Smartphones are frequent theft targets. Manufacturers try to combat smartphone theft by implementing several security measures. The first security measure is “remote kill switch”, a feature allowing legitimate owners to block, disable or erase a smartphone in a case it is stolen. Since Aug 12, 2014, the “kill switch” is mandatory in California in all new smartphones manufactured after July 1, 2015. Other jurisdictions followed, passing legislations with “kill switch” requirements to combat smartphone theft.
Long before legislations, the “remote kill switch” was used by companies to allow remotely erasing the phone’s content. Apple’s Find My iPhone, Microsoft’s Find My Phone, BlackBerry Protect and Android Device Manager allowed locating, ringing, blocking or erasing the phone remotely. However, the “kill switch” was originally designed to only protect the phone owner’s data, but could not help discourage theft. The criminal would simply erase the phone by performing factory reset, and resell the device. IMEI blacklisting aside, a simple factory reset would result in a clean, usable device, continuing to provide incentive for the criminals.
It took manufacturers much longer to implement true anti-theft protection in their core OS. In today’s state, anti-theft protection is a combination of your familiar remote kill switch and factory reset protection.
Factory reset protection is a security method designed to make sure your smartphone becomes useless if the thief wipes your smartphone. If someone wipes and factory resets your device without providing your authentication credentials, a smartphone equipped with factory reset protection would cease to initialize, display a prominent message asking to enter previous owner’s account credentials, and block further initialization attempts.
In theory, this sounds great. The implementation of the “kill switch” helped reduce smartphone theft by as much as 40 per cent. But is smartphone protection as secure as we think? Let’s find out.
Apple iOS
Summary:
- Factory Reset Protection: yes, on all current devices
- Remote kill switch since: iOS 4.2 (November 2010)
- FRP supported since: iOS 6 (September 2012) https://en.wikipedia.org/wiki/Find_My_iPhone
- Coverage: global
- Rollback protection: yes
- Removing FRP: unlock iPhone; disable Find My iPhone; Apple ID password required
- Security status: impeccable
iOS is a closed system that is fully controlled by Apple. In reasonably recent versions of iOS there are no known ways to bypass the setup wizard. With Apple’s centralized update policy, most iPhones worth stealing are running the latest iOS anyway.
In iOS, the “kill switch” is enabled automatically out of the box. The setting is located under iCloud – Find My iPhone:
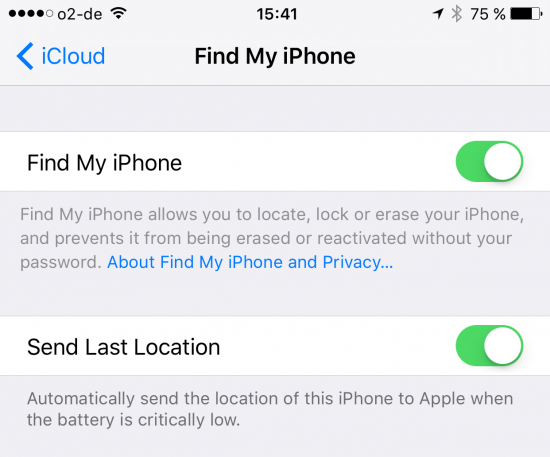
If your iPhone is lost it or stolen, the thief will be unable to initialize the device without providing your Apple ID and password. If you sell your iPhone, you’ll have to disable the “Find my iPhone” feature prior to resetting the device; otherwise, the buyer will be asked to log in with your Apple ID and password before they can start using the phone. In order to disable FRP, you will need to perform three steps:
- Unlock your iPhone (passcode or fingerprint)
- Turn off Find My iPhone in the Settings
- Enter your Apple ID password
Importantly, factory reset protection will only be disabled after you enter the correct Apple ID password. Simply unlocking the phone and switching the setting off will not be enough.
In our research, we have found no way around factory reset protection. With global coverage, Apple did an exemplary job protecting their users.
