If you are familiar with breaking passwords, you already know that different tools and file formats require a very different amount of efforts to break. Breaking a password protecting a RAR archive can take ten times as long as breaking a password to a ZIP archive with the same content, while breaking a Word document saved in Office 2016 can take ten times as long as breaking an Office 2010 document. With solutions for over 300 file formats and encryption algorithms, we still find iTunes backups amazing, and their passwords to be very different from the rest of the crop in some interesting ways. In this article we tried to gather everything we know about iTunes backup passwords to help you break (or reset) their passwords in the most efficient way.
What is an iTunes backup
Apple’s iPhone has one of the most amazing backup systems of all competing platforms. Some basic information on iOS backups is available in Apple’s About backups for iOS devices. While iOS backups include a lot of data, they don’t contain everything. Here is a quote:
An iTunes backup doesn’t include:
- Content from the iTunes and App Stores, or PDFs downloaded directly to Apple Books
- Content synced from iTunes, like imported MP3s or CDs, videos, books, and photos
- Data already stored in iCloud, like iCloud Photos, iMessages, and text (SMS) and multimedia (MMS) messages
- Face ID or Touch ID settings
- Apple Pay information and settings
- Apple Mail data
- Activity, Health, and Keychain data (To back up this content, you’ll need to use Encrypted Backup in iTunes.)
There are more articles on backups in Apple knowledge base, in particular:
So, basically, a local backup has almost everything one requires to restore an existing iPhone or set up a new one. Transferring files and settings to another device is fast and easy; your experience with a replacement device will not be much different from using your old iPhone.
So what about the “almost” part of “everything”? While a restored device will look the same, it will be missing some important data that will be lost when you restore. Which data, exactly? More on that later.
Backup contents: the technical side
Traditionally, computer backups are created by a special program that enumerates all files at a specific location, optionally compresses them and stores the data in a huge single “archive” (usually accompanied with an index).
This is not going to work with iPhones. There is no way a computer the iPhone is connected could access any specific files on the device except for media (photos and videos). There are many reasons for that, and the most important are security and data integrity.
So how does it work then? The backups are produced on the device itself. The program you run on the desktop, be it iTunes or another app, does nothing but sending a command (over a USB port or Wi-Fi) to the iPhone. A special service running on iOS then goes through the file system (except many specific ares), collects and sends the data back to the “host” computer. What do we need the “host” computer for? It’s used to receive and save the data into a file on a hard disk.
