We loved what Apple used to do about security. During the past years, the company managed to build a complete, multi-layer system to secure its hardware and software ecosystem and protect its customers against common threats. Granted, the system was not without its flaws (most notably, the obligatory use of a trusted phone number – think SS7 vulnerability – for the purpose of two-factor authentication), but overall it was still the most secure mobile ecosystem on the market.
Not anymore. The release of iOS 11, which we praised in the past for the new S.O.S. mode and the requirement to enter a passcode in order to establish trust with a new computer, also made a number of other changes under the hood that we have recently discovered. Each and every one of these changes was aimed at making the user’s life easier (as in “more convenience”), and each came with a small trade off in security. Combined together, these seemingly small changes made devastating synergy, effectively stripping each and every protection layer off the previously secure system. Today, only one thing is protecting your data, your iOS device and all other Apple devices you have registered on your Apple account.
The passcode. This is all that’s left of iOS security in iOS 11. If the attacker has your iPhone and your passcode is compromised, you lose your data; your passwords to third-party online accounts; your Apple ID password (and obviously the second authentication factor is not a problem). Finally, you lose access to all other Apple devices that are registered with your Apple ID; they can be wiped or locked remotely. All that, and more, just because of one passcode and stripped-down security in iOS 11.
So What’s the Big Deal?
If you are working in a sensitive environment, is front door security all you need to secure a building? Don’t you need additional checks or e-keys to enter some rooms? This no longer applies to iOS. Once you have a passcode, you then have access to everything. Let us have a look at what you can do to the user and their data once you have their i-device and know their passcode.
The iTunes Backup Password
Imagine you’re working for a company whose main business is breaking passwords. iPhone backups one can make with Apple iTunes or third-party apps such as iOS Forensic Toolkit can be protected with a password. That password is strong or very strong depending on the version of iOS. Your company builds better software, while Apple makes backup passwords even more secure. In the end, Apple seemingly wins the race: breaking those passwords now requires a powerful computer (or multiple computers) equipped with high-end video cards, but even then, you cannot try more than handful passwords per second.
