Finally, TAR support is there! Using Elcomsoft iOS Forensic Toolkit to pull TAR images out of jailbroken iOS devices? You’ll no longer be left on your own with the resulting TAR file! Elcomsoft Phone Viewer 3.70 can now open the TAR images obtained with Elcomsoft iOS Forensic Toolkit or GrayKey and help you analyse evidence in that file. In addition, we added an aggregated view for location data extracted from multiple sources – such as the system logs or geotags found in media files.
What Are These TAR Files Anyway?
While TAR is just an uncompressed file archive used in UNIX-based operating systems, this speaks little of its importance for the mobile forensic specialist.
Since the introduction of the iPhone 5s, Apple’s first 64-bit iPhone, physical acquisition has never been the same. For all iPhone and iPad devices equipped with Apple’s 64-bit processors, physical acquisition is exclusively available via file system extraction because of full-disk encryption. Even with a jailbreak, you must run the tarball command on the device itself in order to bypass the encryption. Since the file system image is captured and packed by iOS, you’ll get exactly the same TAR file regardless of the tool performing physical acquisition. Whether you use iOS Forensic Toolkit or GrayKey, you’ll receive exactly the same TAR archive containing an image of the device’s file system.
One of the questions we’re frequently asked is: what can we do with that TAR file? Up until now, most tools available for analysing information inside these TAR images were integral parts of fully-featured forensic toolkits. Your options would be limited to either time-consuming and labour-intensive manual analysis requiring a high level of expertise, or a highly sophisticated and complex forensic suite, with nothing in between.
This is where Elcomsoft Phone Viewer 3.70 comes. The tool offers a perfect alternative to both the manual analysis and the use of sophisticated forensic packages. With Elcomsoft Phone Viewer, you can access call logs, contacts and message databases, notifications, browsing history, and of course location data.
Why TAR Files Are Important?
Compared to logical acquisition, physical offers tangible benefits. At very least, you get all of the following in addition to what you’d see in a backup:
- Notifications. Undismissed notifications used to be part of a backup, yet iOS 11 got rid of them. Today, you can only extract notifications from a TAR file. Notifications may contain critical evidence that would be otherwise unavailable, such as notifications from email accounts, social networks, banking and travel apps, taxi applications and much more.
- Applications. In iOS, developers have control over what information gets backed up. Even if they opt to allow a backup, the developer may choose to make the data available to same device only – meaning it’ll be encrypted with a hardware key that would be impossible to crack even with a jailbreak. The TAR file solves this problem by allowing unrestricted access to apps’ sandboxed data. Elcomsoft Phone Viewer displays the list of installed packages and shows the exact location of each app’s data.
- Locations. You can expect to see a lot more location data in a TAR file compared to a backup.
Speaking of locations, EPV 3.70 can extract location data from a wide range of sources. At this time, the sources include:
- Significant locations (what are those?)
- Locations cache (3G/LTE/Wi-Fi connections)
- Apple Maps
- Google Maps
- EXIF in media files, including the ID of the device that was used to capture the image
- Calendar events, including the link to the event
- The UBER app
By accessing location data gathered from such a wide range of sources, you are no longer limited to evidence collected from just the location logs. Some sources are only available with physical extraction (TAR files), and some data may be limited when analyzing backups. The number of supported sources of location data will be growing in future releases of Elcomsoft Phone Viewer.
When Locations Can Lie
When analysing location data, do note that you cannot blindly trust everything reported by the tool. For example, locations will be extracted from all images on the device, and not just those captured by that device. The user may receive image as email or instant messaging attachments, while calendar events could be automatically added without the user ever attending. Locations cache lists approximate coordinates of the nearest base station, while Wi-Fi coordinates are retrieved with a third-party service based on the access point’s MAC address; this data should generally be questioned as hard evidence. Finally, Significant Locations are great, but are derived with a closed-source algorithm. However, Significant Locations are among the more reliable indicators of the user’s actual location, albeit without a time stamp.
Analyzing TAR Files with Elcomsoft Phone Viewer
Enough theory, let’s check out a TAR file opened in the latest Elcomsoft Phone Viewer!
Before you begin, make sure you are using the Forensic edition of Elcomsoft Phone Viewer, which can be purchased separately and is included with Elcomsoft Mobile Forensic Bundle. The Standard edition cannot open TAR files. Quite obviously, you’ll also need a TAR file obtained during the course of physical extraction with Elcomsoft iOS Forensic Toolkit or GrayKey.
- Launch Elcomsoft Phone Viewer. Compared to the previous version, you’ll see a new icon that reads “iOS device image”. Click on it to open a TAR file.
