In our previous blog post, we wrote everything we know about authentication tokens and Anisette data, which might allow you to bypass the “login, password and two-factor authentication” sequence. Let us have a look at how you can actually extract those tokens from a trusted computer and use them on a different computer to access a user’s iCloud account. Read Part 1 and Part 2 of the series.
Extracting Authentication Tokens from a Live System (Windows)
Extracting authentication token from a live system is as easy as running a small, stand-alone executable file you get as part of the Elcomsoft Phone Breaker package. The tool is called ATEX (atex.exe on Windows), and stands for Authentication Token Extractor.
Using the tool is extremely simple. Make sure you are logged on under the user you’re about to extract the token from, and launch ATEX with no arguments. The file named “icloud_token_<timestamp>.txt” will be created in the same folder where you launch the tool from (or C:\Users\<user_name>\AppData\Local\Temp if there are not enough permissions).
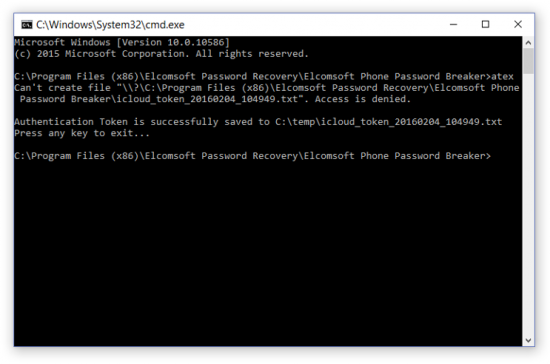
The full path to the extracted file will be displayed in the console window. The resulting file with .txt extension contains the Apple ID of the current iCloud control panel user and its authentication token .
Extracting Authentication Tokens from Disk Images or Other Users (Windows)
While extracting an authentication token from the currently logged in user on a live system is a one-click affair, obtaining one from a forensic disk image or just from another user is significantly more complex.
The reason for this is the fact that authentication tokens are not stored in the system in plain text. Instead, they are encrypted, and you’ll have to provide path to the decryption key in order to make use of these tokens.
For extracting the token from the disk image (or another user on the same system), you’ll have to use Elcomsoft Phone Breaker.
First, open the tool and navigate to Tools – Apple, then use Extract Authentication Token.
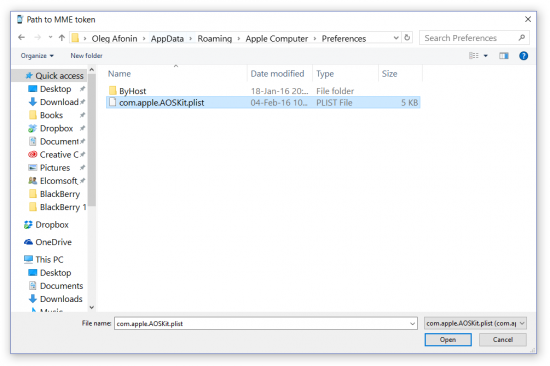
When prompted, provide path to the token file:
Then you will have to provide path to the user’s Master Key:
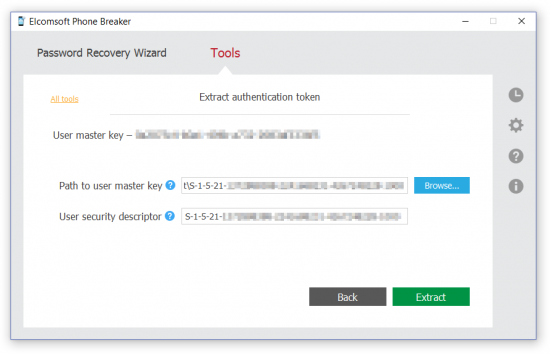
After that, the token will be extracted and decrypted. You will be able to use it with EPB:
Note: detailed information about extracting authentication tokens is provided in Elcomsoft Phone Breaker user’s manual.
Extracting Authentication Tokens from macOS (Live)
In macOS, the authentication tokens are stored in the keychain. Let’s have a look at how to extract the keychain from.
You can use Elcomsoft Phone Breaker to extract the token. If you are able to access the live system with the user currently logged on, extracting macOS keychain is as easy as launching the ATEX tool:
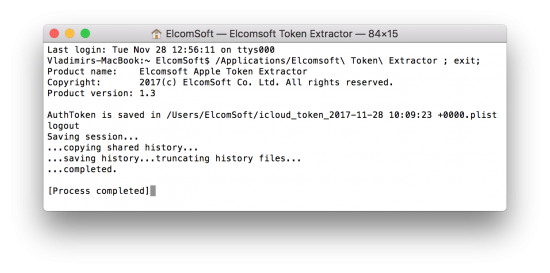
The iCloud authentication token is stored in the resulting .plist file.
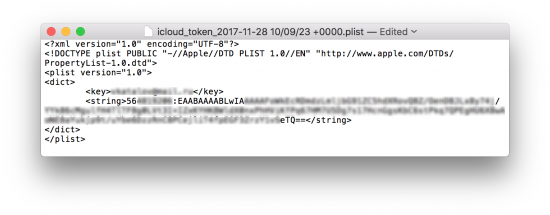
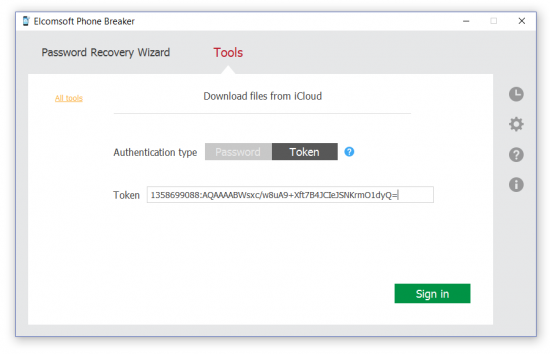
Copy the binary data and use in Elcomsoft Phone Breaker to access cloud data.