Then Apple makes a sudden twist, allowing anyone to simply reset that highly secure password. That’s what they did in iOS 11. If you have access to the device and know its passcode, you will no longer need to perform lengthy attacks. Just go ahead and remove that password.
Why is this important? Before I tell you that, let us look at how it used to be in iOS 8, 9 and 10.
Backup Passwords in iOS 8, 9 and 10
In these versions of iOS, one could protect their backups by specifying a backup password in iTunes. One would only need to do it once. Once a password was set, all future backups made on that computer and any other computer, with no exceptions, would be protected with that password:
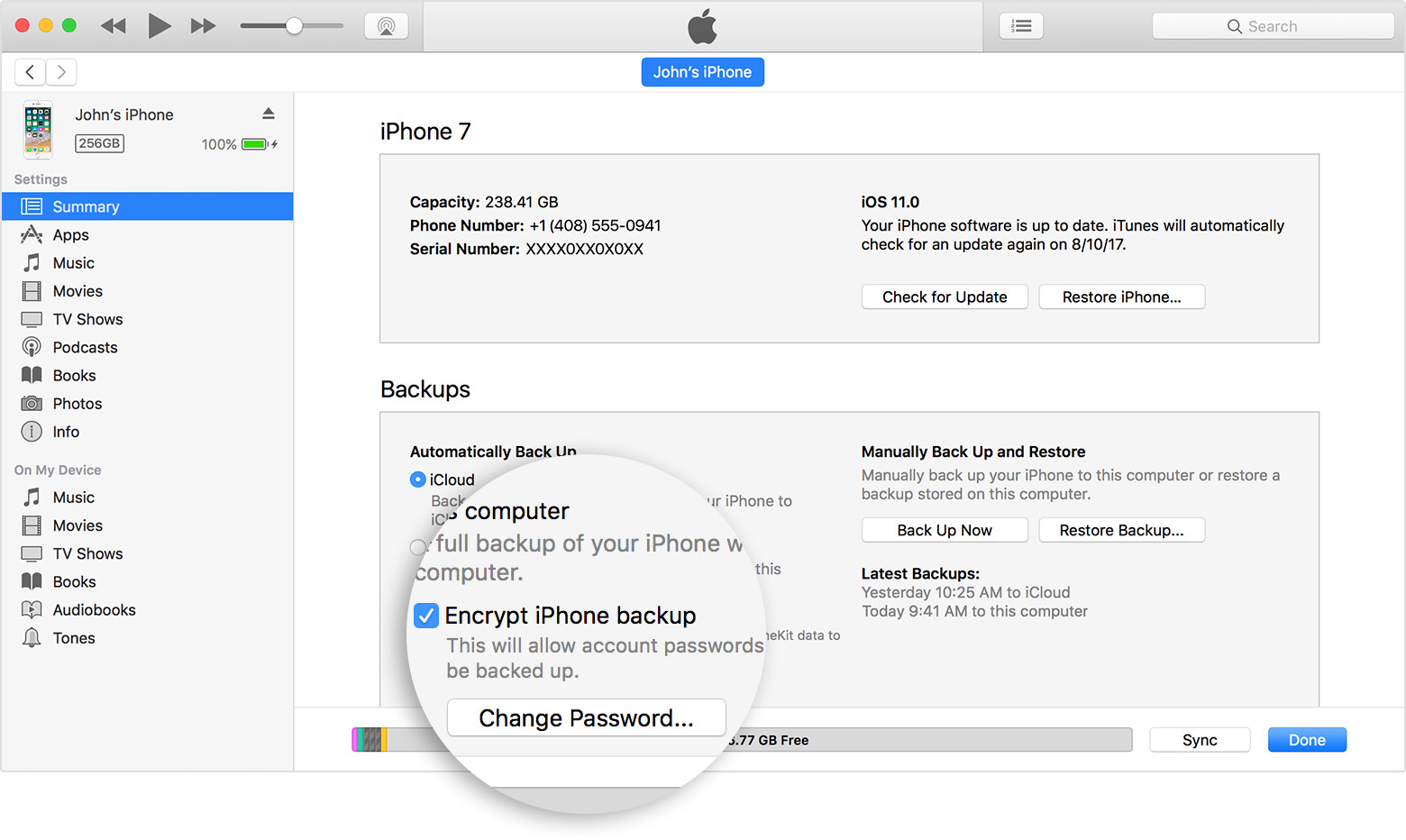
The password would become the property of the i-device and not the PC (or the copy of iTunes) that was used to set the password. You could connect your phone to a different computer and make a local backup with a freshly installed copy of iTunes, and that backup would still be protected with the password you set a long time ago.
Any attempt to change or remove that password must pass through iOS, which would require to provide the old password first. Forgot the original password? There’s no going back, you’re stuck with what you have unless you are willing to factory reset the device and lose all data in the process.
If you ask me, this was a perfect and carefully thought through solution. Want to protect your data against an attacker? Set a long and complex backup password and don’t store it anywhere. Forgot that password? You can still make a cloud backup and restore your phone from that backup; even your passwords (keychain) would be restored if you rolled out the cloud backup onto the same device you made the backup from (or used iCloud Keychain if that was to be a different device).
A perfect system? Apparently, it was not to everyone’s liking. The users whined. The police complained. The FBI complained. And Apple gave up.
iOS 11: Stripping Backup Passwords
In iOS 11 you can still specify a backup password in iTunes, and you still cannot change or reset it through iTunes if you don’t know the original password. However, this means very little as you can now easily remove that password from iOS settings.
This is what Apple has to say in its Knowledge Base:
You can’t restore an encrypted backup without its password. With iOS 11 or later, you can make a new encrypted backup of your device by resetting the password. Here’s what to do:
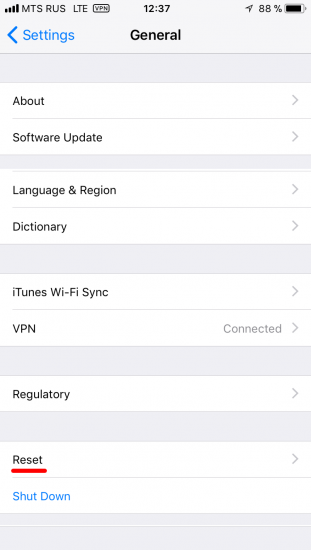
- On your iOS device, go to Settings > General > Reset.
