We’ve just released the first major update to Elcomsoft Phone Viewer, our lightweight forensic tool for glancing over data extracted from mobile devices. Boosting version number to 2.0, we added quite a lot of things, making it a highly recommended update.
So what’s new in Phone Viewer 2.0? Improved compatibility with full support for iOS 9 backups (both local and iCloud). Support for media files (pictures and videos) with thumbnail gallery and built-in viewer. EXIF parsing and filtering with geolocation extraction and mapping. These things greatly enhance usage experience and add the ability to track subject’s coordinates on the map based on location data extracted from the images captured with their smartphone.
How does it all work? As you can expect from an ElcomSoft tool, everything is perfectly smooth. We spent a while designing, implementing and testing each and every element of the user interface to make our tool really smooth, really fast and really simple.
iOS 9 Support
We already wrote about what’s new in iOS 9. What we didn’t publish just yet is the fact that Apple made significant changes into the way iOS 9 manages cloud backups. Now stored in iCloud Drive (instead of previously used iCloud), iOS 9 backups are stored in a different format and use new encryption. As a result, viewing iOS 9 cloud backups required an update to both the extraction tool (Elcomsoft Phone Breaker 5.0) and the viewer. Elcomsoft Phone Viewer 2.0 is ready to let you view iOS 9 backups regardless of whether you downloaded them off the cloud or just grabbed a copy created with Apple iTunes.
Did we mention Elcomsoft Phone Breaker? Version 5.0 is still the only stand-alone tool on the market to download and decrypt cloud backups produced by devices running iOS 9 (regardless of jailbreak status). Since iOS 9 is now running on more than 61% of eligible Apple devices, we highly recommend updating your copy of Elcomsoft Phone Breaker to version 5.0.
Multimedia Gallery
Unlike a countless number of free forensic tools, Elcomsoft Phone Viewer does not put every picture or video found on the device into a single gallery and gets away with it. Instead, the tool takes its time to categorize pictures, sorting every image into an appropriate folder. It can distinguish between images captured with the phone’s built-in camera and pictures received as MMS messages or attachments, sorting those into Camera Roll and Message Attachments folders correspondingly. Pictures captured with or saved by third-party apps (e.g. Camera+) are placed into yet another folder (Other Media), which also includes images and videos cached by the Web browser.
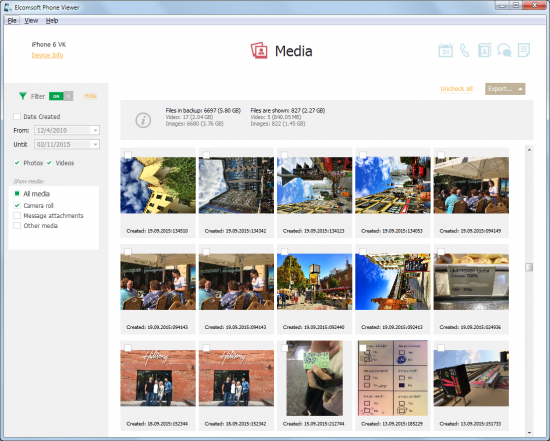
Now here’s the catch. Where are all the images that come with the apps? You know, all the icons, clip art, splash screens and other things shipped with every other app? We place those into the Other Media folder, and believe me, together with the files captured with third-party cameras.
EXIF Information
Each and every picture captured with the smartphone’s built-in camera comes with certain additional information embedded into the image. The extra data is stored in EXIF (Exchangeable image file format) tags, and contains information about where and when it was captured, what hardware was used, and what lighting conditions (and shooting parameters) there were. With this information, experts can actually do a lot of things. By analyzing EXIF tags, one can tell whether the image is original (unaltered) or faked (modified or post-processed in an image editor). In most cases, it can be possible to determine whether or not a particular picture was taken with a particular device (unless EXIF tags are faked). Important for digital investigations, EXIF metadata contains information about the date and time the image was captured, allowing experts to determine on what exact date and at what exact time the image was taken.
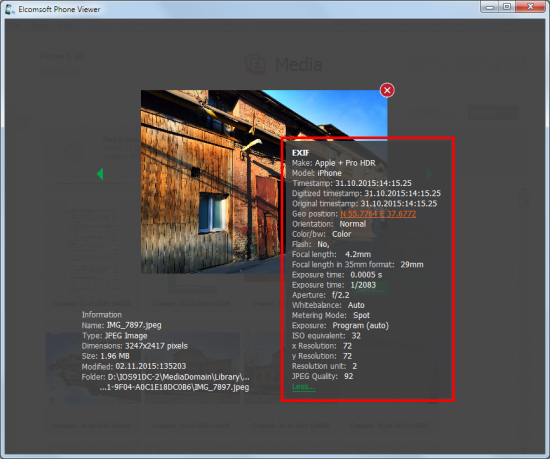
Speaking of Elcomsoft Phone Viewer, version 2.0 can now parse and display EXIF tags. Not only that; the product can actually use data from EXIF tags to allow you filtering images by the date they were captured. When investigating an incident, you’ll be most likely looking for images captured around a certain date. Elcomsoft Phone Viewer 2.0 allows you to specify a date range, only displaying a thumbnail gallery of pictures (and videos) that were captured during that range. Of course, that very same filter can be applied to images and videos received as MMS messages or attachments or captured with third-party apps – yet in those cases the filter will not be based on EXIF data.
Least but not last, EXIF metadata may contain (and, in most cases, does contain) information about the location where the picture was taken. Whether or not geolocation information is saved in EXIF is a configurable setting on most smartphones, yet in our experience many users just leave it on all the time.
Elcomsoft Phone Viewer 2.0 can now extract location data out of the image’s EXIF tags, place a location pin and display the map showing where and when the image was captured.
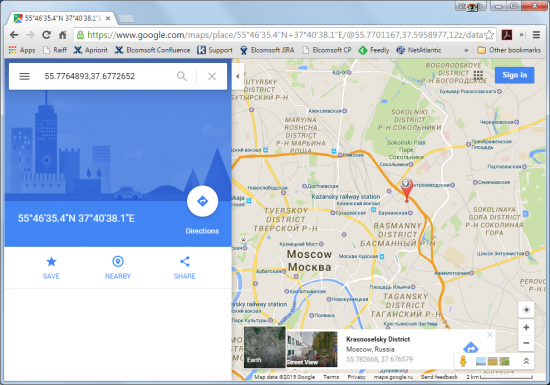
By reviewing a bunch of images with GPS coordinates, experts can track subject’s route around the time of the incident.
Despite the new features, the updated Elcomsoft Phone Viewer 2.0 remains one of the smallest and lightest forensic analysis tools on the market. It’s quick to launch and easy to use, requires no learning curve and affordable to everyone.
So what exactly is new in the new version? Here’s the full list:
- Support for iOS 9 backups (local and iCloud)
- Multimedia Gallery
- Automatic sorting of media files by categories (Camera Roll, Message Attachments, Other media)
- Full EXIF support
- Real-time filtering by date and time
- Positioning information extracted from EXIF tags and displayed on the map
- New filters for call and message logs
Have you ordered the tool already? Download the update free of charge! Still sitting on the fence? A free evaluation download is available!





