Two-step verification and two-factor authentication both aim to help users secure their Apple ID, adding a secondary authentication factor to strengthen security. While Apple ID and password are “something you know”, two-step verification (and two-factor authentication) are both based on “something you have”.
However, Apple doesn’t make it easy. Instead of using a single two-factor authentication solution (like Google), the company went for two different processes with similar usability and slightly different names. What are the differences between the two verification processes, and how do they affect mobile forensics? Let’s try to find out.
Before we begin, let’s look at Apple’s official documentation about the two verification methods.
Two-Step Verification
Long story short, two-step verification protects access to certain activities with users’ Apple ID since 2013. This method introduces an extra verification step in addition to the password. Generally speaking, the secondary verification step is required when signing into Apple ID or iCloud or making a purchase from a new device (more information is available in the Apple support article linked above). What’s important, however, is how Apple delivers codes that serve as the secondary authentication factor.
There are as many as four different methods that can be used to receive codes for two-factor authentication.
Delivery of secondary authentication codes:
- push notification to a trusted device
- text message or phone call to a registered number
- offline recovery key
- application-specific password
Enabling two-step verification:
- Two-step verification could be enabled from an Apple device…
- Or by signing in to My Apple ID.
Two-Factor Authentication
Apple views two-factor authentication (first released in 2015 with iOS 9) as an improvement over the previously used two-step verification. The new and improved security method is built directly into iOS 9 and OS X El Capitan, and cannot be used on devices running older versions of iOS. At this time, two-factor authentication availability is still limited to some regions; the method will roll out slowly to all regions.
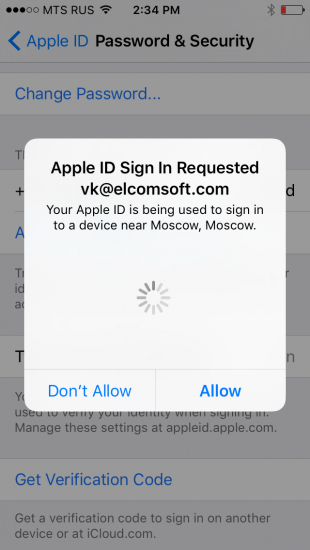
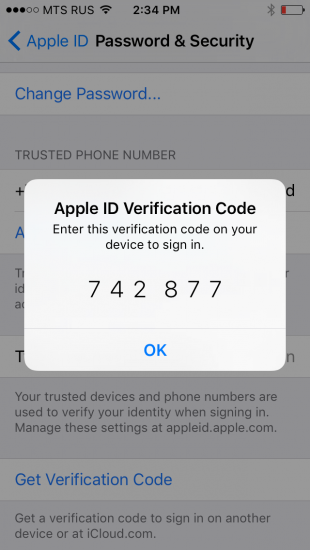
In this new authentication method, Apple ditched offline recovery keys and app-specific passwords.
Delivery of secondary authentication codes:
- push notification to a trusted device (interactive prompt appears on all trusted devices)
- text message or phone call to a registered number (via “Did not get a verification code?” prompt)
- NEW: no application-specific passwords; instead, Apple suggests appending a 6-digit authentication code to the original password (see below)
- NEW: offline, time-dependent code generated from the Settings of a trusted device
Enabling two-factor authentication:
- Two-factor authentication can ONLY be enabled from a compatible Apple device (iOS 9, El Capitan)
- If two-step verification is already enabled, it must be first disabled in order to enable two-factor authentication
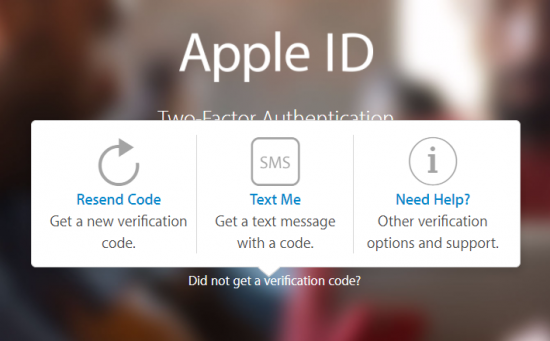
As you can see, it is now possible to generate and use authentication codes offline by requesting them from a trusted device:
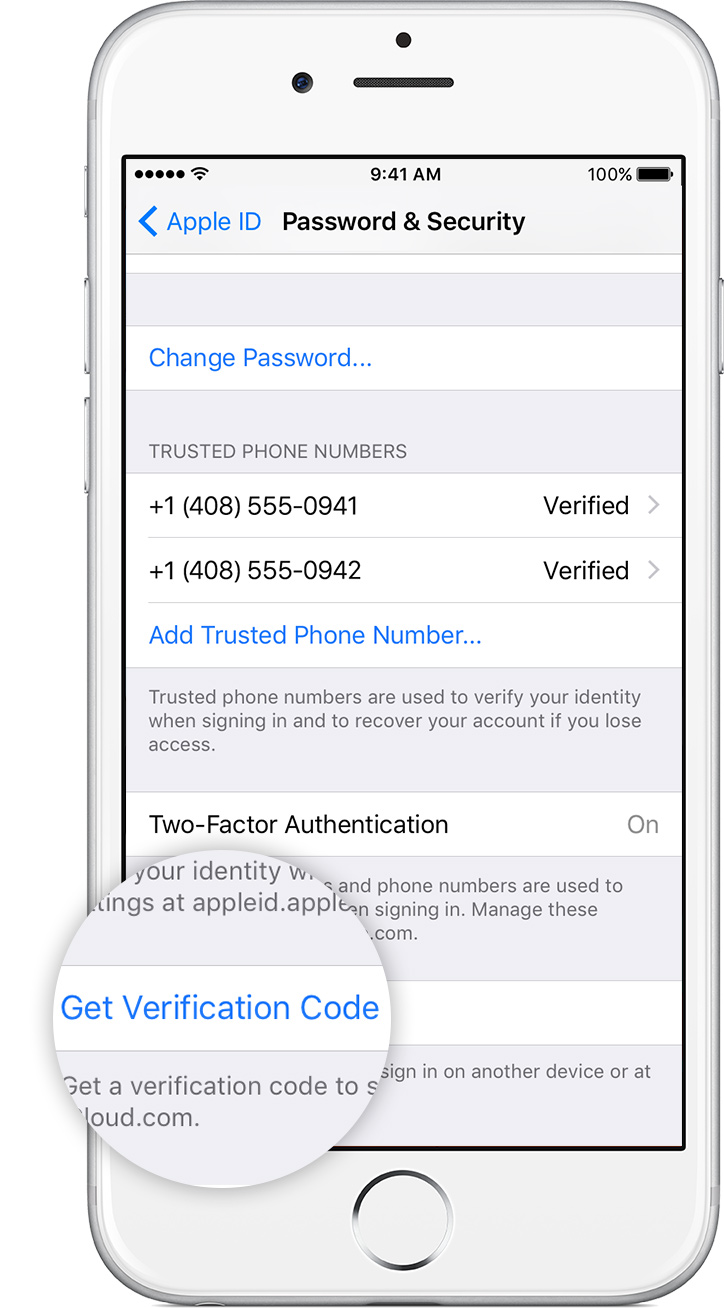
These offline authentication codes work similar to Google’s and Microsoft’s implementations, meaning that a new code is generated every 30 seconds. Unlike Google’s and Microsoft’s authenticator apps, Apple uses a unique seed for each trusted device, meaning that each trusted device generates a unique authentication code. This, however, means that users can revoke 2FA authorization from each individual device (as opposed to Google’s or Microsoft’s approach that invalidates all Authenticator apps initialized with a certain seed).
2FA: No App-Specific Passwords
In addition to Recovery Keys, Apple ditched app-specific passwords. When activating two-factor authentication, users who have at least one device without support for 2FA (such as an iPhone with iOS 8 or older) will see the following prompt:
Some of your devices are not ready for two-factor authentication. If you continue you will have to add a six-digit verification code to the end of your password any time you enter password on an old device
We tested this, and received a somewhat confusing result. The first time we tried making an App Store purchase from an iPhone 5C running iOS 8.3, we were prompted to enter the password with a 6-digit code appended at the end. A trusted device displayed the prompt and the code. However, when we tried to use that phone to make a purchase on the next day, the regular Apple ID password worked. We did not have to attach the 6-digit code. However, our trusted device still displayed the prompt and the code – yet we didn’t have to use it. We’ll continue investigating the issue.
One more thing that’s new with two-factor authentication is what happens when one loses access to all of their trusted devices (and registered phone numbers).
If this is the case, one will need to make a request to Apple to regain access to Apple ID with two-factor authentication account recovery:
https://support.apple.com/en-us/HT204921
Using Elcomsoft Phone Breaker with Two-Step Verification and Two-Factor Authentication
If you’re using Elcomsoft Phone Breaker to acquire iOS backups from Apple iCloud, and if that Apple ID is protected with either two-step verification or two-factor authentication, you will need access to the secondary authentication factor in order to be able to download the data. If two-factor authentication is enabled on a given Apple ID, Elcomsoft Phone Breaker will automatically prompt to enter the secondary authentication code.
Elcomsoft Phone Breaker and 2SV/2FA:
- The current release of Elcomsoft Phone Breaker fully supports 2SV. It automatically prompts for a verification code if it detects that 2SV is active.
- For Apple accounts protected with 2FA, you’ll have to manually generate a 2FA code on a trusted device, then append the 6-digit 2FA code to the end of the original password when authenticating EPB. We are working on an update with full 2FA support.
When using Elcomsoft Phone Breaker with accounts protected with either 2SV or 2FA, please note the following:
- You cannot use an app-specific password to download iCloud backups
- If the device being acquired runs iOS 8.x or earlier, it can only use two-step verification (and not two-factor authentication). However, if the user has at least one device that supports 2FA, they may have enabled 2FA on their Apple ID despite the fact that a given device is not compatible.
- At this time, if two-factor authentication is enabled for a given Apple ID, you’ll have to manually generate a 6-digit authentication code on a trusted device. When authenticating Elcomsoft Phone Breaker, you’ll have to append that six-digit code to the end of the password.
- If you’re acquiring a backup from an account protected with two-factor authentication (iOS 9 and newer) while using a 2FA code generated offline from the trusted device’s Settings, be aware that such codes are short-lived. You can only use them for authentication during the first 30 minutes after they’ve been generated.
- Finally, if you don’t have access to the secondary authentication factor, you may still be able to access cloud backups by using a binary authentication token acquired from a computer with iCloud Control Panel (iCloud for Windows) signed in. Note that these tokens don’t seem to expire for iOS 9 backups that are stored in iCloud Drive, but tend to expire quickly for iOS 8.x and earlier backups that are stored in the “classic” iCloud.
At this time, we are actively working on implementing full support for Apple’s two-factor authentication into Elcomsoft Phone Breaker. The upcoming release will be able to automatically detect accounts with 2FA enabled, prompting for a 2FA code and saving an authentication token to bypass 2FA the next time you use it.