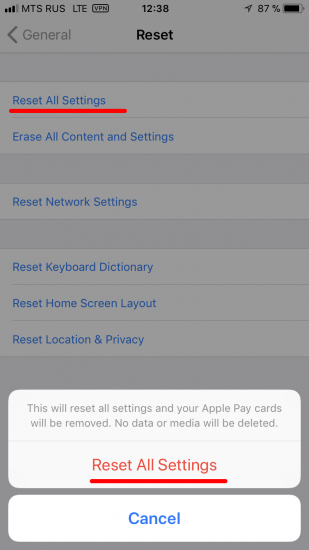
- Tap Reset All Settings and enter your iOS passcode.
- Follow the steps to reset your settings. This won’t affect your user data or passwords, but it will reset settings like display brightness, Home screen layout, and wallpaper. It also removes your encrypted backup password.
- Connect your device to iTunes again and create a new encrypted backup.
You won’t be able to use previous encrypted backups, but you can back up your current data using iTunes and setting a new backup password.
If you have a device with iOS 10 or earlier, you can’t reset the password.
You’ll be looking for these settings:
and
That’s it? That’s it. You have just removed the backup password. You can now make a new backup or, rather, extract information from the device. Don’t rush and make sure to specify a temporary password (“123” always works) before you make that backup. A password-protected backup will allow you decrypting the user’s passwords, credit card data, health data and other things that would be otherwise inaccessible.
So, set a temporary password, make that backup, decrypt it with Elcomsoft Phone Breaker or just use Keychain Explorer (a tool in Elcomsoft Phone Breaker) to access that user’s passwords, authentication tokens, credit card numbers and other interesting things. Oh, and their pictures, too.
Passwords:
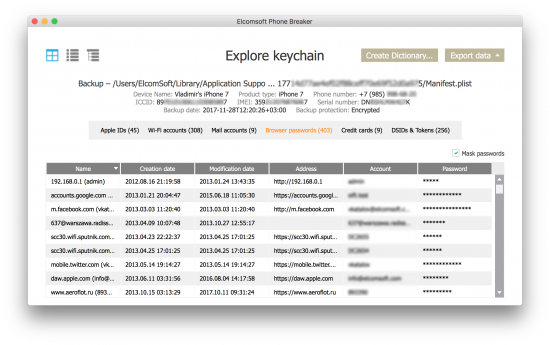
While there, look for their Google Account password. If it is there in the keychain (and I don’t see why not), you’ll gain access to a whole lot of highly interesting information including several years worth of precise location data, all passwords they saved in Chrome, Google Photos, bookmarks, Google search history and a log more. Two-factor authentication? I bet it’s that SIM card or Google Prompt on the iPhone in your hands.
What if you don’t have any photos in the backup? Check in the iOS Settings app whether iCloud Photo Library is enabled in iCloud account – Sync – Photos. If it is, the photos are synced with iCloud and are not included in local or cloud backups. Simply switching this feature off makes it possible to back up the photos into a local backup.
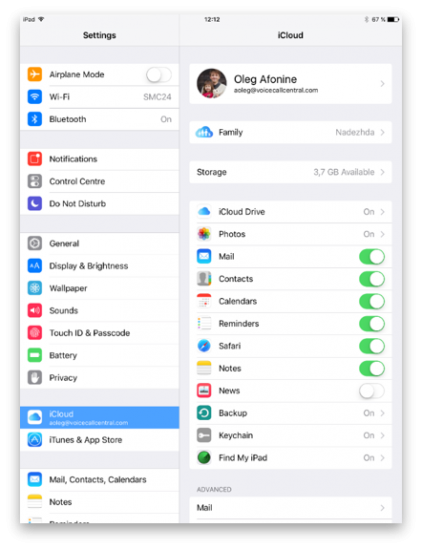
What if the iPhone in question runs an earlier version of iOS that does not allow removing backup passwords? I say you’re lucky because you can simply update that device to iOS 11 and then reset that password. We tried this strategy multiple times, and not once did we have an issue.
