As you may already know from the official press release, we’ve recently updated Elcomsoft Phone Breaker to version 4.10. From that release, you could learn that the updated version of the tool targets passwords managers, adding the ability to instantly decrypt passwords stored in BlackBerry Password Keeper for BlackBerry 10 and attack 1Password containers.
If you read along the lines though it’s a different story.
Essentially, we’ve discovered a backdoor hidden in recent versions of BlackBerry Password Keeper allowing us to decrypt the content of that app instantly without brute-forcing the master password. For our customers, this means instant access to passwords and other sensitive information maintained by BlackBerry Password Keeper. No lengthy waits and no fruitless attacks, just pure convenience. But is this convenience intentional? Did BlackBerry leave a backdoor for government access, or is this an unintentional vulnerability left by the company renowned for its exemplary security model? Let’s try to find out.
Old versions of BlackBerry Password Keeper were relying upon a user-selectable master password to protect access to the user’s sensitive information. Old versions of Elcomsoft Phone Breaker had to attack that password with all the brute force (and a bit of brain force) we had at our disposal. Whether or not we’d be able to break in would depend on how much we knew about the password and on how long and complex that password was.
This was about to change. And it did. Recent versions of the Keeper app continue using the master password. But that’s on the surface. In addition to the master password, BlackBerry Password Keeper now makes use of an escrow key. That escrow key is stored in BlackBerry 10 backups alongside the data. Notably, BlackBerry 10 backups are encrypted, and must be decrypted with Elcomsoft Phone Breaker (using the correct BlackBerry ID and password) in order to gain access to Password Keeper data.
Elcomsoft Phone Breaker 4.10 adds support for the latest version of BlackBerry Password Keeper, enabling the extraction of escrow keys and instant decryption of the protected container. Note that BlackBerry 10 backups containing BlackBerry Password Keeper containers are also encrypted, and must be decrypted with ElcomSoft Phone Breaker using the original BlackBerry ID and password prior to accessing BlackBerry Password Keeper data.
BlackBerry Password Keeper makes use of AES 256 to encrypt information. However, the choice of the algorithm itself does not mean much in terms of how secure the product is going to be. In order for the product to be secure, every stage must be properly implemented, and there must be no backdoors that could render the entire protection scheme pointless.
Now let’s pause for a moment and look at the following screenshot of a BlackBerry phone.
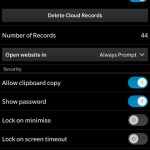
Password Keeper has Cloud Synchronization? BlackBerry claims that one can restore the full Password Keeper contents onto a new BlackBerry device provided that the same BlackBerry ID and the same Master Password are used. Now, we know for sure there is an escrow key to that (you can verify that easily by downloading Elcomsoft Phone Breaker 4.10 and processing a BlackBerry 10 backup with a Password Keeper container). Is this escrow key exported to the cloud alongside the data? We don’t know. All we do know that there is an escrow key, and that that key is stored alongside Password Keeper data in BlackBerry 10 backups. We are not suggesting that BlackBerry has intentionally left this backdoor for the convenience of the government. We don’t know if that escrow key ever leaves the device (other than being stored in offline backups) or gets synced to the cloud. However, *if* the escrow key is synced to the cloud, then BlackBerry Inc. would have no technical problem accessing all passwords and other data stored in the Password Keeper. Neither would the government.
1Password: Any Better Than BlackBerry Password Keeper?
With an average user having more than 30 accounts, the use of password managers is on the rise. That’s why we decided to add support for two popular password keepers: BlackBerry Password Keeper for BlackBerry 10 and the multi-platform app 1Password. How do the two password managers compare?
1Password is a popular multi-platform password manager. Available for Windows, Mac, Android and iOS devices, 1Password is used to store and synchronize passwords by millions of users. 1Password can use Dropbox or iCloudDrive to keep passwords. iOS devices can back up 1Password containers to local or iCloud backups. The data is protected with a user-selectable master password. Elcomsoft Phone Breaker can attack the password and decrypt 1Password containers, revealing all of the user’s stored passwords.
Interestingly, 1Password uses a bunch of different formats, so containers stored in Dropbox, iCloudDrive, iTunes and iCloud backups are different.
Is 1Password secure, or did we manage to break it? So far we’ve discovered no escrow keys to allow us unlocking 1Password containers. It’s still good old brute force and brainwork. In a sense, we have a feeling that 1Password is even more secure than BlackBerry Password Keeper.
Unlike many (most, in fact) password managers, 1Password discloses full technical information about its data format, which security experts consider to be the best practice.
So what happens if an attacker gains access to someone’s 1Password database? If the password is reasonably complex and strong enough to not make it into the Top 10000 Passwords List, the stolen database will be of little use to the attacker:
While some reports claim that up to 98.8% of users choose passwords from the Top 10000 Passwords List, we have a hard time believing their statistics.
Your average password manager is not nearly as secure as 1Password. We researched a number of mobile password managers only to discover that most of them have no security whatsoever despite claims to the contrary.
What Else Is New
It’s difficult to underestimate the convenience of over-the-air acquisition. However, the need to know the user’s Apple ID and password, as well as the obstacles presented by Apple’s two-factor authentication made the process difficult. In one of the previous builds, Elcomsoft Phone Breaker introduced the ability to access iCloud accounts without using the login and password – and without getting stopped by Apple’s two-factor authentication. We used binary authentication tokens instead. Those were the very tokens saved by iCloud Control Panel to free the user from re-entering their password every time they wanted to sync with the cloud.
Extracting those tokens was not exactly straightforward, so we made command-line tools for Windows and Mac. At first, we could only work with live systems. Later on, we added support for hard drives and forensic disk images. But experts still had to use the command line.
Elcomsoft Phone Breaker 4.10 finally gets rid of the command line. The new version integrates the ability to extract iCloud authentication tokens directly into the user interface instead of relying on command-line tools.
In this release, we significantly improved password recovery speed when using NVIDIA boards due to low-level code optimizations. We can now say that Elcomsoft Phone Breaker reached theoretical maximum performance when performing GPU-assisted password recovery with NVIDIA boards. Compared to previous versions, the performance grows some 15 to 20 per cent. To reach this performance level, we worked together with NVIDIA engineers who helped us squeeze the last bit of performance out of their hardware.
Other news include scalable UI with support for Retina displays.