Extracting the fullest amount of information from the iPhone, which includes a file system image and decrypted keychain records, often requires installing a jailbreak. Even though forensically sound acquisition methods that work without jailbreaking do exist, they may not be available depending on the tools you use. A particular combination of iOS hardware and software may also render those tools ineffective, requiring a fallback to jailbreak. Today, the two most popular and most reliable jailbreaks are checkra1n and unc0ver. How do they fare against each other, and when would you want to use each?
About checkra1n
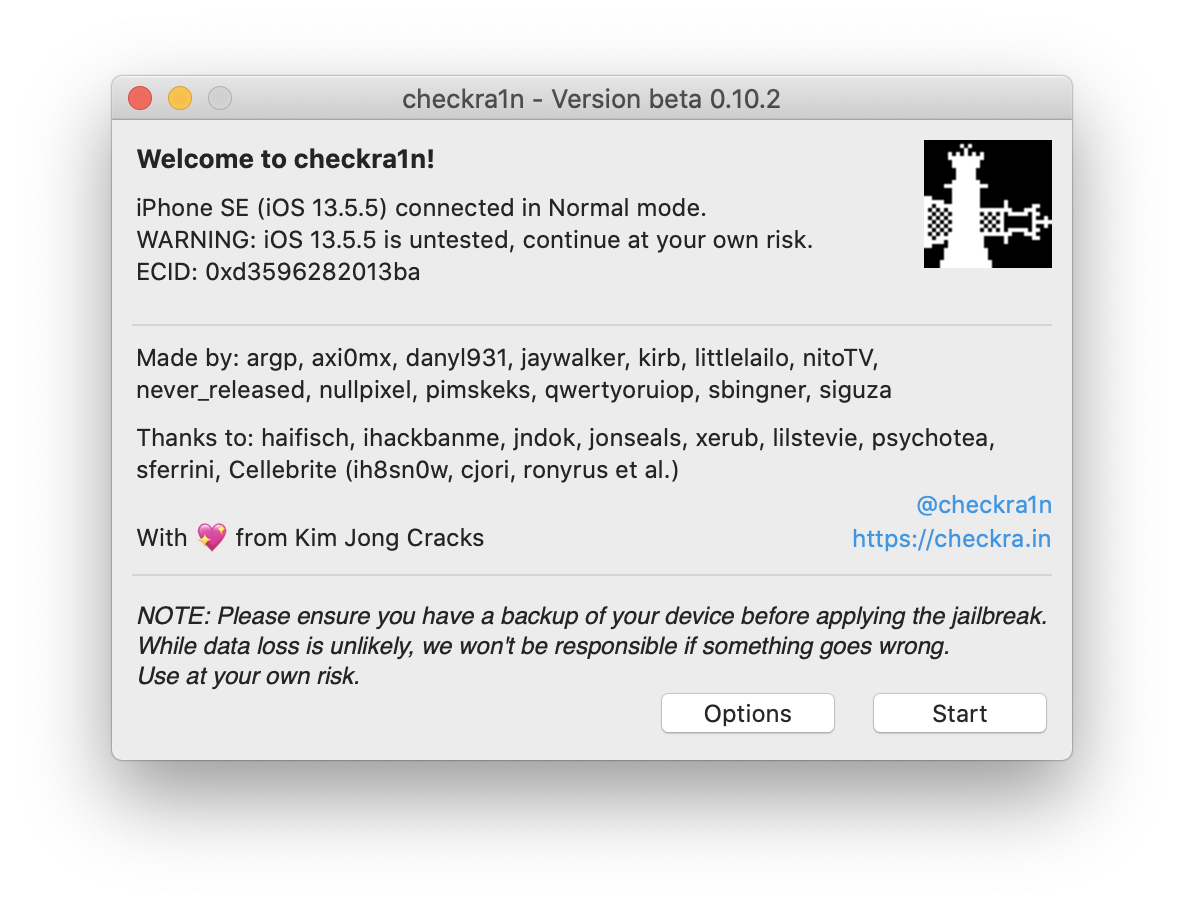
The chechra1n jailbreak is based on checkm8, which is a hardware-based exploit. There is no way for Apple to fix the vulnerability, so it is going to stay forever in all affected models.