What if the device simply cannot run iOS 11, like that iPhone 5c from San-Bernardino? If this is the case, your best bet is attempting to jailbreak that iPhone. 32-bit devices (iPhone 4s, 5, and 5c) allow for complete physical acquisition (including the keychain). Just note that we are talking about the situation when the passcode is known, though that was not the case in San-Bernardino.
With access to just an iPhone and its passcode, you have already gained access to all of the following:
- Everything contained in a local backup (with a password)
- Passwords and tokens from the local keychain
- Local pictures and videos
- Application data (mostly SQLite)
This alone is massive, but that was just the beginning. You can do more; in fact, a lot more. What if I say you can now change the user’s Apple ID password, remove iCloud lock, remotely lock and/or erase user’s other devices and make sure they can never get back control over their account?
Changing Apple ID Password and Removing iCloud Lock
Normally, changing an account password requires confirming the old password first. In some cases, one could reset a password by receiving a one-time password reset link to a trusted address. This is about the same for the Big Three (Apple, Google and Microsoft) if you do it through the browser.
But (and this is a very important “but”) Apple has its own way. For Apple accounts with two-factor authentication, one can simply reset their Apple ID password from the device by confirming their device passcode (as opposed to supplying their old Apple ID password).
What does that mean in practice? If you have someone’s iPhone, and you happen to know or can recover the passcode (solutions allowing to brute-force device passcodes are available on the market), you can do the following:
- Change the user’s Apple ID password
- Remove iCloud lock (then reset and re-activate the iPhone on another account)
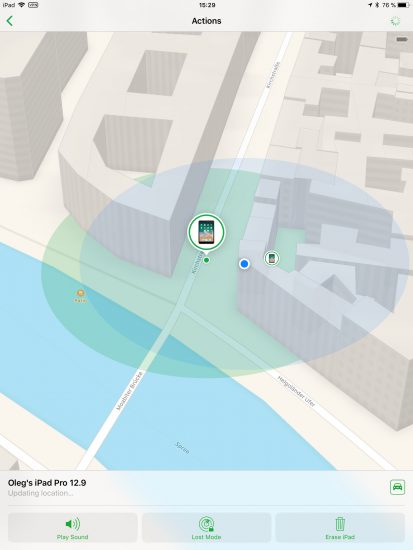
- Discover physical location of their other devices registered on the same Apple account
- Remotely lock or erase those devices
- Replace original user’s trusted phone number (from then on, you’ll be receiving that user’s 2FA codes to your own SIM card)
- Access everything stored in the user’s iCloud account
So how do you reset the user’s Apple account / iCloud password? For that, we’ll use the preinstalled Find My Phone app (reminder: this is going to work on 2FA-enabled accounts only):
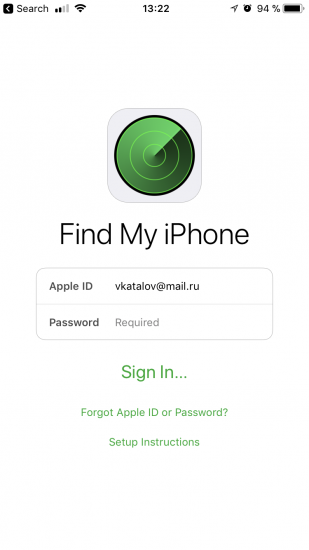
From there, tap “Forgot Apple ID or password?” The app will prompt for device passcode:
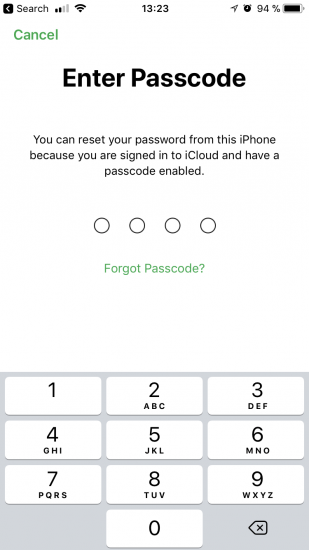
Enter the passcode. During the next step, enter and confirm a new Apple ID password (same as iCloud password):
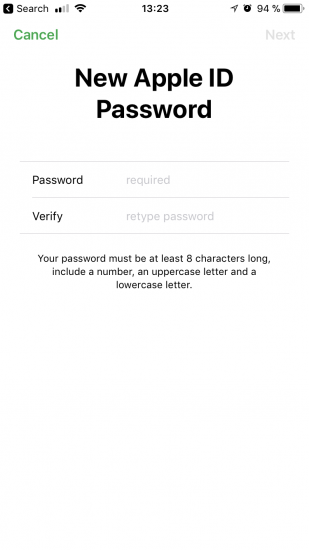
It’s that simple. You were never prompted to enter the original Apple account password; device passcode was enough to reset account password.