Android
Summary:
- Factory Reset Protection: on some devices (devices running Android 5.1 or higher that came preinstalled with Android 5.0 or higher) via Google Services
- Remote kill switch: optional via Android Device Manager (December 2013), Android 2.2 and up
- FRP supported since: Android 5.1 (February 2015)
- Coverage: global
- Rollback protection: depends on vendor and bootloader status
- Disabling FRP: unlock device; remove Google Account (password not required)
- Security status: bypassing is “so simple that even a seven-year-old could follow” (Android Authority)
- Special note:
Starting with Android 5.1, Google includes factory reset protection in Google Android. You read it right: only “Google Android” devices equipped with Google’s proprietary GMS receives anti-theft protection. Non-Google Android (such as custom ROM’s or the whole lot of Android devices sold in China) lack this feature entirely regardless of Android version (vendors may use their own implementations).
Google only advertises coverage in devices running Android 5.1 or higher that came preinstalled with Android 5.0 or higher (https://support.google.com/nexus/answer/6172890?hl=en). With many Android features being highly OEM-dependent, not all OEMs chose to implement factory reset protection in their devices, especially those that came preinstalled with Android 4.4 and earlier.
In Android 5.1 and newer, factory reset protection is automatically activated (if supported) if two conditions are met:
- The user has their lock screen set to something other than “none” or “swype”. Enabling PIN, passcode or pattern lock is required for the feature to activate.
- The user adds at least one Google Account to the device. In a case the device is erased, factory reset protection will require signing in with that Google Account during initialization.
Notably, there is no special setting to activate, enable or disable factory reset protection. There is no place in the Settings to see whether your device is protected or not.
Once the Android device with active FRP is erased (via device settings, by booting into recovery or by using Android Device Manager), the following prompt will appear when setting up the device:
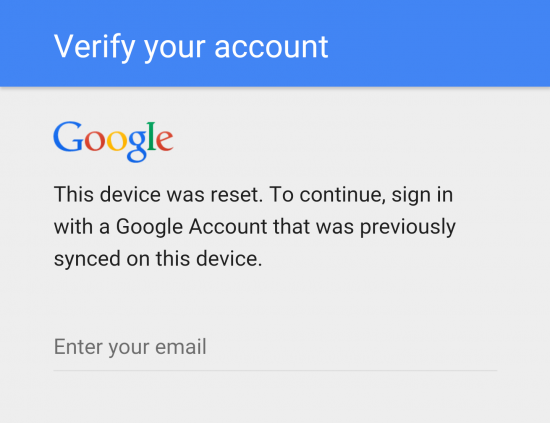
You will then have to sign in with the main Google Account that was used on the device preceding factory reset. If two-factor authentication is enabled, you will need to supply a one-time code as well.
Google implements an interesting (and unique) additional security measure. If you change your Google Account password and perform a factory reset, you will be unable to activate the device during the first 24 hours (this used to be 72 hours; apparently, Google reduced the wait period after receiving a large number of support calls). For security purposes, you cannot use an account to set up a device after factory reset if that password was changed within 24 hours (source: https://support.google.com/nexus/answer/6172890?hl=en)
One common misconception with Google Device Protection (the name the company uses for Factory Reset Protection) is the affect of the “OEM unlocking” function. If your device comes with unlockable bootloader, you will have to trigger a switch in the Developer options in order to allow bootloader unlock. When you trigger the switch (you’ll have to perform your usual screen unlock procedure here, be it entering a PIN or using an unlock pattern), you’ll see the following prompt:
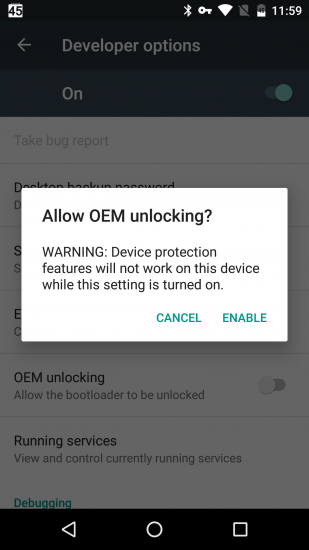
The prompt specifically states that allowing OEM unlocking disables device protection features, which makes one think that activating OEM unlocking disables factory reset protection. This is not true: while enabling OEM unlock allows someone to flash a different build of Android (or a custom ROM) that may not enforce factory reset protection (and thus making the phone usable to a thief), enabling this feature does not disable FRP by itself. In other words, if you need to sell your Android device, you will need to remove your Google Account in order to disable FRP. If you simply trigger “OEM unlock” and do a factory reset, the new owner will still be required to log in with your Google Account credentials to activate the device (unless they are willing to unlock bootloader and flash a custom ROM image to bypass FRP).