- Affected device models: iPhone 5s, 6, 6 Plus, 7, 7 Plus, 8, 8 Plus, iPhone X
- Affected versions iOS: iOS 12.3 to iOS 13.5.5 beta
- Pros: will work with future versions of iOS; can be used for locked and disabled devices
- Cons: limited set of devices supported; does not work with iOS 12.2 and lower
About unc0ver
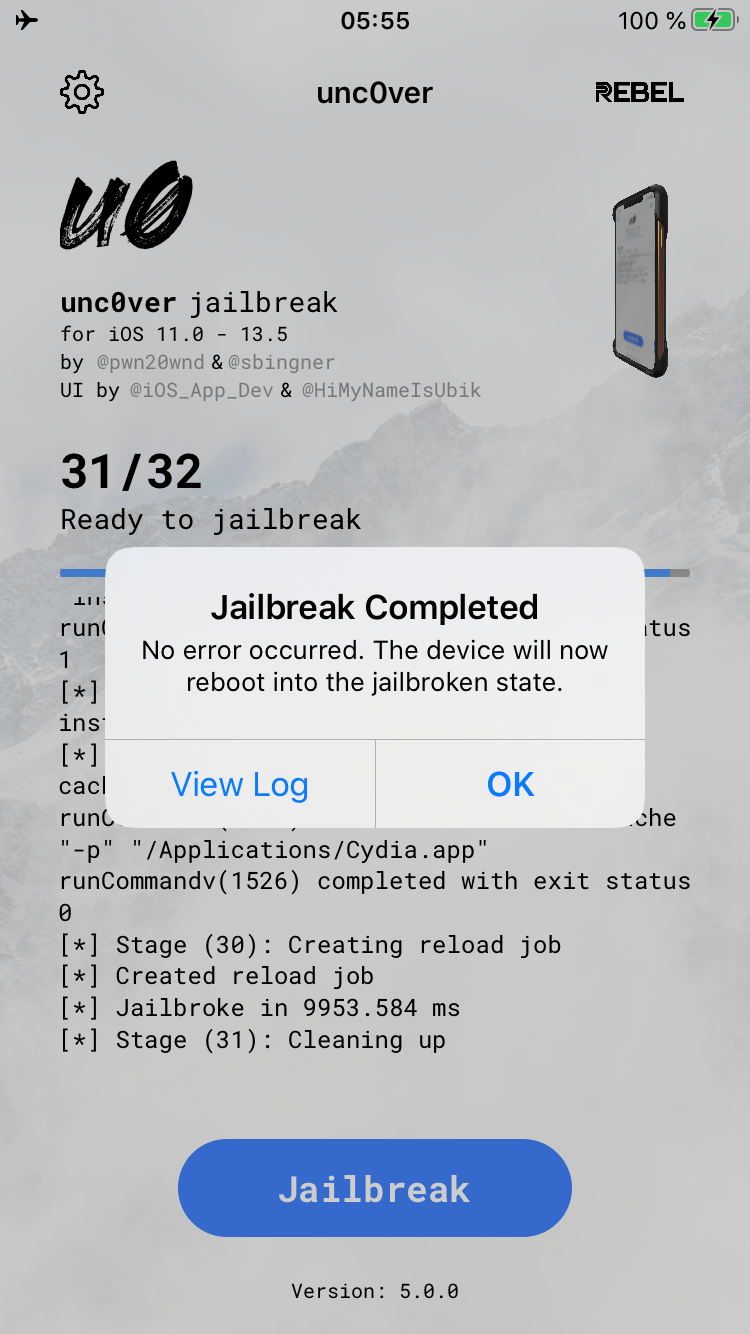
The Unc0ver jailbreak is completely different. It is based on software exploits that are currently available for most versions of iOS up to iOS 13.5.