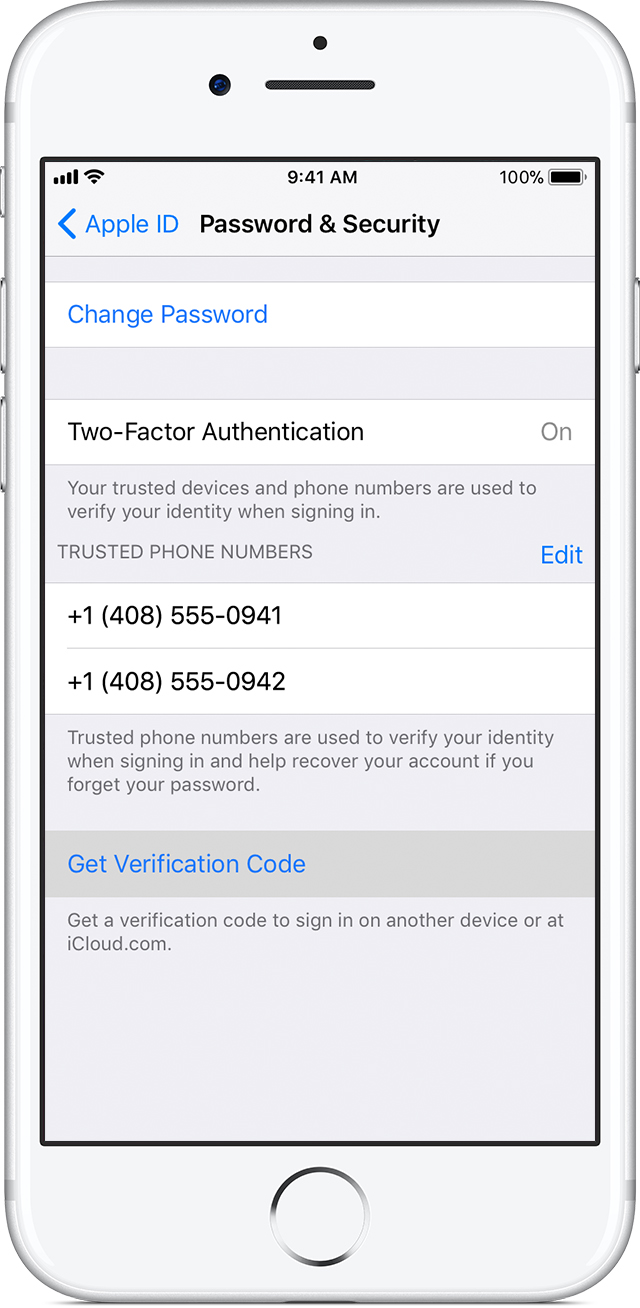
Is this a bug in the Find My Phone app? Absolutely not! You can do the same even without using the app. Open the Settings app on the user’s iPhone, and open the user’s Apple ID settings. From there, open Password & Security:
Tap Change Password. You will be prompted for device passcode:
Then you’ll be able to change the password to iCloud / Apple ID:
In fact, you can do even more from the Settings app compared to Find My Phone. In addition to account password, you can also replace the user’s Trusted Phone Number with your own phone number, making it insanely difficult for the ex-owner to regain control over now-yours Apple account. In order to replace the trusted phone number, first add and confirm a new trusted number; then you can remove the old one.
At this point, removing iCloud lock (the very lock that protects iOS devices from theft) it as easy as switching off Find My iPhone and typing your newly created Apple ID password.
Accessing iCloud Account
Access to iCloud data (backups, synced data, iCloud Photos and stored passwords) is normally securely protected. In order to access that data you would need a login and password (and access to the second authentication factor).
