The ninth beta of iOS Forensic Toolkit 8.0 for Mac introduces forensically sound, checkm8-based extraction of sixteen iPad, iPod Touch and Apple TV models. The low-level extraction solution is now available for all iPad and all iPod Touch models susceptible to the checkm8 exploit.
checkm8 is applicable to all devices with bootloader vulnerability, yet there are technical differences when it comes to implementing the exploit on the various devices. In this update we are targeting non-iPhone devices, spending efforts to support the many iPads equipped with the corresponding SoCs. While other vendors have been offering their own implementations of checkm8 extraction for quite a while, we found their solutions to lack in device/iOS version coverage and miss the “forensically sound” mark.
Typically, service life of an iPad is several times as long as an iPhone of the same generation. This is reflected in the number of supported battery charge cycles. While Apple claims that a typical iPhone battery is designed to retain up to 80% of its original capacity at 500 complete charge cycles, an iPad battery is designed to retain similar capacity at 1000 complete charge cycles. In other words, despite their age, many of these tablets are still actively used – and can now be extracted.
In addition to extended service life, iPads are real workhorses compared to the iPhone. They are actively used in companies and as BYOD. Unlike iPhones, which are designated as media consumption devices, iPads (especially the Pro lineup) are made for creative tasks, which results in a lot of highly valuable potential evidence.
Compatibility
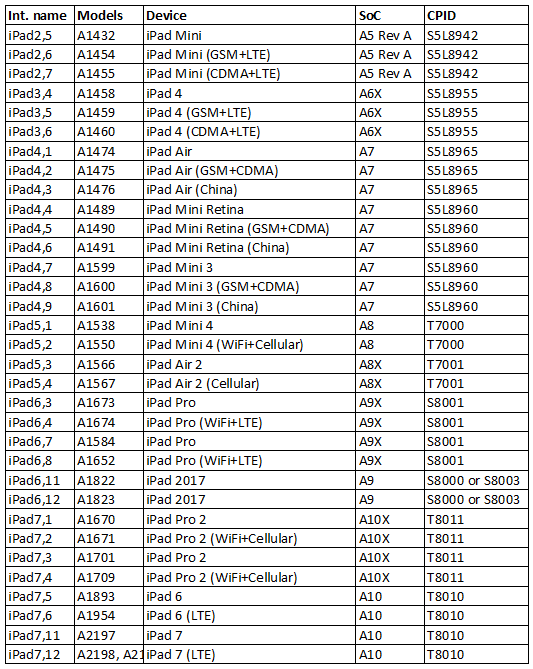
The newly added iPad models include the full-size iPad 5, 6, and 7, the iPad Mini 2, 3, and 4, the iPad Air 1 and 2, and the iPad Pro 1 and 2 (9.7” and 12.9” models respectively). In addition, iPod Touch 6 and 7 are also supported. This is in addition to previously supported iPad and iPod Touch models. Currently, our checkm8 extraction solution supports all iPad and all iPod Touch models having the bootloader vulnerability with no exceptions.

All versions of iOS up to and including iOS 15.5 are supported. Here is the full list of supported iPad models:
Technical notes
For most devices the exploit can be applied directly. However, there are several requirements when it comes to some other devices.
The Apple TV 4K does not have a USB port anymore. Connecting it to the computer requires additional hardware and some soldering skills.
For iPad 6/7 and iPad Pro 2 devices running iOS 14 or 15, the passcode must be removed prior to the extraction. Follow this guide to disable the passcode: How to Remove The iPhone Passcode You Cannot Remove
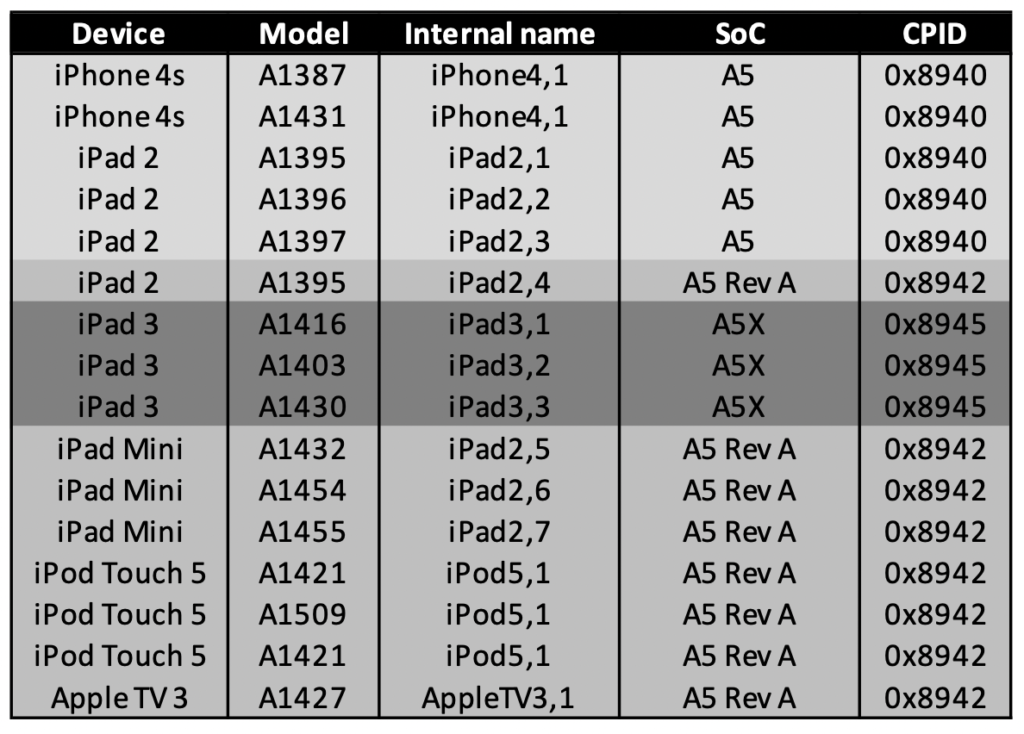
Will I need the Pico board?
In the seventh beta, we introduced a hardware/software solution to help place the iPhone 4s into PwnedDFU. The solution requires a Raspberry Pi Pico board with custom firmware. You won’t need the Pico board to work with most iPad and iPod Touch models except those based on the same USB controller as the iPhone 4s.
Please refer to the following table for devices requiring the Raspberry Pi Pico board to utilize our checkm8 extraction solution:
Conclusion
It is difficult to underestimate the importance of checkm8 for mobile forensic specialists. Our solution is the only one on the market supporting forensically sound checkm8 extraction for all Apple devices with the bootloader vulnerability, including all compatible iPhone, iPad, and iPod Touch models, as well as the Apple TV and Apple Watch devices.