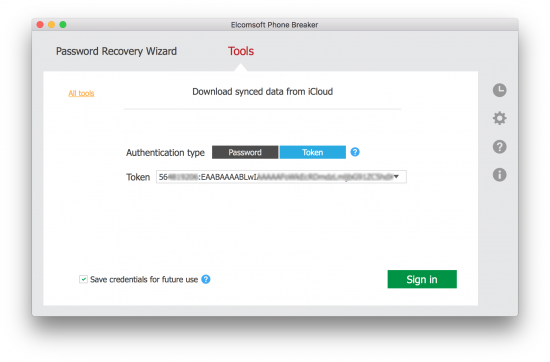
Extracting Authentication Tokens from macOS (Offline)
Extracting an iCloud authentication token from a disk image is a bit more complex.
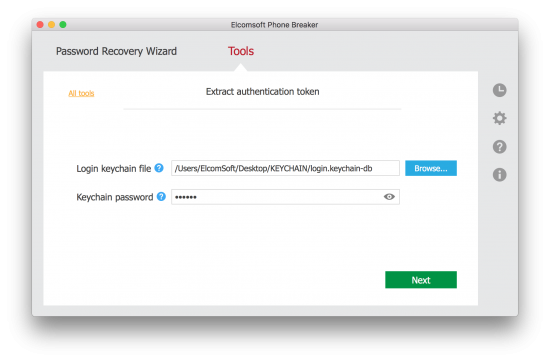
In Elcomsoft Phone Breaker, use Tools – Extract Authentication Token command. Provide path to the login keychain (it is stored under /Users/username/Desktop/Keychain/login.keychain-db in macOS Sierra and newer; in older versions of macOS, the file name was login.keychain) and enter keychain password to decrypt. Note that the keychain password is usually (but not always) the same as the user’s login password for a given account.
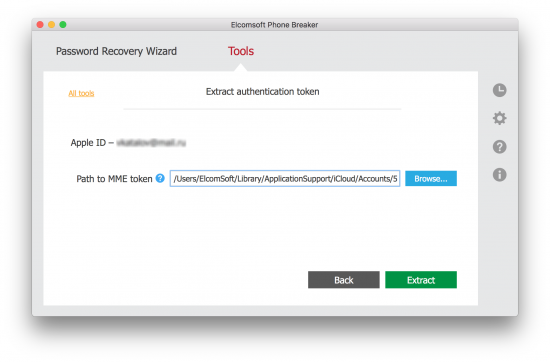
The next step is providing path to the MME token:
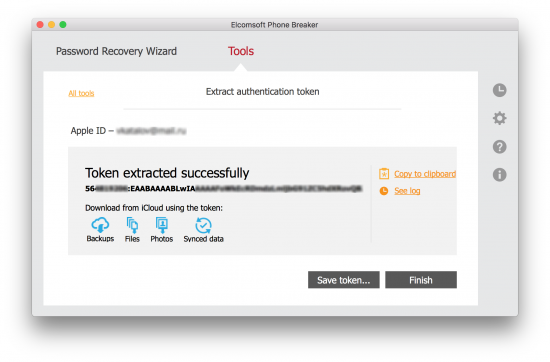
Then finally the token is extracted:
Extracting Authentication Tokens from iOS System Backups
Did you know you can also extract iCloud authentication tokens from iOS system backups? In order to extract an authentication token from an iOS system backup, you will need all of the following:
- A local (iTunes) iOS backup protected with a password (if the password is empty, you must set a temporary password before making a backup)
- DSID of the Apple account you are obtaining the token for
- Elcomsoft Phone Breaker
In order to access authentication tokens, you’ll be using the Keychain Explorer function of Elcomsoft Phone Breaker. To access Keychain Explorer:
- Launch Elcomsoft Phone Breaker
- Tools – Apple – Keychain Explorer
- Provide path to the password-protected backup
- Enter the password to decrypt the keychain
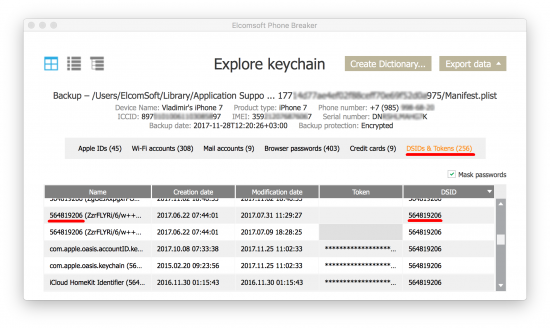
You will see the following window:
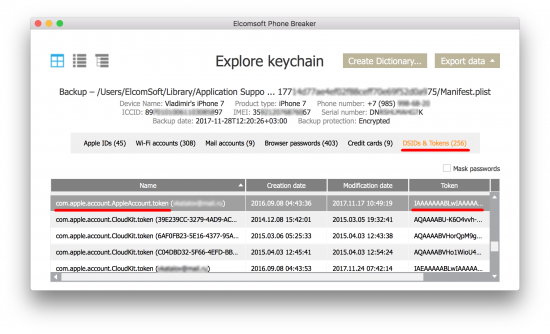
The very first tab (Apple IDs) contains all sources known to us that may contain the user’s Apple ID password as well as authentication tokens. Try copying iCloud-related tokens and using them in Elcomsoft Phone Breaker to authenticate!
Note that you will also need to provide a so-called DSID, which is Apple’s internal representation of the user’s Apple ID. You can get the DSID here:
Conclusion
This article concludes the short series of blog posts about authentication tokens. You should now know how to extract and use these tokens to access information stored in the user’s iCloud account.