Wait! We’ve just reset the user’s iCloud password, and we’ve just added a new phone number to receive one-time codes! This means we can easily access everything the user has in their Apple account, including iCloud backups, photos taken on all of their devices, their iCloud Keychain, contacts, call logs, and a lot more.
iCloud Backups
We wrote about iCloud backups many times before. In a word, Apple may store up to three last backups per device. If the user has multiple iOS devices registered on the same Apple ID, up to 3 cloud backups will be available for each device.
By resetting the iCloud password, you’ve just opened the possibility to access those backups. All you need is the user’s Apple ID, your newly reset password, and one-time code to pass two-factor authentication.
Use Elcomsoft Phone Breaker to download backups. [Tools] | [Apple] | [Download from iCloud] | [Backups].
The backup will be downloaded and saved in the iTunes format. You can view its content with Elcomsoft Phone Viewer or other forensic tools.
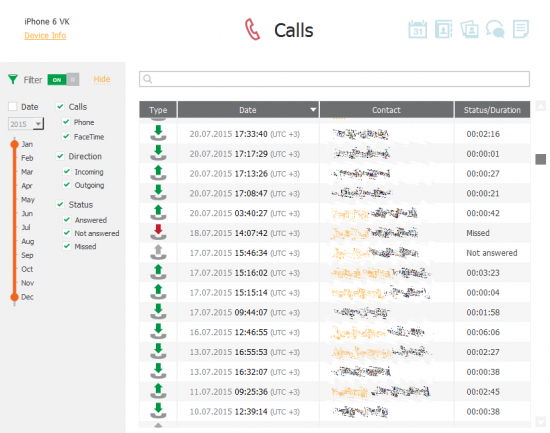
Call Logs, Files and Synced Data
iCloud is a lot more than just backups. Apple devices use iCloud to sync information such as browser bookmarks and open tabs, Web browsing history, contacts, notes, call logs, and even passwords. This information is collected and synchronized across all devices registered on the same Apple account.
Extracting synced data is simple. Just use Elcomsoft Phone Breaker to download, and Elcomsoft Phone Viewer to analyse.
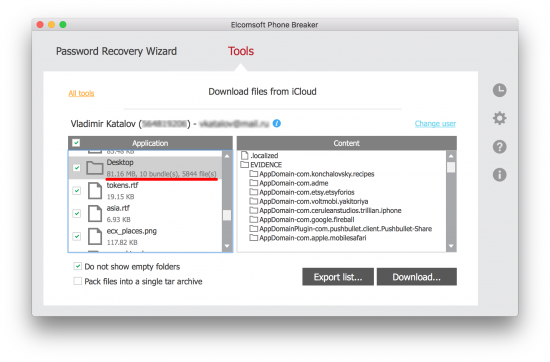
What if the user has a Mac? We can then access Documents and Desktop files synced by that Mac with iCloud Drive! Use Elcomsoft Phone Breaker: [Tools] | [Apple] | [Download from iCloud] | [iCloud Drive] to obtain those files. Finally, as an added bonus, you may be able to extract the user’s FileVault2 recovery key (if the user allowed cloud recovery, that is).
The Passwords: iCloud Keychain
iCloud Keychain is a cloud service for synchronizing Safari passwords, authentication tokens and payment information across iOS devices. After changing iCloud password and assuming you know device passcode (and this, for the purpose of this article, is a given), you can easily download those passwords.