- Affected device models: iPhone 5s to iPhone 11 Pro Max and iPhone SE 2 (2020)
- Affected versions of iOS: iOS 11.0 to iOS 13.5
- Pros: stable; compatible with all iOS 11 and iOS 12 versions; compatible with the latest Apple devices (iPhone 11, iPhone SE 2020)
- Cons: does not work with iOS 13.5.1 and 13.5.5 beta; not future-proof; underlying exploits can and will be fixed by Apple
Agent-based acquisition
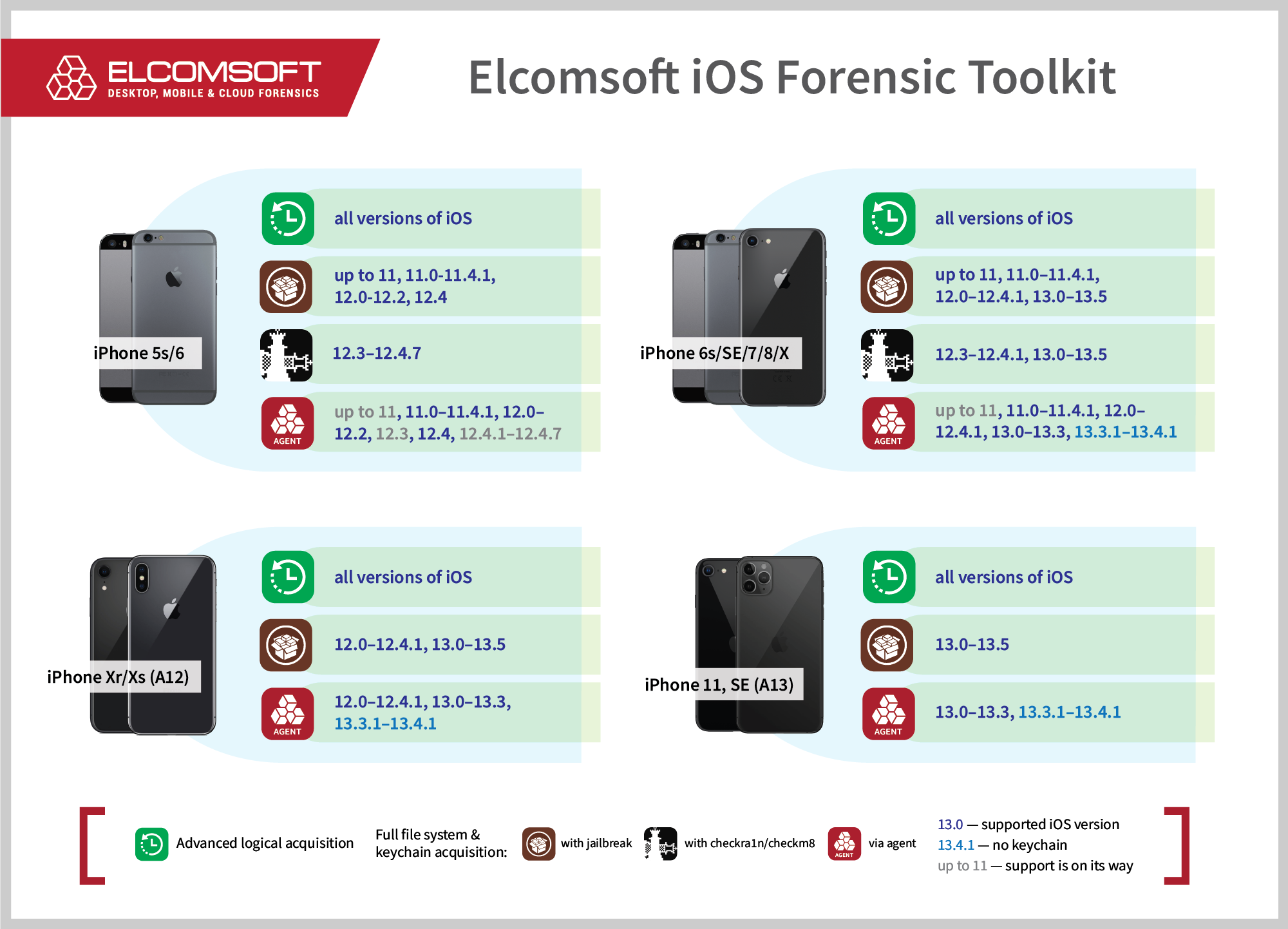
We already talked about agent-based extraction several times. We see jailbreaking as the last resort, a fallback of a sort. For this reason, we have developed a method that allows to extract the same amount of data without jailbreaking.
