Biometric approach to unlocking portable electronics has been on the rise since late 2013 when Apple released iPhone 5S. Ever since, manufacturers started adding fingerprint scanners to their devices. In the world of Android, this was frequently done without paying much (if any) attention to actual security. So how do these systems compare?
Apple iOS: Individually Matched Touch ID, Secure Enclave at Work
Apple invented Touch ID to increase the average user security. The idea behind fingerprint unlock is for users who had no passcode at all to use Touch ID. Fingerprint data is stored on the Secure Enclave, and is never transferred to Apple servers or iCloud.
Apple Touch ID is an integrated complex of hardware and software components facilitating the use of a fingerprint to quickly unlock iPhones and iPads equipped with fingerprint readers. Touch ID is available on iPhone 5S, 6/6Plus and iPhone SE; iPad mini 3 and 4; iPad Air 2, and both iPads Pro.
Touch ID is deeply integrated into iOS devices. Each fingerprint reader is individually paired with the rest of the system at the factory. Since iOS 9, iPhone users who had their Touch ID fingerprint reader replaced by a third party would be unable to use fingerprint unlock feature. During initial iOS 9 roll-out, these users experienced Error 53, an error message that effectively bricked iPhones with fingerprint sensors replaced by a third party. This was fixed later with an iOS update; however, Touch ID remains disabled if the fingerprint sensor is not correctly paired with Secure Enclave.
Apple treats Touch very seriously. In recent iPhone generations (iPhone 6S and 6S Plus), using Touch ID to unlock the phone is truly instant: Touch ID unlocks the phone just as quickly and reliably as if the device was never locked.
Touch ID Security
Touch ID is not bulletproof. Fingerprint readers found in early devices (iPhone 5S) could be fooled rather easily. The system became significantly more secure in iPhone 6/6 Plus, and further improved in iPhone 6S/6S Plus. For this reason, Apple limits the use and lifespan of fingerprint unlock in an attempt to reduce the possibility of a malicious attacker successfully exploiting Touch ID.
If your device is rebooted or power-toggled, Touch ID can only be used after the phone is successfully unlocked with a passcode. Until then, user data (such as Wi-Fi passwords as well as the entire data partition) remains securely encrypted. Unlocking the phone with a passcode enables subsequent unlocks with Touch ID. However, Touch ID expires if the phone is rebooted or has not been unlocked for 48 hours (update: can be 8 hours if passcode unlock wasn’t used during the last 6 days). This feature is meant to reduce the time a malicious user has to attempt circumventing the fingerprint scanner.
This has recently changed, with additional rules imposed on Touch ID to further reduce the possibility of fooling the fingerprint reader.
Today, Touch ID expires (and the user must unlock the device with a passcode instead of their fingerprint) if any of the following conditions is met:
- The device is rebooted or power cycled
- A new finger is added to Touch ID
- A lock command is issued from Find My iPhone
- 5 straight unsuccessful login attempts with Touch ID
- The device hasn’t been unlocked in 48 hours
- New: The device hasn’t been unlocked with a passcode in 6 days AND it hasn’t been unlocked with Touch ID in 8 hours
PhoneArena speculates that “…the last rule could have an impact on law enforcement.” It continues, “This year there have been a spate of cases involving locked iPhone units that the FBI or local police needed to have unlocked while searching for evidence. In the case of the Apple iPhone 5c belonging to San Bernardino shooter Syed Farook, Apple ignored a court order forcing them to unlock the device, saying that it could not open the handset without developing a special version of iOS dubbed Govt.OS. Eventually, the government was forced to pay a third party to unlock the device.”
Acquisition Steps
As you now know, Touch ID can expire quickly. In order to be able to use Touch ID to unlock the phone, you must act fast before it expires. We recommend the following acquisition steps:
- When seizing a locked device, put it into a Faraday bag and connect to a charger. This will prevent the device from switching off due to low power.
- When seizing an unlocked device, go to Settings and disable automatic lock:
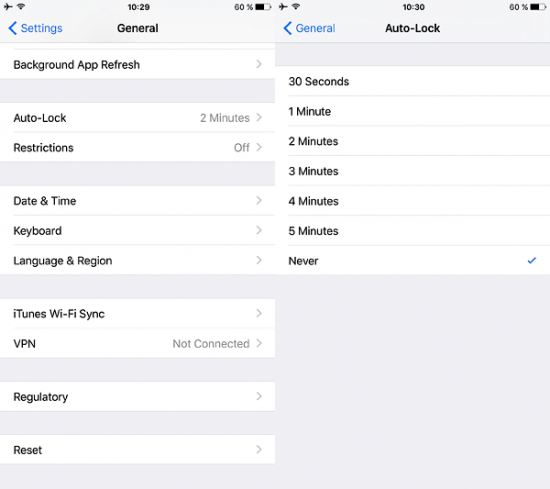
- From now on, you have 48 hours or less to make the suspect unlock the device.
- Never allow the device leave wireless-shielded environment even while making the suspect unlock it. Connecting to a cellular data network takes seconds; receiving a remote erase command (Find My Phone) can be nearly instant.
- Once the device is unlocked, configure it to never lock automatically (see p.2).
- Note that you won’t be able to add another fingerprint, change or remove the passcode without entering the correct passcode in the first place.
The Role of Touch ID in iPhone Acquisition
When it comes to mobile forensics, is Touch ID a curse or a blessing? Courts are on the edge of approving a legislation allowing the police to force suspects unlock their iPhones with a fingerprint (as opposed to forcing the suspect to unlock with something they know, aka passcode). But does a successful Touch ID unlock really help during an investigation?
Understanding the role of Touch ID and how it affects forensic acquisition of iOS devices is extremely important. What can and what cannot be done to an iPhone (or iPad) unlocked with Touch ID?
- Physical acquisition: NO. For physical acquisition with Elcomsoft iOS Forensic Toolkit to work on 64-bit iPhones, the device must be unlocked AND the passcode must be removed from the settings (which requires entering the correct passcode).
- Limited physical acquisition: YES. Even if you don’t remove the passcode, Elcomsoft iOS Forens ic Toolkit can still extract a limited amount of data from the device via the “TAR FILES” command.
- Cloud backups: YES. Devices unlocked with Touch ID can be forced to produce a fresh cloud backup via Settings – iCloud – Backup – Backup now.
- iTunes backups (logical acquisition): YES. Devices unlocked with Touch ID can be forced to produce a local backup (via iTunes). Note, however, that if the user set a password to protect iTunes backups, you will not be able to remove that password without specifying it first. If this is the case, use Elcomsoft Phone Breaker to attack and recover the backup password and to decrypt the backup.
Our Take
Apple’s implementation of fingerprint unlock is exemplary. While false positives and false negatives are natural for all consumer biometric authentication techniques, Apple has taken every possible step to minimize their impact on end-user security. If you have an iOS device equipped with Touch ID, we can absolutely recommend using this technology.
The use of Touch ID in law enforcement is limited to logical acquisition and partial physical acquisition (which extracts very limited amounts of data unless you remove the passcode from the settings). However, unlocking the device with Touch ID is way better and offers far greater possibilities compared to dealing with a locked device.



