If you follow industry news, you already know about the release of iOS 9. You may also know that iOS 9 is the toughest one to break, with no jailbreak available now or in foreseeable future. With no jailbreak and no physical acquisition available for newer devices, what methods can you still use to obtain evidence from passcode-locked devices? Our answer to this is Elcomsoft Phone Breaker 5.0 that adds over-the-air acquisition support for iOS 9.
Phone Breaker 5.0
iOS 9 support, so what? Is that it? Does it justify bumping version number to 5.0? Yes, that’s it, and yes, we truly believe jumping the version number if fully justified. Let’s see why.
As you may already know, iOS 9 is pretty secure. In fact, it’s been a tough one to break since the very first public beta. While iOS 8.3 took a while to jailbreak, jailbreaking iOS 9 does little in the way of physical extraction (yes, we’re working on a physical acquisition tool for iOS 9, and no, we’re still not sure if such a tool is possible). As a matter of fact, iOS 9 has security improvements at all points. Apple even has a codename for this, referring to a specific subset of security technologies embedded into iOS 9 as ‘Rootless’.
If the device is locked with an unknown passcode, there is no way to make the locked device produce a local backup for further analysis. You can literally do nothing with the device unless you know the correct passcode.
If physical acquisition is not available, and if there is no possibility to make the device produce an offline backup, cloud forensics can be the last resort. Of course, iCloud extraction is not without its share of challenges, but what is?
Downloading device backups from the user’s iCloud account delivers almost as much information as a local backup, and does not require knowing the device passcode. (You do need to know the user’s Apple ID and password, or have access to a non-expired authentication token.) However, iOS 9 doesn’t make it simple.
Remember we said iOS 9 security was improved all around? The changes apply to iCloud as well. The location of iCloud device backups has been changed, with backups now stored in the user’s iCloud Drive account (as opposed to iCloud), which is no longer an optional upgrade. Despite that fact, cloud backups still cannot be accessed via iCloud Control Panel, and there is still no Apple tool available to download or manage backups via a PC or Mac.
Cloud backups now have a different structure, and feature notable changes and improvements to encryption. Finally, iOS 9 now has strict certificate checks all over the place, and introduces the new ATS (App Transport Security) protocol. These measures effectively put foot down on traffic sniffing and rule out man-in-the-middle attacks.
Developing iOS 9 Support
Before we go any further, let me explain what we do to develop iCloud acquisition support for a particular version of iOS. Normally, we would jailbreak an iPhone and replace certificates with our own, then sniff the traffic exchanged between the device and Apple’s servers, implementing a classic man-in-the-middle attack. Do you see a problem here? Certificates are strictly checked all over the place and cannot be replaced. The new ATS (App Transport Security) protocol is in place to combat man-in-the-middle attacks. It seems Apple specifically targeted the innocent developers such as us to make it harder making useful tools for their new OS.
Because of all these changes, we had to perform a tremendous amount of research, and believe me, this wasn’t the easiest or the most pleasant thing on Earth. But we did it.
iCloud for Windows Is Now Required
In previous versions, iCloud for Windows was not required to download iCloud backups. Prior to iOS 9, you would only need it if you wanted to download files from the cloud. iOS 9 changed that. You will now need to install iCloud for Windows from Apple Web site.
Cloud backups made with iOS 8.x remain visible and accessible to our tool even if iCloud for Windows is not installed. It’s the new iOS 9 backups that require the use of iCloud for Windows.
At this point, Elcomsoft Phone Breaker 5.0 runs on 32-bit and 64-bit Windows platforms up to and including Windows 10. We are working hard on making a Mac OS version available.
iCloud Backups: What’s Inside
Cloud backups are nothing new, yet they still are somewhat underestimated by the forensic crowd. Cloud backups offer users the convenience of being able to restore their usage experience on a new device to the look and feel of the original one. This includes typed passwords, cached Web forms, the content of the home screen, application data (again with cached passwords and authentication tokens), call and message logs, pictures and videos (including geotags), notes, books, and lots and lots of other data. In other words, the new device is restored to look, feel and work just like the original.
As many things Apple, iCloud backups are exemplary implemented. They are enabled with a simple toggle; from then on, the device will maintain incremental backups in the cloud by automatically transmitting new and updated information every time the device is connected to a known Wi-Fi network while sitting on a charger. This convenience and the fact that iCloud backups are enabled by default in new Apple devices running recent versions of iOS quickly made iCloud backups popular among Apple customers.
Retrieving and analyzing iCloud backups can help gain access to valuable evidence that may not be available elsewhere. If Apple ID and password are not known, or if there is no access to the secondary authentication factor (if two-step authentication is enabled on the account), law enforcement officials may be able to request the content of suspects’ iCloud backups by serving a warrant to Apple.
Downloading iCloud Backups
Downloading a cloud backup with Elcomsoft Phone Breaker is fairly simple. Just click “Tools” in the Password Recovery Wizard, and select “Download backup from iCloud”. If you don’t have an Apple ID and password but do have access to the computer that was synced with the cloud, try extracting the authentication token first, then using it in place of the login and password.