iTunes backups are stored in an unusual way. Even if there is no iTunes with iOS 13 anymore, macOS 10.15 beta suggests that the backups will remain the same, it’s just the way to create them will be slightly different. In a nutshell, iTunes backups are a partial copy of the iOS file system, but you will not see any familiar files and folders. Instead, the file names in the backup are actually hashes of the actual names (with path), accompanied with a kind of an index (as a database) and some additional metadata.
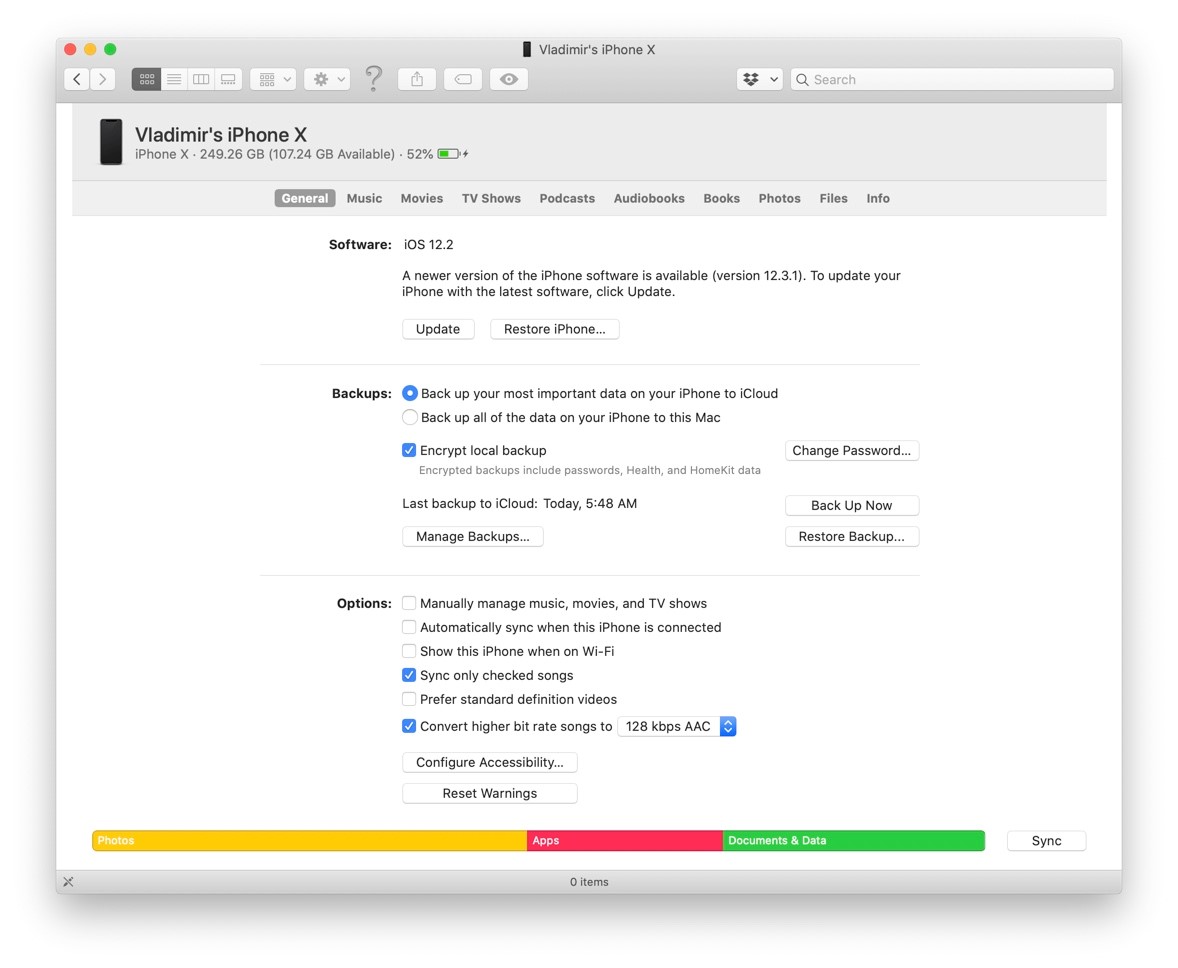 Apple does not provide any tools to work with iOS backups. All you can do is restoring the backup to a new device, and that’s it. Of course, there are several third-party tools to browse backup contents (and export selected data from there); e.g. Elcomsoft Phone Viewer (in fact it does much more than that).
Apple does not provide any tools to work with iOS backups. All you can do is restoring the backup to a new device, and that’s it. Of course, there are several third-party tools to browse backup contents (and export selected data from there); e.g. Elcomsoft Phone Viewer (in fact it does much more than that).
 iTunes backups: encryption and passwords
iTunes backups: encryption and passwords
Finally, we are about to talk about passwords! In iOS, backup passwords are highly unusual for at least three different reasons.
Similar to other file formats, iTunes backups can be protected with a password; more information at About encrypted backups in iTunes. In brief:
With iOS 11 or later, you can make a new encrypted backup of your device by resetting the password. Here’s what to do:
- On your iOS device, go to Settings > General > Reset.
- Tap Reset All Settings and enter your iOS passcode.
- Follow the steps to reset your settings. This won’t affect your user data or passwords, but it will reset settings like display brightness, Home screen layout, and wallpaper. It also removes your encrypted backup password.
- Connect your device to iTunes again and create a new encrypted backup.
And this is where the similarities end. There is something important that makes encrypted iTunes backups different from any other encrypted file.
First, the backup password is not just a property of the backup itself; it is also a property of the particular device. Once you set the password, this password is stored somewhere deep inside the device. When asked to perform a device backup, iTunes does nothing but sending a command to the device, and the special service running on iOS returns an encrypted stream of data. The encryption happens entirely on the device and not on the host computer. If you connect the device to another computer and use iTunes or a third-party tool, the backup will be created with exactly the same password. For the computer of the tool there is no workaround, and there is no way to change it until you know the old password.