- Supported devices: iPhone 5s to iPhone 11 Pro Max and iPhone SE 2 (2020)
- Supported versions iOS: iOS 11.0 to iOS 13.3 (with some exceptions for iPhone 5s and iPhone 6)
- Pros: 100% safe; forensically sound
- Cons: requires Apple developer account; limited compatibility
Other jailbreaks
For iOS 11 and iOS 12, several other jailbreaks are available. I’d like to mention Electra, rootlessJB and Chimera. We fully support Electra and Chimera, but had to remove rootlessJB support due to potential technical issues that are outside the scope of this article. For all supported devices and versions of iOS, we recommend using checkra1n and unc0ver instead.
For older iOS versions, jailbreaks exist as well:
- iOS 10.0 to iOS 10.3.3: Meridian
- iOS 9.2 to iOS 9.3.3: Pangu
- iOS 9.0 to 9.1: Pangu (different version, separate download)
- iOS 8.0 to iOS 8.4: TaiG
We tested all of them and have not found any problems with full file system and keychain acquisition. Just note that some of these jailbreaks do not have ssh included, so you will have to install OpenSSH from Cydia, so bringing the device online, which is risky. We are about to add iOS 10 support to our agent-based acquisition soon.
Workflow
When considering the path to take during the acquisition, always obtain as much information about the device as possible. You’ll need:
- Device model
- Installed iOS version
- Whether the device is locked and if you know the passcode
For disabled and locked devices with the passcode unknown, you have no option but checkra1n, and even then you’ll be limited to BFU (Before First Unlock) acquisition with very limited set of data. It’s still much better than nothing; just remember that it only works with devices running iOS 12.3 and later. Also, checkra1n versions 0.9.6+ force USB restrictions mode to be activated, so using an older version of that jailbreak is recommended.
If the device screen is unlocked, but the device is running the latest version of iOS (13.5.1 or 13.5.5 beta), checkra1n is again the only way to perform the full extraction.
For most other devices and versions of iOS, agent-based acquisition is the preferred method. As noted above, it is forensically sound, safe for the device, and also much faster. Agent-based extraction does not use an SSH backhaul, utilizing a direct USB connection instead. The current version of Elcomsoft iOS Forensic Toolkit has full extraction support for iOS 11.0 to 13.3; for iOS 13.3.1 to 13.4.1, we can only access the full file system but not the keychain.
