Since early days of iOS, iTunes-style system backups could be protected with a password. The password was always the property of the device; if the backup was protected with a password, it would come out encrypted. It didn’t matter whether one made a backup with iTunes, iOS Forensic Toolkit or other forensic software during the course of logical acquisition; if a backup password was enabled, all you’d get would be a stream of encrypted data.
Password protection of iOS system backups was always a hallmark of iOS data protection. We praised Apple for making it tougher for unauthorized persons to pair an iPhone to the computer in iOS 11. Today we discovered something that works in reverse, making it possible for anyone who can unlock an iPhone to simply reset the backup password. Is this so big of a deal? Prior to this discovery, forensic specialists would have to use high-end hardware to try recovering the original backup password at a rate of just several passwords per second, meaning that even the simplest password would require years to break. Today, it just takes a few taps to get rid of that password completely. If you know the passcode, logical acquisition now becomes a trivial and guaranteed endeavor.
iOS Backup Password Security
How secure, exactly, are iOS backup passwords? We measured the recovery rate or backups made by several different versions of iOS, and here are the results.
- iOS 4 to 9 (and 10.1): about 150,000 passwords per second on GPU (NVIDIA GeForce 1080)
- iOS 10.0: about 6,000,000 passwords per second with Intel i5 CPU due to a bug we discovered
- iOS 10.2 and up (incl. iOS 11): about 5 passwords per minute (CPU); ~100 passwords per second on GPU
As you can see, iOS backup passwords are pretty secure. With just 100 passwords per second (iOS 11, GPU acceleration), a simple 6-character password would take over a month to break – considering the password only contains of lower-case letters! 6-character password with at least one capital character and a digit would take several years to break. Don’t even dream of breaking longer/more complex passwords!
iOS 11 Ruins It
Prior to iOS 11, if you’ve got an iPhone and attempted to perform logical acquisition by pulling an iTunes backup, you would always face the risk of backup data being encrypted with an unknown password. If this was the case, your only option would be using Elcomsoft Phone Breaker or Elcomsoft Distributed Password Recovery to attack the original, plain-text password in order to decrypt the backup. Depending on the version of iOS installed on the iPhone or iPad you were extracting, the recovery speed would be slow or very slow, with iOS 10.2 through iOS 11 being the slowest.
It is very important to note that, once a backup password was set, all versions of iOS prior to iOS 11 would not allow to remove or change that password without either providing the original backup password (that you may not know) or performing a full factory reset of the iPhone/iPad.
In iOS 11, Apple makes it possible to simply reset the backup password on the iPhone. The procedure is simple.
- Unlock the iPhone with Touch ID, Face ID or passcode.
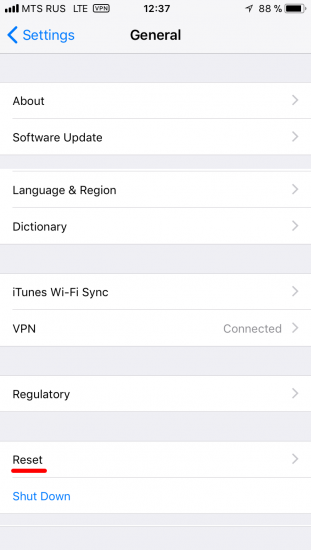
- Open the Settings app and navigate to General.
- Scroll all the way down and tap Reset.
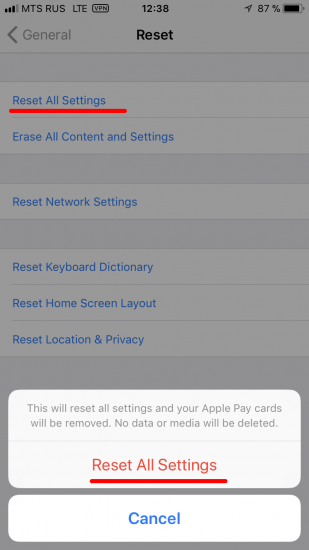
- Tap and confirm Reset All Settings (iPhone passcode required if enabled).
Using “Reset All Settings” will erase the following settings:
- Display brightness
- Whether or not to display battery percentage
- All Wi-Fi passwords (but not any other passwords or tokens stored in the Keychain)
- apple.wifi.plist
- iTunes backup password
As you can see, resetting an iTunes backup password is fairly simple. All you lose are a few settings that aren’t all that important for the investigation, as well as the list of Wi-Fi passwords. All user data including the content of the Keychain (except Wi-Fi passwords) are preserved.
