BitLocker is a popular full-disk encryption scheme employed in all versions of Windows (but not in every edition) since Windows Vista. BitLocker is used to protect stationary and removable volumes against outside attacks. Since Windows 8, BitLocker is activated by default on compatible devices if the administrative account logs in with Microsoft Account credentials. BitLocker protection is extremely robust, becoming a real roadblock for digital forensics.
Various forensic techniques exist allowing experts overcoming BitLocker protection. Capturing a memory dump of a computer while the encrypted volume is mounted is one of the most frequently used venues of attack. However, acquiring BitLocker-encrypted volumes may become significantly more difficult with the release of Windows 10 November Update. In this article, we’ll explore existing methods of recovering BitLocker volumes, look at what has changed with November Update, and review the remaining acquisition paths.
Windows 10 November Update
Microsoft has maintained compatibility between generations of BitLocker in all versions of Windows since Windows Vista through Windows 10 RTM. It was not until build 1511 of Windows 10 for BitLocker to receive a major overhaul. In Windows 10 build 1511 (often referred to as November Update), Microsoft updated BitLocker with support for XTS-AES encryption algorithm. The new mode supports both 128-bit and 256-bit XTS-AES keys, and provides an extra layer of protection against certain types of attacks. Since XTS-AES is not backward compatible with existing systems running earlier versions of Windows, this mode is an optional choice when encrypting an external drive with BitLocker to Go.
XTS-AES is not the only thing new to BitLocker with Windows 10 November Update. Microsoft has implemented a change to DMA port access, adding a new MDM policy to allow system administrators blocking DMA ports (think FireWire) when the device is starting up. In addition, unused ports with DMA access (e.g. FireWire) are automatically disabled when the device is locked (existing devices may continue to work). The DMA ports are turned back on when the device is unlocked.
This new policy makes it impossible using a FireWire attack for capturing a live RAM dump if the device being acquired is locked. Since the FireWire attack was one of the major acquisition paths for encrypted volumes (as well as for capturing massive amounts of volatile evidence), the November Update presents a real obstacle to digital investigations.
The Use of BitLocker
It might be true that all versions of Windows since Windows Vista support BitLocker encryption. However, not all Windows editions do. BitLocker is available on the Ultimate and Enterprise editions of Windows Vista and Windows 7, as well as the Pro and Enterprise editions of Windows 8 and Windows 10.
However, there’s more to BitLocker than meets the eye. In addition to “full” BitLocker, Microsoft ships BitLocker Device Encryption with the core edition of Windows 8.1, Windows RT, and Windows 10 Home. Device encryption is a feature-limited version of BitLocker that automatically encrypts the system boot volume.
BitLocker device encryption is activated automatically if all of the following conditions are met:
- The device meets Connected Standby or Modern Standby specifications, which typically require solid-state storage (SSD or eMMC)
- The device features non-removable (soldered) RAM to protect against cold boot attacks
- The device is equipped with a TPM 2.0 chip
- At least one account with administrative privileges logs in with Microsoft Account credentials (as opposed to using a local Windows account)
These conditions are frequently met on Windows-powered tablets (such as Lenovo ThinkPad 8, Nokia Lumia 2520 or Dell Venue 8 Pro), most business laptops and many high-end and even mid-range ultrabooks. (Notable, Apple’s Macbooks are not equipped with TPM chips).
As soon as the system meets the requirements, and the user logs in with a Microsoft Account, Windows begin encrypting the boot partition with BitLocker. The encryption is done completely in background and without prompting the user; the user may not be even aware that their system partition is encrypted. The only indication of the encryption process may be the higher than usual disk activity and battery consumption.
BitLocker Escrow Keys
Unlike the “full” BitLocker that offers multiple options for creating and storing escrow keys, BitLocker device protection automatically creates a so-called Recovery Key. The Recovery Key is automatically uploaded into the user’s Microsoft Account. For this purpose, Windows uses the first Microsoft account with administrative privileges. The Recovery Key is then stored to the user’s Microsoft Account. Alternatively, the Recovery Key can be stored in the Active Directory, if a corresponding security policy exists.