Any reason to use unc0ver? You would only use it if you have a modern device based on the A12/A13 CPU (so an iPhone Xs, Xr, 11, 11 Pro, or SE2), and need to decrypt the keychain from an iOS 13.3.1-13.4.1 or iOS 13.5 device. We are working around the clock to add support for keychain acquisition for iOS 13.5, and this feature will be available in the upcoming version of Elcomsoft iOS Forensic Toolkit to be released early next week.
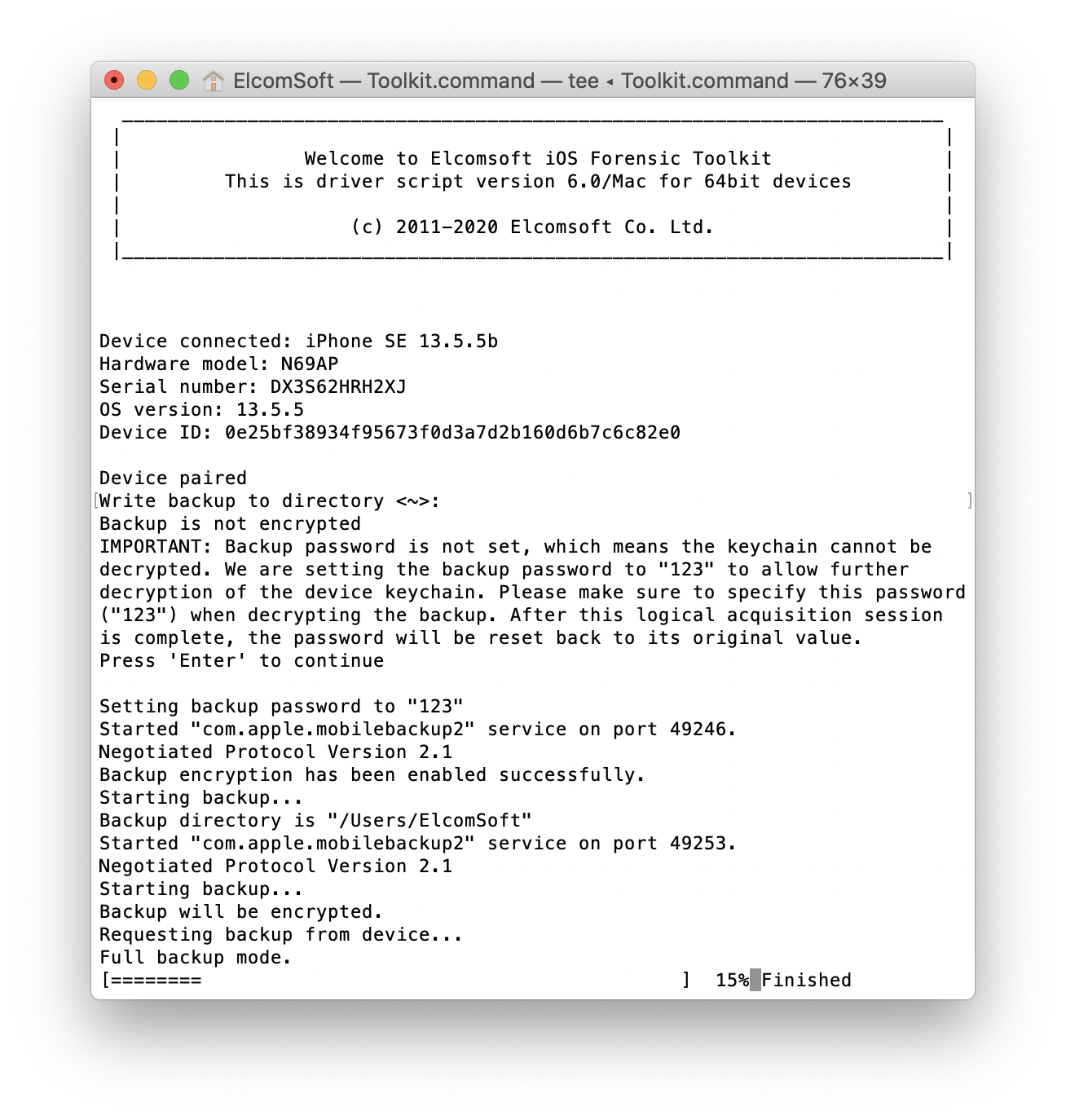
Finally, what can you do if your device is unsupported by both jailbreaks and our extraction agent? Logical acquisition to the rescue. Just remember the following:
- Prevent the iPhone from syncing with your PC
- Always create password-protected backups (they contain more data)
- Do not forget about the data other than the backup: media files, shared files, diagnostic and crash logs
Worst case scenario? A locked iPhone based on A12/A13 (so not vulnerable to checkm8), with USB restricted mode activated (so no chance even for logical acquisition, even with a valid lockdown/pairing record). All you can do is switch the device to diagnostic mode and extract basic information, then request cloud data from Apple the company (by quoting the device serial number), or try locating account credentials and do cloud extraction with Elcomsoft Phone Breaker.
Other Apple devices
Apple Watch S1 to S3 are also vulnerable to the checkm8 exploit, and so the full file system extraction is theoretically possible. Currently no jailbreak is available for the Apple Watch, and no direct extraction with the agent is possible.
What about the Apple TV? Both checkra1n and unc0ver jailbreaks are available for Apple TV 4 and 4K. We did not try checkra1n (it’s difficult to put an Apple TV 4K into DFU mode, you will need a special adapter for that), but unc0ver worked fine for tvOS up to 13.4.5. The information available in Apple TV can become handy even with logical acquisition, see Apple TV and Apple Watch Forensics 01: Acquisition for details.
Conclusion
We would be happy to offer the proverbial “one button” solution compatible with all Apple devices and versions of iOS. Unfortunately, this isn’t possible. We do our best to offer the choice of several different acquisition methods; in most cases, at least one of them would be applicable.