What can you do if you genuinely forget your backup password? After all, a backup password is not something you would regularly type. First, if you encrypted backup on a computer running macOS, there is a good chance that the password is saved in the macOS keychain (in “iOS backup” record), and can be easily extracted from there using the Keychain utility.
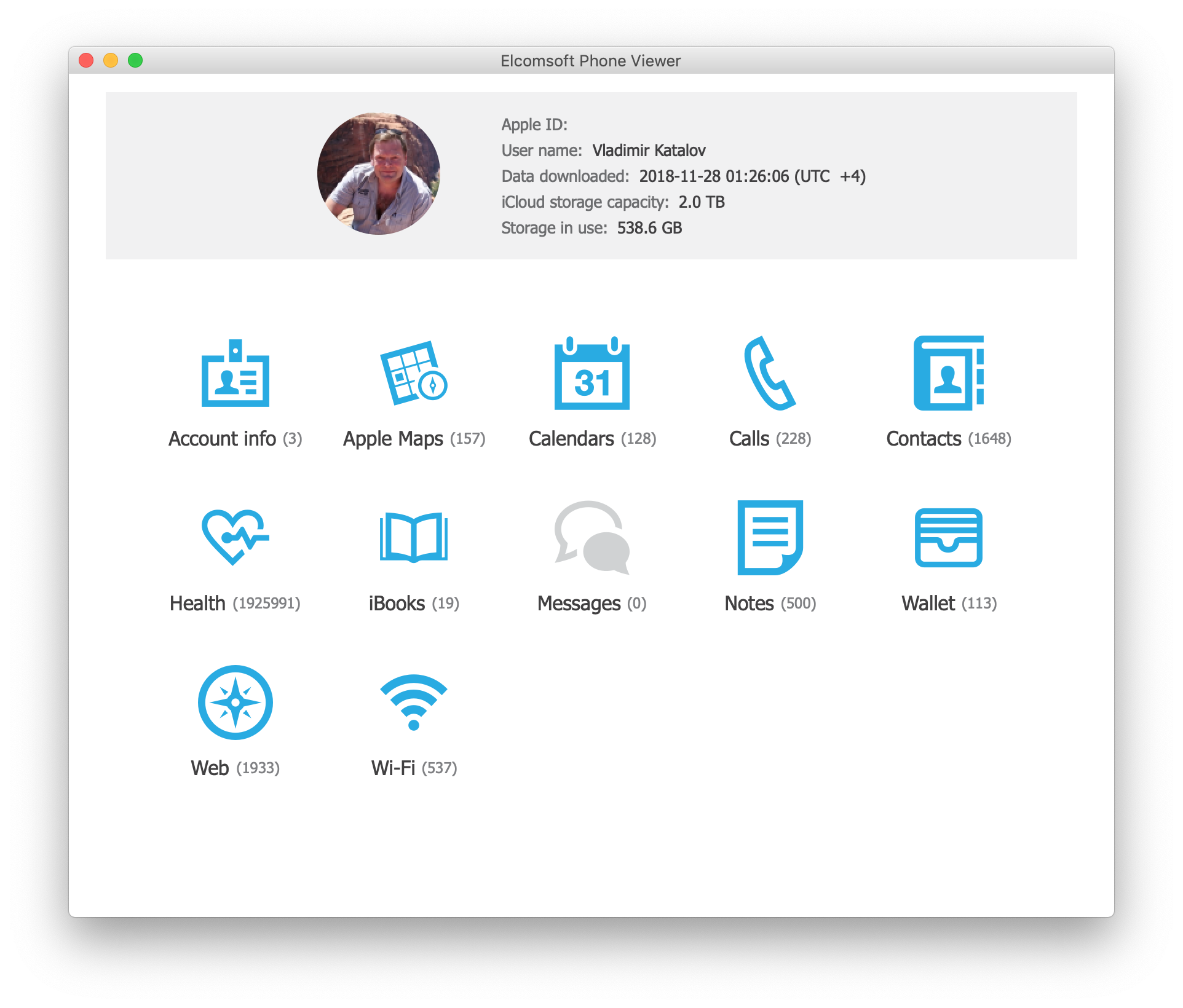
Second, you can try to break the password (e.g. with Elcomsoft Phone Breaker) using a dictionary or brute-force attack. Starting with iOS 10.2, however, the encryption is extremely strong, and even with a modern video card, your password recovery rate will be very limited: no more than about 200 passwords per second with a high-end GPU accelerator. This makes long and complex passwords virtually unbreakable. What we’d recommend is creating focused dictionaries/wordlists based on all passwords you can think of for a particular user, plus other passwords stored in the system (e.g. in Web browsers); these can be extracted with Elcomsoft Internet Password Breaker.