New in Windows 10 November Update: the Recovery Key can now be stored in Azure Active Directory. According to Microsoft, “In addition to using a Microsoft Account, automatic device encryption can now encrypt devices that are joined to an Azure Active Directory domain. When the device is encrypted, the BitLocker recovery key is automatically escrowed to Azure Active Directory.” source
Attacking BitLocker Protection
There are several methods allowing to decrypt a BitLocker volume.
- For BitLocker volumes and removable devices encrypted with BitLocker To Go, one can perform an attack on the original plain-text password. Once the password is recovered, the volume can be instantly unlocked.
- Volumes encrypted with either BitLocker Device Protection or the full BitLocker can be decrypted by extracting a binary encryption key from the computer’s RAM dump. The dump must be captured while the encrypted volume is mounted.
- BitLocker Device Protection automatically saves an escrow key (BitLocker Recovery Key) into the user’s Microsoft Account, Active Directory or Azure cloud. The user may or may not be aware that a recovery key exists. By pulling the Recovery Key from https://onedrive.live.com/recoverykey, investigators can use it to unlock encrypted volumes.
Recovering BitLocker Password
Attacking the original plain-text password is the most obvious and straightforward acquisition approach. A number of forensic tools such as Elcomsoft Distributed Password Recovery exist allowing enumerating text-based passwords in an attempt to recover the correct one. However, BitLocker (as well as most recognized full-disk encryption products) was designed specifically to sustain this type of attacks. Enumerating passwords is painfully slow even if you run a distributed attack with multiple computers, each equipped with a high-end GPU accelerator.
Due to the strong protection used by Microsoft on BitLocker volumes, brute-forcing passwords is extremely slow to the point of becoming unfeasible for all but the simplest passwords. Even if GPU acceleration is enabled, breaking BitLocker passwords remains painfully slow. Attempting to recover a BitLocker password only becomes feasible if a custom password dictionary is available (such as the list of passwords used by the same person to protect accounts, documents, archives etc.)
The actual recovery speed (using Elcomsoft Distributed Password Recovery on a single PC equipped with a single GPU unit) is as follows:
- CPU Xeon E5-2603 (4 cores, 1.80GHz): 2 passwords per second
- NVIDIA GeForce GTX 750 Ti: 150 passwords per second
- NVIDIA GeForce GTX 980: 490 passwords per second
- NVIDIA GeForce GTX Titan: 195 passwords per second
Even with 500 passwords per second, breaking a 6-character alphanumerical password could take over three years. If more than six alphanumerical characters are used, or if the password contains one or more special characters, the recovery time increases significantly.
Extracting Decryption Key
Extracting the binary decryption key from the computer’s RAM dump is one of the most commonly used attacks on BitLocker and other full-disk encryption tools. In order to extract the decryption key, one needs to either make the computer produce a RAM dump.
Once the memory dump has been captured (one can use any kernel-mode RAM dumping tool such as Belkasoft Live RAM Capturer), one can use Elcomsoft Forensic Disk Decryptor to load the RAM image, locate and extract the BitLocker decryption key, and use that key to either mount the encrypted volume or decrypt it for offline analysis.
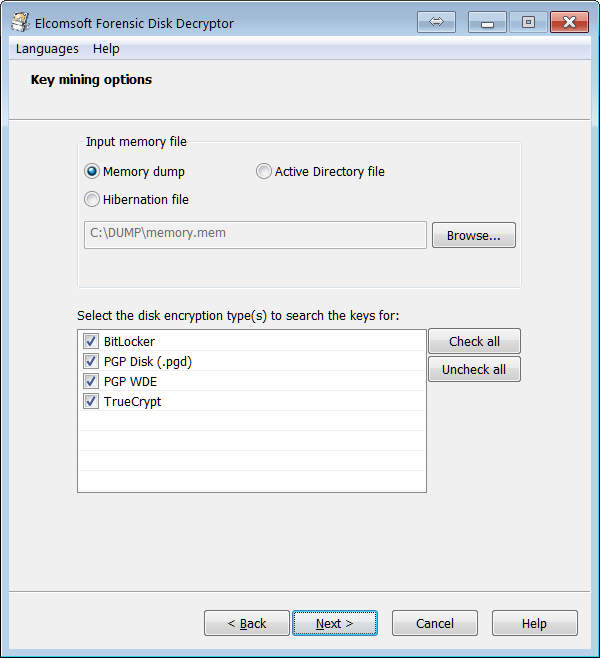
Sleep Mode
If the computer being acquired has entered sleep mode (or uses Modern Standby), the BitLocker decryption key is still stored in the computer’s RAM. If this is the case, it could be possible to run a
DMA attack over a FireWire port to read the contents of physical memory. This attack is very common, and Windows provided no protection against it in all versions of Windows before Windows 10 November Update (build 1511).
