ID passwords. You get an email pretending to be from Apple, with the subject reading (just a few examples):
- Apple/iCloud Profile Suspension
- Apple Account Blocked
- Apple & iCloud Cancellation
- Your Apple Cancellation
- Please confirm your apple account information
- Important Notice: Your last purchase with your Apple ID
- Your iTunes invoice #11209351958
- Your Apple ID was used to sign in to iCloud on an unknown device
In the email that can appear quite genuine (even including a warning to never enter your password on suspicious Web sites), you’re geared towards clicking on one of the links and signing in to your Apple account. Only problem, it’s not “your” account you’ll be signing into.
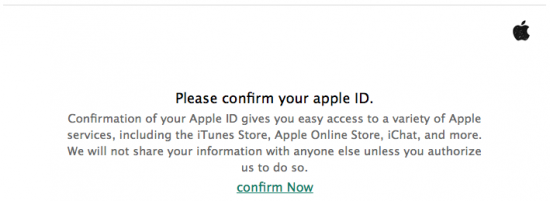
By clicking the link in this mail, you are transferred onto a Web site that looks exactly like the real thing, and asked to enter your Apple ID and password. Even the link in your Web browser may look “safe”, e.g. https://appleid.apple.signinserver5.com (not a real link). Note that the top-level domain name is not “appleid” or “apple” but some “signinserver5.com” (can be anything, really), while “apple” and “appleid” are its sub-domains. The Web site, of course, has nothing to do with Apple, and does nothing but collecting victims’ Apple IDs and passwords (for whatever purpose). In worst-case scenario, you may be asked to “update” or “confirm” your billing address and credit card number. Below is a list of articles on that issue:
Brute-force attacks. Most Apple services have effective protection against brute-forcing in place: an account is being locked if an incorrect password has been entered too many times (usually just three to five). However, we cannot say for sure that this is true for all services. Some time ago, researchers discovered that the Find My Phone service did not have that protection (now it does), then the same was found about the Game Center.
“Reverse” brute-force attacks. To avoid account locking mentioned above, hackers employ a different approach. Instead of attacking one account with many different passwords, they try just one password (from the list of the most popular ones) across many (thousands) Apple accounts. There is no single Apple account to lock in that case, and there is a good chance that at least a few accounts with that password will be found. If not, the hackers will try another password from their list on the same group of Apple accounts just a day or two after the first round.
Password reset/recovery. Sometimes it easier to break into the mailbox linked to a particular Apple account. By gaining access to victim’s mailbox, the hacker can reset the Apple ID password using the My Apple ID service. We have an article on that type of attack on our blog.
Keyloggers. A good old method that is hard to protect against. More info here.
Social engineering. Some people will tell their passwords if you just ask. Hard to believe? Here is the proof: What is Your Password? It is not always that simple, of course. Read the excellent Mitnick’s book The Art of Deception for more info.
Password re-use. If you use the same password to authenticate at least two different resources, you are at risk. Not all accounts and services are protected equally well. If just one account is compromised, we can consider that the other ones with the same password are cracked, too.
Password? What password? Did you know it is possible to get into iCloud without a password? In order to do that, one only needs an authentication token saved on your computer (PC or Mac) where iCloud Control Panel is installed.
How to Protect Yourself
Now when you know how an Apple ID password can be retrieved or hacked, let’s talk about how to protect oneself from common attacks.
Of course, the obvious recommendation could be “not using iCloud”. However, iCloud is just too much a convenience to dump. In addition, iCloud is not the only service related to Apple ID, so not using iCloud won’t do much in protecting your Apple ID.
You can go one step further, ditching your iPhone for a BlackBerry, Android, or Windows Phone device. If you’re really paranoid, you can even get a Nokia 8210 (especially if you are a drug dealer). But if you prefer to keep your lovely iPhone, keep reading.
Avoid phishing. Please review the following Apple articles first:
Ignore phishing emails. It is really easy to recognize phishing emails; you do not have to be security expert for it. Don’t ever click any link from an email asking you to log in to your account. If in doubt, just open your Web browser and type the correct link (e.g. apple.com). In addition, many email services (including Gmail and Hotmail) have really good spam and phishing filters that will automatically move many phishing emails to right where they belong: the Trash folder.
Think of physical security. As shown above, both your desktop and your iOS device may retain your Apple account password and/or authentication token. You can only blame yourself if you leave your computer unlocked and unattended, or set no passcode on the device.
Use a strong password. It may sound obvious, but many people are still using short and simple passwords that can be easily guessed. This is true for your desktop password, Apple ID password, and device passcode (though for the latest devices running the latest versions of iOS, even a simple 4-digit passcode is secure enough).
Enable two-step verification. While two-factor authentication is not a panacea, it still is a serious improvement. If enabled, anyone who wants to get into your account will also need to get your trusted device or recovery key, or steal an authentication token from one of your devices. This greatly reduces the number of people who can potentially steal your password.
We have mixed thoughts on two-step verification and some of its particular implementations. It is definitely not a panacea, and has a potential to create more risks. On a balance, it’s still an improvement.
The Risks
So what are the risks if someone steals your Apple ID password? In worst-case scenario, you’re doomed. We won’t quote horror stories from dubious sources. Instead, let’s review the official information from Apple itself:
Apple : Privacy : Government Information Requests
Follow the link “Legal Process Guidelines” (U.S. Law Enforcement; there are similar documents for IMEIA, Japan and APAC):
Legal Process Guidelines (U.S. Law Enforcement)
Pay the special attention to Information Available From Apple chapter. In brief, the data includes:
- Device registration information
- Customer service records
- iTunes information
- Apple retail store transactions
- Apple online store purchases
- iCloud
- Subscriber information
- Mail logs
- Email content
- Other iCloud content (incl. backups)
- Find My iPhone
Bear in mind that most of that information is available not just to law enforcement but to anyone who managed to get your Apple ID and password. You decide how sensitive this information is.
Theoretically, your account (i.e. your stored credit card) might be used to purchase iOS or Mac OS X software and even hardware. However, when they attempt to use a new device to make a purchase for the first time, they’ll have to confirm credit card data by entering the CVV code. Therefore, this risk is minimal (unless Apple happens to have a vulnerability to allow fooling the system so it thinks that the device is the same).
Finally, the password can be used to remove Activation Lock from your devices, making them more susceptible to theft.
Conclusion
In this article we reviewed some of the common methods and tools used to recover Apple ID passwords, covered methods and techniques used by malicious third-parties to break into users’ accounts, discussed methods to protect personal Apple accounts against unauthorized access and overviewed the risks associated with letting the Apple ID password slip away.
Activation Lock, Apple ID, Apple ID password, authentication token, Celebrities hack, Find My Phone, FindMyPhone, iCloud, iCloud password, iPhone, keychain, phishing, Social Engineering