As you can see, in the land of Android factory reset protection is not an absolute. At very least, one can bypass it by unlocking bootloader and flashing a custom ROM. But what if the bootloader is locked, and no custom ROM images are available? Even then, there are many known exploits allowing to bypass factory reset protection on Android smartphones.
For example, on some Samsung smartphones one can launch the Setup wizard from a USB OTG flash drive, effectively bypassing reset protection because Samsung File Explorer pops up automatically (even during initialization) if you plug an OTG drive. Devices running all versions of Android 5.1 and 6.0.1 (even those with January 2016 security patch) are also susceptible. One can easily bypass the Setup Wizard (and skip FRP) by following simple instructions: http://www.androidauthority.com/factory-reset-protection-bypass-nexus-marshmallow-680580/
The issue was still unpatched in the first beta of Android ‘N’. “This is clearly a serious issue with Factory Reset Protection. If phone thieves with no technical skills can bypass FRP, it negates the entire purpose of the feature, theft deterrence”, says Android Authority http://www.androidauthority.com/factory-reset-protection-bypass-nexus-marshmallow-680580/. “It’s so simple that even a seven-year-old could follow”. That’s all you need to know about Android Factory Reset Protection.
More: http://www.androidcentral.com/factory-reset-protection-what-you-need-know.
Windows Phone 8.1 and Windows 10 Mobile
Summary:
- Factory Reset Protection: on some devices (US only for newer devices running Windows Phone 8.1 GDR2 and newer, Windows 10 Mobile)
- Remote kill switch: optional via Find My Phone (Windows Phone 8 and up)
- FRP supported since: Windows Phone 8.1 Update 2 build 8.10.15127.138 (February 2015)
- Coverage: USA only (https://www.microsoft.com/en-us/mobile/support/faq/?action=singleTopic&topic=FA144486)
- Rollback protection: yes
- Disabling FRP (Windows Phone 8.1): unlock device; navigate to About – Reset your phone; you will be prompted for your Microsoft Account password before you perform factory reset.
- Disabling FRP (Windows 10 Mobile): unlock device; turn off Find My Phone – Reset Protection (you’ll be prompted for your Microsoft Account password).
- Disabling FRP (online): log in to Microsoft Account at microsoft.com/devices, click I don’t own this phone anymore, make note of recovery key, send that key to the new owner.
- Checking reset protection status: https://account.microsoft.com/devices/resetprotection
- Security status: no known bypass methods; insufficient research
In the world of smartphones, Microsoft is a clear outsider. With less than 4% share of the smartphone market, few would even care about factory reset protection in Windows devices. Consider the fact that most Windows smartphones in use are low-end offerings (think Lumia 640, a $29 AT&T GoPhone), and you’ll find that very few would actually care.
Still, Microsoft had to comply with legislations requiring manufacturers implement a compulsory kill switch in newer smartphones. For this reason, Microsoft added reset protection to their newer devices running fairly resent versions of Windows. However, the company didn’t bother for global coverage. Instead, they chose to only enable reset protection in devices sold in the US (https://www.microsoft.com/en-us/mobile/support/faq/?action=singleTopic&topic=FA144486) – and skip it entirely in their global offerings.
Notably, factory reset protection must be enabled on the device during manufacturing time.
According to Microsoft https://sysdev.microsoft.com/en-us/Hardware/oem/docs/Manufacturing_Retail/Reset_protection, Reset Protection consists of the following parts:
- Reset and reactivation protection – The stolen device cannot be reused by resetting or flashing the device. When a user performs a factory reset on the device, they will be asked to enter the Microsoft Account credentials that are associated with that device. Additionally, if the device is flashed with a new image and Reset Protection is turned on, the Microsoft Account credentials that were associated with that device is required to finish OOBE and use the device.