New in Windows 10 November Update: Microsoft has finally addressed the ongoing security issue by implementing a new MDM policy allowing to block DMA port access while the computer is sleeping and before it is unlocked. The new policy, if enabled, allows disabling unused DMA ports (e.g. FireWire) when the device is locked or sleeping. source
If the computer has this new policy enabled, a FireWire attack is no longer possible.
BitLocker Device Protection and Hibernation
If BitLocker Device Protection is active, the hibernation file is automatically encrypted once the system enters deep sleep (hibernation) mode. It is therefore not possible to extract the decryption key from the hibernation file as that file itself is encrypted with BitLocker.
On the other hand, if the boot volume is not encrypted but other volumes are, the decryption key to unlock those other volumes will be saved into the hibernation file, and can be extracted and used to mount or decrypt those volumes.
Accessing BitLocker Escrow Keys
The easiest way to decrypt a system volume encrypted with BitLocker Device Protection is by using BitLocker escrow keys or, as Microsoft calls them, “BitLocker Recovery Keys”.
What triggers BitLocker device protection? The encryption starts on devices meeting the minimum requirements once the administrative user logs in with their Microsoft Account credentials instead of using a local Windows account. At this time, Windows generates a unique BitLocker identification record as well as the corresponding escrow (recovery) key. BitLocker Recovery Keys are then automatically uploaded to the user’s Microsoft Account (alternatively, they are uploaded to Active Directory or Azure Active Directory if the corresponding MDM security policy is in place).
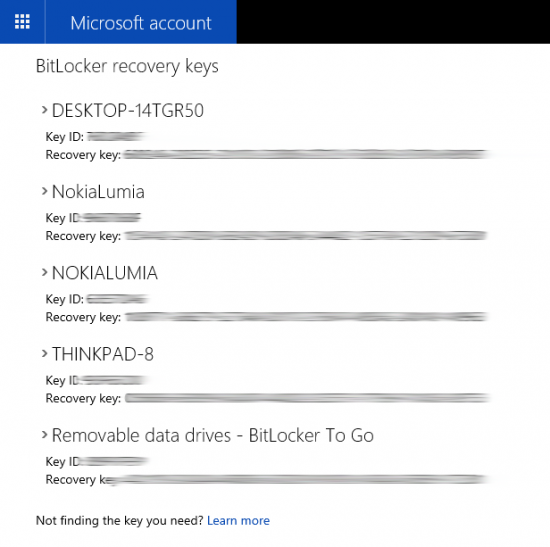
Once you know the account password, you can access all BitLocker Recovery Keys from that account. The keys are available at the following link (must use the correct Microsoft Account credentials to access): https://onedrive.live.com/recoverykey
Once logged in, you’ll be able to access BitLocker Recovery Keys to all devices registered under that Microsoft Account:
Recovering Microsoft Account Password
Once you know the user’s Microsoft Account credentials, you can access BitLocker escrow keys. But what if you don’t? Since Microsoft Account is cloud-based, its authentication credentials are stored on Microsoft servers, meaning that you cannot brute-force the password in a traditional way.
However, you may still be able to brute-force that password if you have access to at least one computer that uses the same Microsoft Account credentials without BitLocker encryption. This scenario is extremely likely if the user owns a Windows tablet, business laptop or ultrabook that DOES have BitLocker protection and, at the same time, uses a desktop PC that DOES NOT have such protection.
This scenario is very likely because desktop computers rarely, if ever, meet the requirements for BitLocker Device Protection. Indeed, most desktop PCs have removable RAM (thus violating one of the requirements) and are not equipped with a TPM 2.0 module (which is an absolute must for BitLocker Device Protection).