Finally, if you still have the device itself, you can sometimes reset the password – read the next chapter for details.
We heard a lot of “horror stories” when someone forgot their backup password and needed to restore from a backup to a new device, with the original iPhone being sold already, or broken. Moreover, it looks like sometimes the password is being set by something in iOS without the user even knowing (sounds crazy, but Apple support forum is full of messages saying that password has never been set, and the owner of the iPhone even did not know that it can be set). And that is a huge problem – again, with such a strong encryption, the chances to recover these passwords are very low.
Backups and the keychain
Another thing why iPhone backup passwords are unusual is the keychain. There really is a huge difference between password-protected iTunes backups and backups without a password that makes password-protected backups even more desirable for an expert than those without a password. Apple says the following about backup encryption:
The Encrypt backup feature in iTunes locks and encodes your information. Encrypted iTunes backups can include information that unencrypted iTunes backups don’t:
- Your saved passwords
- Wi-Fi settings
- Website history
- Health data
The first item is the most important. To tell you the truth, saved password are included in unencrypted backups as well (despite what Apple says), but the thing is. they are encrypted with a hardware-specific key. This in turn means that you can only restore such a backup exactly onto the same device you’ve captured the backup from – otherwise, saved passwords will be lost for goods. Of course you can use the iCloud keychain, but the fact is some keychain items are not synced with the iCloud.
By the way, if you encrypted the iTunes backup and know the password, you can view all the passwords stored in the iOS keychain using Elcomsoft Phone Breaker.
 Resetting backup passwords
Resetting backup passwords
So we figured the backup password is a secure way to protect its content. We also figured that the password is the property of the device. What happens if you’ve lost the password?
If the iPhone is still in your hands and runs a fairly recent version of iOS, you should be able to reset the password. Here is how (from the same article on encrypted backups we already mentioned):
You can’t restore an encrypted backup without its password. With iOS 11 or later, you can make a new encrypted backup of your device by resetting the password. Here’s what to do:
- On your iOS device, go to Settings > General > Reset.
- Tap Reset All Settings and enter your iOS passcode.
- Follow the steps to reset your settings. This won’t affect your user data or passwords, but it will reset settings like display brightness, Home screen layout, and wallpaper. It also removes your encrypted backup password.
- Connect your device to iTunes again and create a new encrypted backup.
Sounds good, right? Not exactly.
There is a big caveat to resetting All Settings on an iPhone. This operation has an important impact you should be aware of: it also resets the device passcode (screen lock password). That means that you will also lose Apple Pay transactions and downloaded Exchange mail (if it was there). Moreover, if a given device is connected to an iCloud account with two-factor authentication enabled, then you will not be able to change this account settings from the device without entering a separate Apple ID password because the passcode is removed.