Step 1: in Elcomsoft Phone Breaker click [Tool] | [Apple] | [Download from iCloud] | [Keychain]
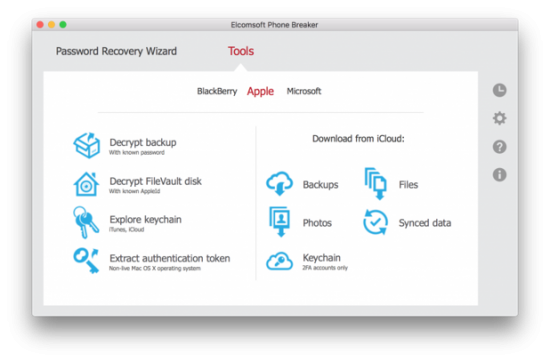
Step 2: use login, password and 2FA code to log in to iCloud
Step 3: select a trusted device from the list (this must be the device that you know the passcode to) and enter its passcode into the Device passcode box
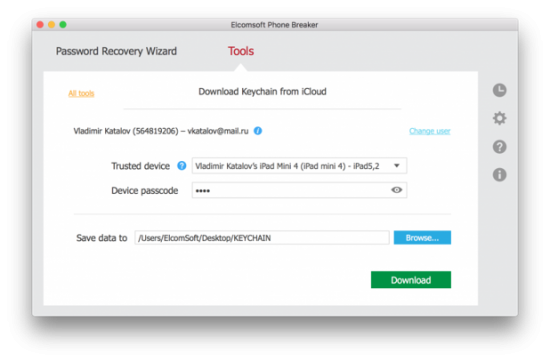
Step 4: the iCloud Keychain will be downloaded. You can now go back to the main window and open Keychain Explorer to access those passwords. By the way, you will now have access to the original (old) password to the user’s Apple ID account, as well as (possibly) passwords and tokens to that user’s other Apple ID accounts, if there are any. In addition, you may also see passwords to email accounts and Wi-Fi networks, as well as pretty much every password the user typed in Safaru.
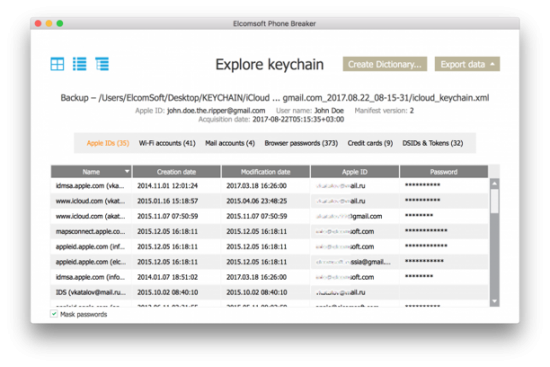
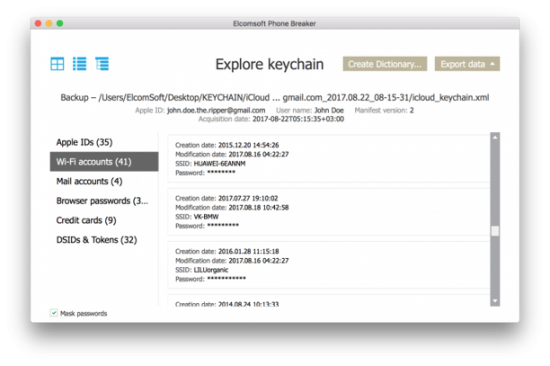
Conclusion
With the release of iOS 11, Apple developers made too many assumptions, breaking the fragile security/convenience balance and shifting it heavily onto convenience side.
Once an intruder gains access to the user’s iPhone and knows (or recovers) the passcode, there is no single extra layer of protection left. Everything (and I mean, everything) is now completely exposed. Local backups, the keychain, iCloud lock, Apple account password, cloud backups and photos, passwords from the iCloud Keychain, call logs, location data, browsing history, browser tabs and even the user’s original Apple ID password are quickly exposed. The intruder gains control over the user’s other Apple devices registered on the same Apple account, having the ability to remotely erase or lock those devices. Finally, regaining control over hijacked account is made difficult as even the trusted phone number can be replaced.
This is just scary. Why Apple decided to get rid of the system that used to deliver a seemingly perfect balance between security and convenience is beyond us.
If you don’t think this is a big issue, just one word for you: celebgate. Obviously, the victims had a password protecting their accounts, and yet that was not enough to stop hackers from stealing their photos. This is what the second protection layer is for as delivered by two-factor authentication. What I am saying is: once they have your iPhone and your passcode, you are no longer in control of their device and their Apple account.
What can you do to protect yourself? Since the passcode is now the one and only safeguard left, make sure you use at least 6 digits. Four-digit PINs are no longer secure. Other than that, we’ll just wait and see if Apple can fix it.






