Microsoft Account passwords are not normally stored anywhere on the user’s computer, meaning that simply extracting the password is not possible. However, in order to facilitate logins in the absence of network connectivity, Microsoft had to cache a password hash and store it on the computer. On the one hand, this allows users to log in to their computer while using it offline. On another hand, this also allows extracting the cached hash file and running an offline attack to recover the original password.
As you can see, recovering Microsoft Account passwords is a two-step process. During the first step, you will be extracting the password hash (and attempting a range of quick attacks to try some of the most common passwords). If the first step does not reveal the original password, you will need to attack the password offline using one or more computers equipped with GPU units. These attacks are straightforward and very well optimized, allowing enumerating password combinations extremely quickly.
In order to extract the user’s Microsoft Account password, you would need two tools: Elcomsoft System Recovery and Elcomsoft Distributed Password Recovery.
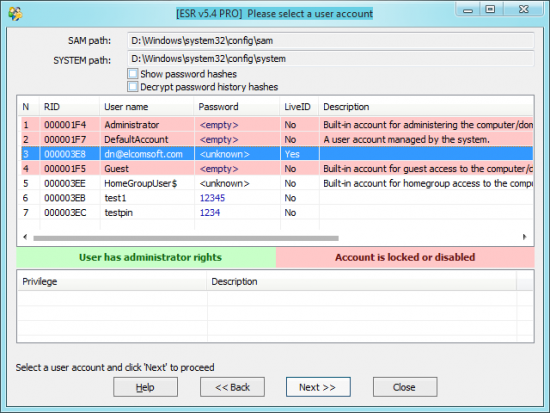
- To extract password hashes, run Elcomsoft System Recovery, select one or more accounts, and click Next. The tool will export the hashes into a file.
- Now when you have the hash file (let’s say its name is “x.pwdump”), transfer it to the computer where you have Elcomsoft Distributed Password Recovery installed. Launch Elcomsoft Distributed Password Recovery and choose to recover a Windows account password. Select “x.pwdump” you’ve just exported. Configure attacks (dictionary, brute force, or combination). Schedule the task and wait while Elcomsoft Distributed Password Recovery enumerates all allowed password combinations.
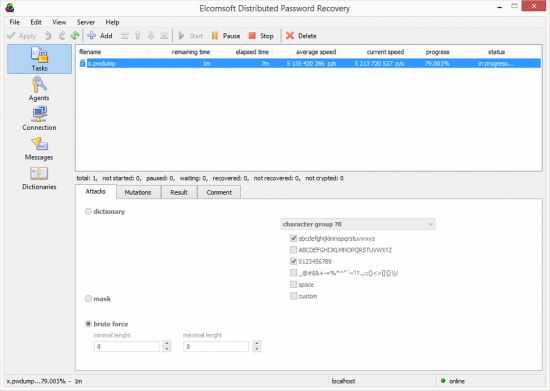
Once Elcomsoft Distributed Password Recovery discovers the correct password, you can use it for logging in to the user’s online Microsoft Account, downloading BitLocker Recovery Keys and using them to decrypt the system partition protected with BitLocker. Alternatively, you can just use the recovered Microsoft Account credentials to log in to the system being investigated. In this case, the encrypted volume will be unlocked automatically without requiring the use of BitLocker Recovery Keys.
Conclusion
Windows 10 November Update introduced several changes to system security. A new XTS-AES encryption algorithm better protects BitLocker volumes. BitLocker escrow keys can now be saved to Azure Active Directory in addition to Microsoft Account. Finally, Microsoft has addressed the long-standing vulnerability allowing attackers capturing the content of the computer’s RAM via a FireWire attack by utilizing ports with DMA access. These security changes present new challenges to forensic experts. However, new acquisition methods are actively developed to overcome the challenge.
BitLocker, EDPR, EFDD, Elcomsoft Distributed Password Recovery, Elcomsoft Forensic Disk Decryptor, Elcomsoft System Recovery, ESR, Microsoft Account, TPM, Windows 10, XTS-AES