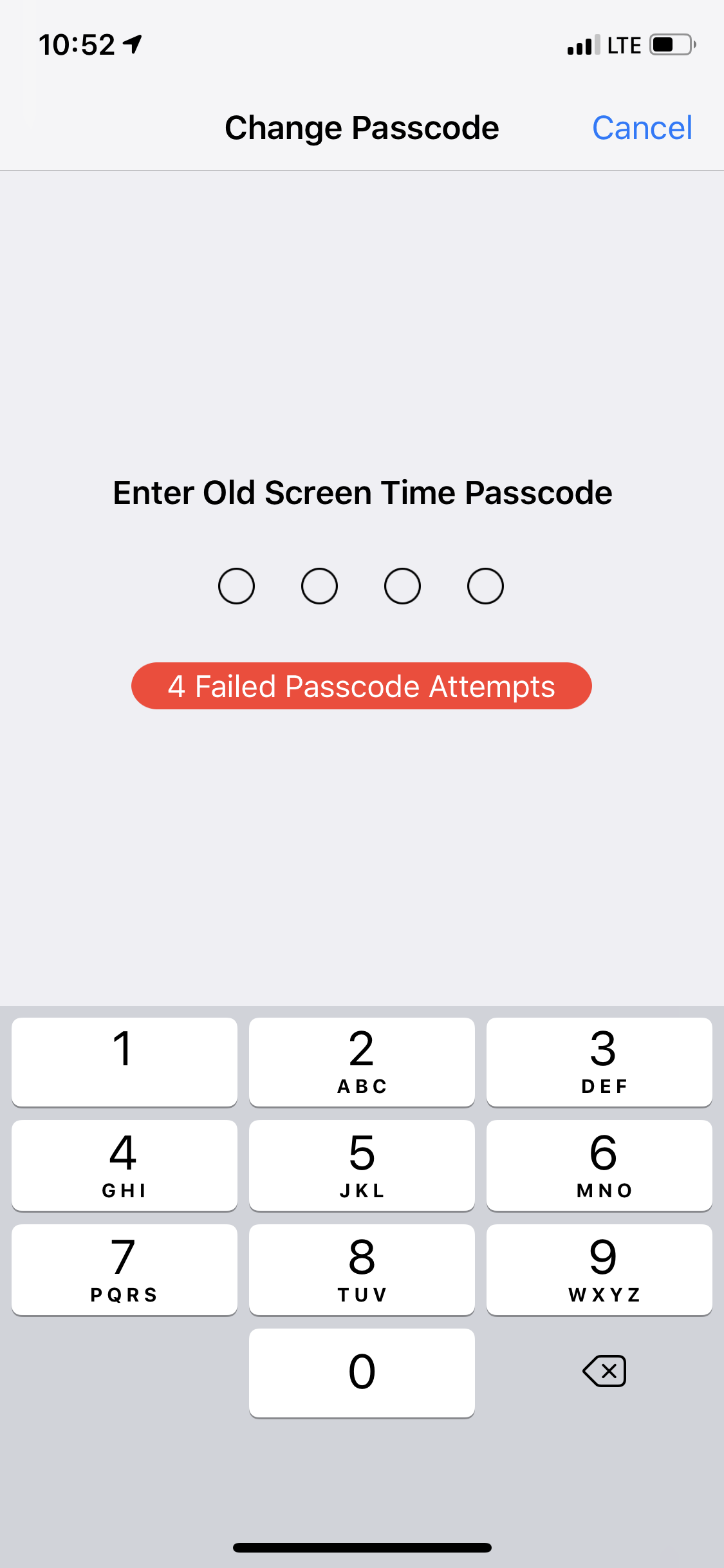
Starting with iOS 7, there is a way to set restrictions on the iPhone. Restrictions protect some options from unauthorized changes (some other operations can be also limited). With iOS 12, there is no restrictions password anymore, but there is a new Screen Time feature that is quite similar. More on that here:
What does it mean for you? You will not be able to use the Reset All Settings command to reset the backup password unless you know that (Restrictions or Screen Time) password. What if you forgot it, too? You have 6 tries to enter the Restrictions (Screen Time) password with no delay, then wait for one minute, than 5 minutes etc. The wait peaks at one hour after 10 unsuccessful attempts. The iPhone will not lock you out as it happens with the device passcode, but obviously you cannot try all 10,000 combinations at one password an hour.
Thinking outside the backup
If you pair the iPhone to the computer, can you access anything other than backups? There quite a few things accessible in addition to backups.