- Anti-rollback protection – If Reset Protection is enabled, the stolen device cannot be flashed to an earlier version of the operating system that did not support Reset Protection.
(source: https://sysdev.microsoft.com/en-us/Hardware/oem/docs/Manufacturing_Retail/Reset_protection)
Windows Phone 8.1 and Windows 10 Mobile use online factory reset protection through Microsoft Account. In order to disable FRP, you will inevitably need to provide the correct Microsoft Account password. Procedures of disabling FRP differ between Windows Phone 8.1 and Windows 10 Mobile. (Source: http://www.windowsphone.com/en-us/how-to/wp8/settings-and-personalization/protect-my-phone)
- Windows Phone 8.1: in order to disable FRP, unlock the device and navigate to About – Reset your phone. Before performing factory reset, your phone will prompt for your Microsoft Account password. Note that this only works in devices that support Reset Protection (US devices running Windows Phone 8.1 Update 2 build 8.10.15127.138 or newer).
- Windows 10 Mobile: you can disable FRP without performing a factory reset by unlocking your device, navigating to Find my phone and toggling the Reset Protection You’ll still need your Microsoft Account password.
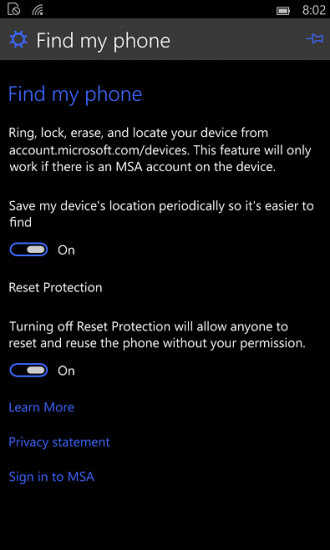
If you no longer possess the phone but want to disable FRP (e.g. you sold the device), you can do so by navigating to account.microsoft.com/devices and signing in with your Microsoft Account. You’ll see the list of devices. From there, follow Microsoft instructions (source: http://windows.microsoft.com/en-us/windows/protect-my-phone):
To turn off Reset Protection when you no longer own the phone
If someone has received your phone and you didn’t turn off Reset Protection, the recipient won’t be able to set up the phone. Here’s what you can do:
- Go to account.microsoft.com/devices.
- Next to the phone you no longer own, select Remove phone.
- Select the I’m ready to remove my phone check box, note the recovery key, and then select Remove. The recovery key will display on the page and will also be emailed to you.
- When you’re certain that you have your recovery key saved, select the I’ve kept a copy of the recovery key check box, and then select Okay.
- Forward the recovery key email to your phone recipient.
Your phone is no longer listed on account.microsoft.com/devices, and the recipient can remove Reset Protection during phone set up using the Disable using recovery key option.
You can also check Reset Protection status of any Windows smartphone by simply entering its IMEI number (Microsoft Account password is not required to check protection status): https://account.microsoft.com/devices/resetprotection
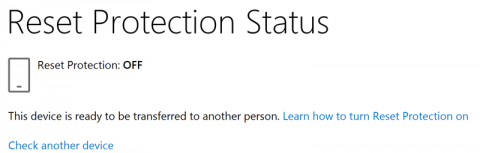
At this time, there are no known ways to bypass FRP in Microsoft devices. However, very little research was done due to the limited number of Windows Phone 8.1 and Windows 10 Mobile devices. For one thing, some Lumia phones are susceptible to bootloader exploit that allows bypassing UEFI security and loading a version of the OS that does not support anti-theft protection.
BlackBerry 10
Summary:
- Factory Reset Protection: yes, on all current devices
- Remote kill switch since: initial release
- FRP supported since: BlackBerry 10 OS version 10.3.2 (June 2015)
- Coverage: global
- Rollback protection: yes; can be bypassed with developer builds
- Removing FRP: unlock BB 10 device; disable BlackBerry Protect; BlackBerry ID password required. Alternatively, sign in to protect.blackberry.com and remove device from the list.