It is important to know that this process does not wipe/invalidate existing pairing records (lockdown files); otherwise, with iOS 11 new security policy, that would require you to enter device passcode in order to establish a new pairing relationship between the iPhone and the desktop. As a result, you may use an existing lockdown record to perform logical acquisition; however, you would still need to enter device passcode in order to Reset All Settings.
iOS 10 and Earlier
According to Apple, “If you have a device with iOS 10 or earlier, you can’t reset the password.”
Check If Backup Password Is Enabled
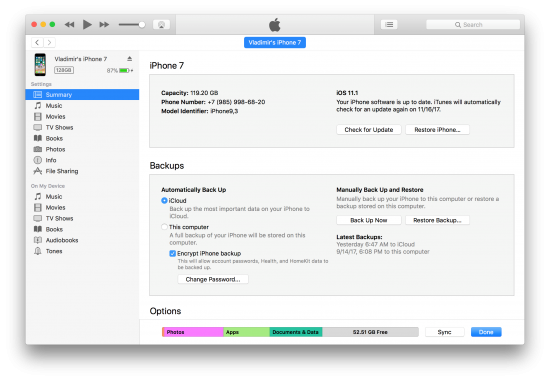
You can check if the backup password is enabled by either using Elcomsoft iOS Forensic Toolkit (the “(I)nfo” option) or with iTunes. Note, however, that iTunes may alter the content of the device by syncing it with the computer. In the following screen shot, you can see that “Encrypt iPhone Backup” is enabled. This means you’ll have to recover the backup password in order to decrypt the backup – or simply reset it on the device if it is running iOS 11.
Logical Acquisition of iOS 11 Devices with Unknown Backup Password
We recommend the following approach to performing logical acquisition of iOS 11 devices if (and only if) the backup is protected with an unknown password.
Pre-requisites:
- iPhone or iPad device running iOS 11
- Elcomsoft iOS Forensic Toolkit 2.40 or newer
- Backup password is set and is unknown (whether or not a backup password is set can be verified by using the (I)nfo command of Elcomsoft iOS Forensic Toolkit)
- Device passcode not set or is known (it will be required to Reset All Settings, and you may need it to establish a trust relationship, which is required to pull a backup after resetting the password)
Steps:
- Perform steps to create a local backup. You may still attempt attacking the original backup password.
- Disconnect the iPhone or iPad device from the computer.
- Unlock the iPhone or iPad device with Touch ID, Face ID or passcode.
- In Settings – General – Reset, tap and confirm Reset All Settings. Note: device passcode required (if enabled).
- Reconnect the iPhone or iPad device to the computer.
- (Skip this step if you have a valid lockdown file) You will be prompted to establish the trust relationship with the computer. Confirm prompts on the computer and on the iPhone or iPad device.
- (Skip this step if you have a valid lockdown file) You will be prompted to enter device passcode on the iPhone or iPad device. Provide the passcode to complete pairing.
- Once the pairing relationship is established, use Elcomsoft iOS Forensic Toolkit to create a new backup. Note: iOS Forensic Toolkit will set a temporary password of “123”; this will allow you to decrypt keychain items. You may use an existing lockdown file (pairing record) to create the backup.
Our Take
In our opinion, the new “feature” looks like a huge step backwards. The ability to reset backup password allows anyone who can unlock your iPhone (and knows the passcode, if one is enabled) to pull the (mostly) complete set of data from your device, which includes your credit card data, passwords and tokens. In many cases this even includes the Apple ID token, which in turn opens access to almost everything in the cloud such as iCloud Photo Library. The passcode remains the only thing to protect your iPhone. If your passcode is compromised, the content of your iPhone is now open to anyone with access to the actual device.
Conclusion
iOS 11 makes it possible to reset passwords protecting iTunes-style backups, which was never possible in previous versions of iOS. Interestingly (and somewhat counter-intuitively), the All Settings reset does not invalidate existing lockdown (pairing) records (the “Reset Network Settings” option does; apparently, Apple does not consider network settings to be part of “all” settings – so they should have named the feature as “Reset Some Settings” instead). If it would, you’d require to re-establishing trust relationship with the computer you’re to make the backup. Since iOS 11 requires entering device passcode in order to establish trust between the device and the computer, you would need to know the original device passcode in order to perform logical acquisition. Since pairing records are not invalidated, you may extract a lockdown file from the user’s computer and use it in order to make a backup (but you would still need that passcode in order to reset backup password).
Thanks to Cindy Murphy from Gillware who first discovered that change in iOS 11, and to Mattia Epifani, the author of Learning iOS Forensics book, who pointed out to the article at Gillware.