First, you can extract all media files (photos and videos) regardless of whether or not the backup is password-protected. You can also obtain shared files (many applications use that feature to allow using by several applications, one example is Microsoft Office). And finally, you can get crash and diagnostics logs (that feature is of special interest to mobile forensic specialist). That can be done with Elcomsoft iOS Forensic Toolkit. To tell you the truth, most of this data can be accessed “manually” as well – using Explorer (Windows) or Image Capture (macOS), XCode and iTunes, but it won’t be that easy. By the way, all of that data (including media, logs and shared files) can be also acquired from an Apple TV and Apple Watch, but this time you will definitely need the software (iOS Forensic Toolkit).
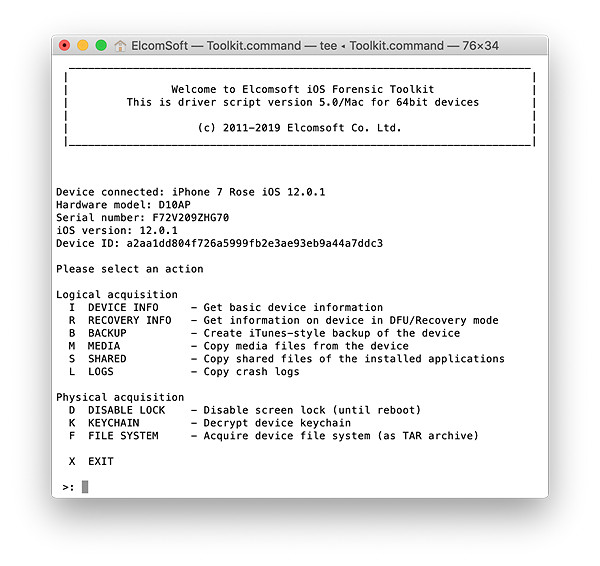 Finally, you can always attempt to make a fresh iCloud backup. In fact, it contains less data than an iTunes backup, e.g. your photos are not always there (if iCloud Photos is used), and messages could be missing if you opted for storing messages in iCloud.
Finally, you can always attempt to make a fresh iCloud backup. In fact, it contains less data than an iTunes backup, e.g. your photos are not always there (if iCloud Photos is used), and messages could be missing if you opted for storing messages in iCloud.
Jailbreaking to the rescue?
Surprisingly, jailbreaking an iPhone could be the solution to the “lost backup password” problem. At the moment, jailbreaks are available for all iOS versions up to iOS 12.1.2 (and there is a good chance for iOS 12.1.3-12.3 jailbreak soon). The point? You will get the complete contents of the iPhone, including files that are not available in a backup: downloaded mail, location data, app-specific data and much more. And the full keychain contents as a bonus, including… the iTunes backup password!
It’s not even all that difficult; you can read Step by Step Guide to iOS Jailbreaking and Physical Acquisition for more information. If you are doing that as part of your forensic work, please also make sure to read Forensic Implications of iOS Jailbreaking.
Locked phones?
A backup can be created if the iPhone is locked with a passcode. You can do that if you have access to a computer that has established trusted relationship with the iPhone in question. In addition, the iPhone must’ve been unlocked at least once after the last reboot. More on that here:
That will not work, however, if USB Restricted Mode was activated.
Conclusion
Creating a backup of your iPhone is not just a good idea. I’s a brilliant idea and a must do, really. Just imagine you lost your iPhone: just syncing it to your iCloud account (as Android users do) is usually not enough to restore everything. Apart of the usual “choose strong passcode, enable 2FA and USB Restricted Mode, and familiarize yourself with the S.O.S. combination on your particular device and get ready to use it in a case of emergency” mantra, we strongly recommend you to do two things. First, make sure to enable iCloud backups (we know, it would be tough with only 5 GB of storage you’ve got from Apple for free. If you can afford an iPhone, buy some more iCloud storage as well.) With iCloud backups, you’ll have two snapshots, which means you might be able to restore accidentally deleted data if needed. Second, make a habit of creating iTunes backups on a regular basis, and make sure to protect them with a password that you can memorize. We don’t mind if you save that password in a safe place 😉
Elcomsoft Distributed Password Recovery, Elcomsoft iOS Forensic Toolkit, Elcomsoft Phone Breaker, Elcomsoft Phone Viewer, iCloud, iOS, iOS backups, iTunes, iTunes backups, jailbreak, keychain