- Security status: can be bypassed on all models by flashing developer firmware
- More information: http://helpblog.blackberry.com/2015/06/getting-started-with-anti-theft-protection-in-blackberry-10-os-version-10-3-2/
BlackBerry smartphones are renown for their security. Data security was always top priority for the company. As a result, the BlackBerry Protect service allowing to remotely locate and erase devices was made available as soon as BlackBerry 10 devices hit the market.
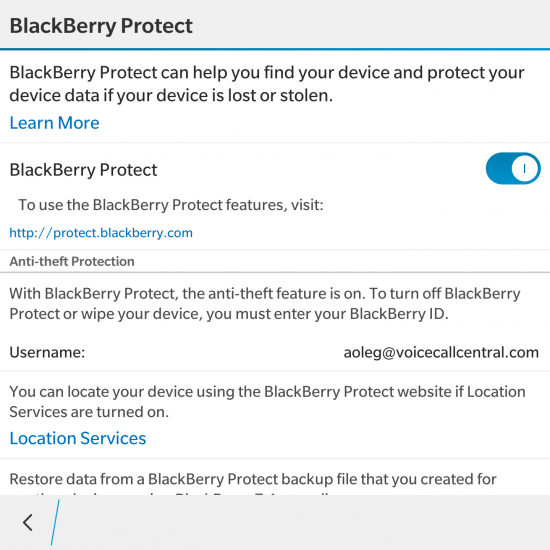
It was not before June 2015 (BlackBerry 10 OS version 10.3.2) when BlackBerry added factory reset protection (dubbed as “Anti-Theft Protection” in BlackBerry marketing materials). BlackBerry’s implementation is similar to what Apple does. If a device is reset without first deactivating BlackBerry Protect, the user would have to sign in with the previous owner’s BlackBerry ID in order to initialize the phone. If that is not available, or if a given BlackBerry ID is deleted, the device is toasted.
BlackBerry devices are unique in that they can be easily flashed to any version of BlackBerry 10. Flashing the device is as easy as downloading an appropriate Autoloader tool (a large .exe that contains all the required firmware, the OS itself, and everything that is needed to flash the phone). Simply launching the autoloader while the phone is connected to the computer erases its content and loads a fresh system. The process is extremely fast and easy, and takes minutes to complete.
With older versions of BlackBerry 10 freely available, rollback protection was essential. BlackBerry implemented such protection by disabling downgrades to any version of BlackBerry 10 lower than 10.3.2. With is no official way to roll back to an earlier version of BlackBerry 10, this system appeared solid for a long while.
Unfortunately, BlackBerry left a backdoor, effectively rendering rollback protection (and its entire factory reset protection implementation) useless. An autoloader containing an old developer build of the OS can be flashed onto the device. This early developer build does not feature Anti-Theft Protection, making it possible to activate the device with a new BlackBerry ID. Devices activated with a new BlackBerry ID can be successfully updated to the current version of BlackBerry 10. Sigh. So much for “the most secure mobile OS on the market”.
Conclusion
As we can see, the chain is only as strong as its weakest link. After reviewing anti-theft protection implemented by Apple iOS, Google Android, Microsoft Windows Phone 8.1 and Windows 10 Mobile, and BlackBerry 10. According to our research, Apple comes out first with solid protection coverage around the globe.
Microsoft offers protection to some newer devices in the US, but lacks any sort of device protection on international markets. Besides, bootloader exploits exist for some models, potentially allowing to install Windows versions without anti-theft protection.
The Android platform is highly fragmented. With so many “ifs” and “buts” and several published video tutorials on bypassing device protection that can be followed by a seven year old, the whole effort is a bad joke.
BlackBerry 10, once marketed as the most secure mobile OS, has a nasty backdoor rendering the entire anti-theft system ineffective.
Our take? If your phone offers anti-theft protection, by all means use it. If it gets stolen, wipe it and call your mobile provider and get its IMEI blacklisted.