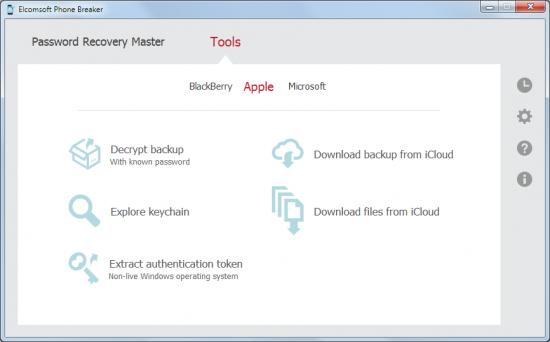
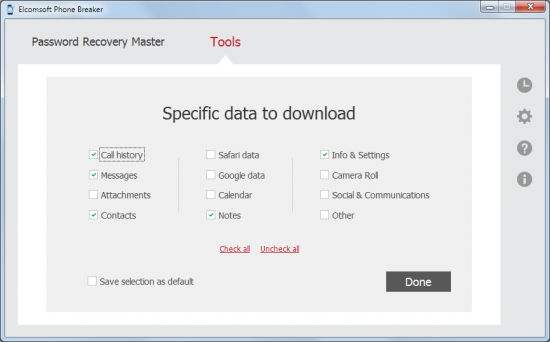
When downloading iCloud backups, you’ll have several options available. You can choose to download the full content of the backup (which may take a while depending on your connection speed and the speed of iCloud network), or you can opt for a much speedier selective download, picking the most important categories such as call logs, passwords or camera roll.
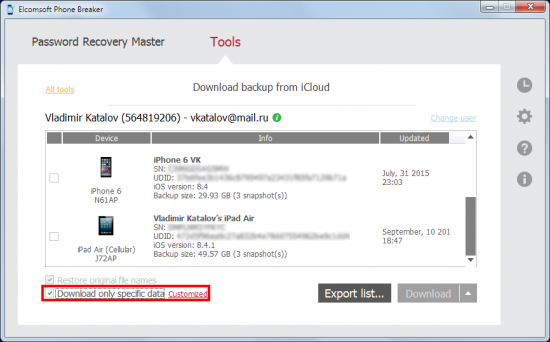
When performing the full download, you’ll be able to save the data in the iTunes format (for further analysis with commercially available forensic tools) or make Elcomsoft Phone Breaker re-create the original file and folder structure (for easier manual review). For selective downloading, only the second version is available.
Viewing iCloud Backups
Once downloaded, iCloud backups can be viewed or analyzed with one of the many forensic tools. If you just need to quickly browse through available data without learning how to use one of the more advanced analytic tools, consider using Elcomsoft Phone Viewer, a quick, easy and highly affordable viewer for mobile backups.
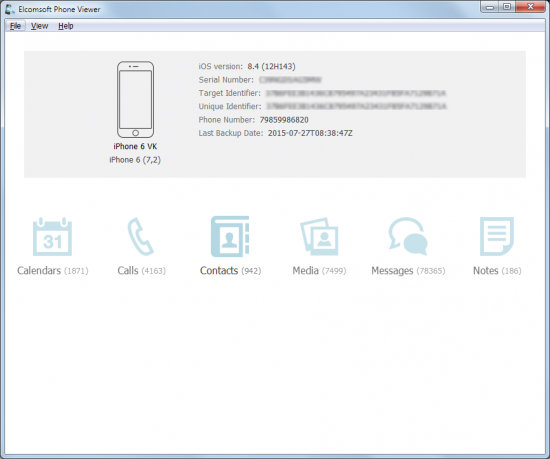
Using Elcomsoft Phone Viewer to view information downloaded from the cloud is easy. Simply launch the tool and open the backup, and you’ll see all available information sorted to appropriate categories. There are no fancy graphs and no advanced analytics, but searching are all there and they work blazing fast.
Note: new version of Elcomsoft Phone Viewer with iOS 9 support will be available in November’2015.
If You Don’t Know the Password
Downloading data from Apple iCloud requires to know the user’s Apple ID and password. But what if the password is not known? We covered this in one of our previous posts: Acquiring and Utilizing Apple ID Passwords, Mitigating the Risks and Protecting Personal Information.
In other words, you have a good chance of extracting the user’s password from their computer if you have access to said computer.
The First and Only (At Least for Now)
With no physical acquisition support (yet?) for the new iOS, over-the-air acquisition is possibly the last chance of obtaining information from passcode-protected Apple handsets. Elcomsoft Phone Breaker 5.0 becomes the first true stand-alone cloud acquisition solution for iOS 9. Our tool does not require a third-party server to operate, and never transmits your Apple ID and password to any server – except using them directly with Apple to authenticate an account. All communications occur strictly between your computer and Apple servers with no third parties involved. No single piece of information is ever transmitted to ElcomSoft or any servers other than Apple’s.
You will need the Professional or Forensic edition to perform iCloud acquisition. If you need two-factor authentication support and/or support for binary authentication tokens, you’ll have to get the Forensic edition. As a bonus, Forensic edition users will gain access to files stored in the user’s iCloud Drive account.
Unless you have a fresh, non-expired authentication token, you will still need to feed the tool with the correct Apple ID and Password, and you will still need access to the secondary authentication factor if two-step authentication is active for that Apple account.
Any (Free) Alternatives?
Are there any free alternatives to ElcomSoft iCloud acquisition tool? This question is often asked at forensic forums. While iCloud acquisition is available in some tools other than Elcomsoft Phone Breaker, all of them (with the exception of those using ElcomSoft engine) are based on iLoot, a Python-based open-source project. iLoot is far from perfect, but it does work – at least for older versions of iOS. However, iLoot development is apparently ceased due to the sheer amount of work and research required. iOS 9 support may come to other tools, but we don’t expect it to be any time soon.