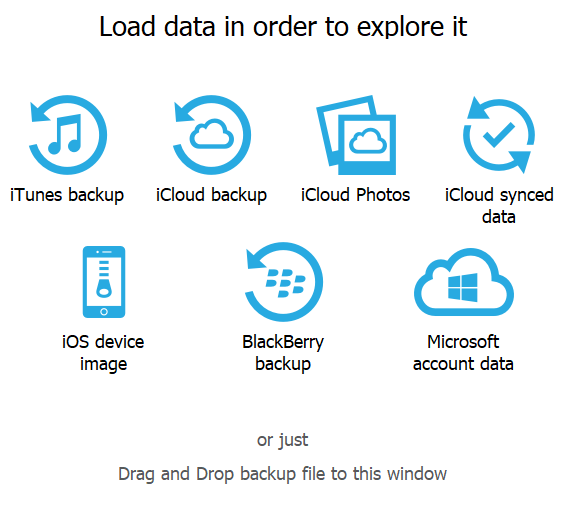
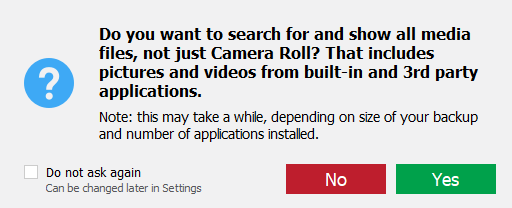
- Select the TAR file. Once the tool opens the file, you’ll see a prompt asking you whether you want to scan locations other than the Camera Roll for media files that may contain location data. Depending on the number of such files, the time required to open the TAR file may grow.
- The archive will be unpacked. Unpacking an 11 GB image takes approximately 2 minutes on a fast computer.
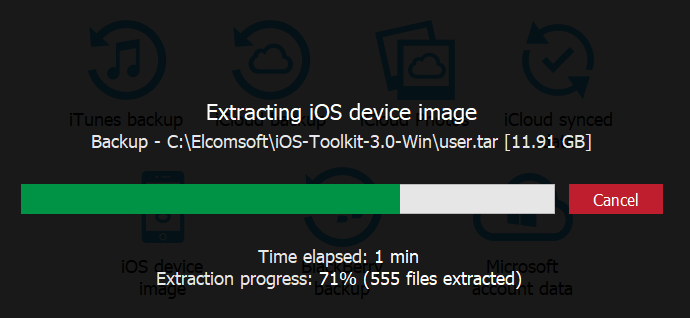
- The file will be processed to discover and index evidence. This may take a few more minutes.
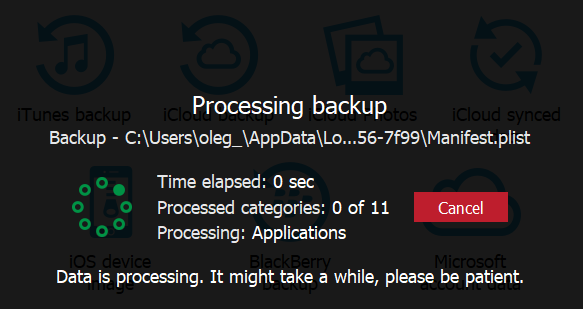
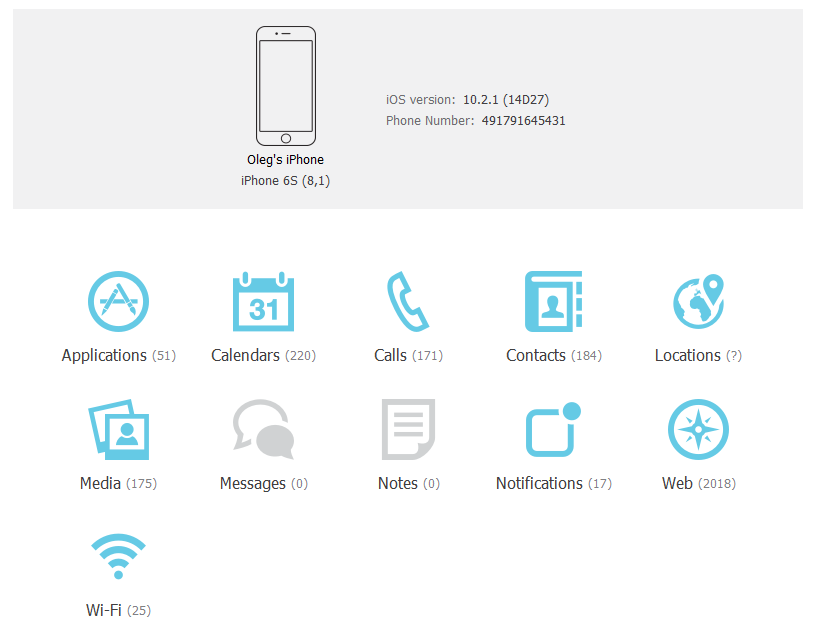
- Finally, you’ll be able to access evidence! If you’re concerned with one or more question marks instead of the number of items (like the one in front of “Locations” in the example below), do note that this is due to background processing of the data. Once you open the corresponding category, EPV will resolve the number of entries.

So what’s inside? First, the list of installed apps:
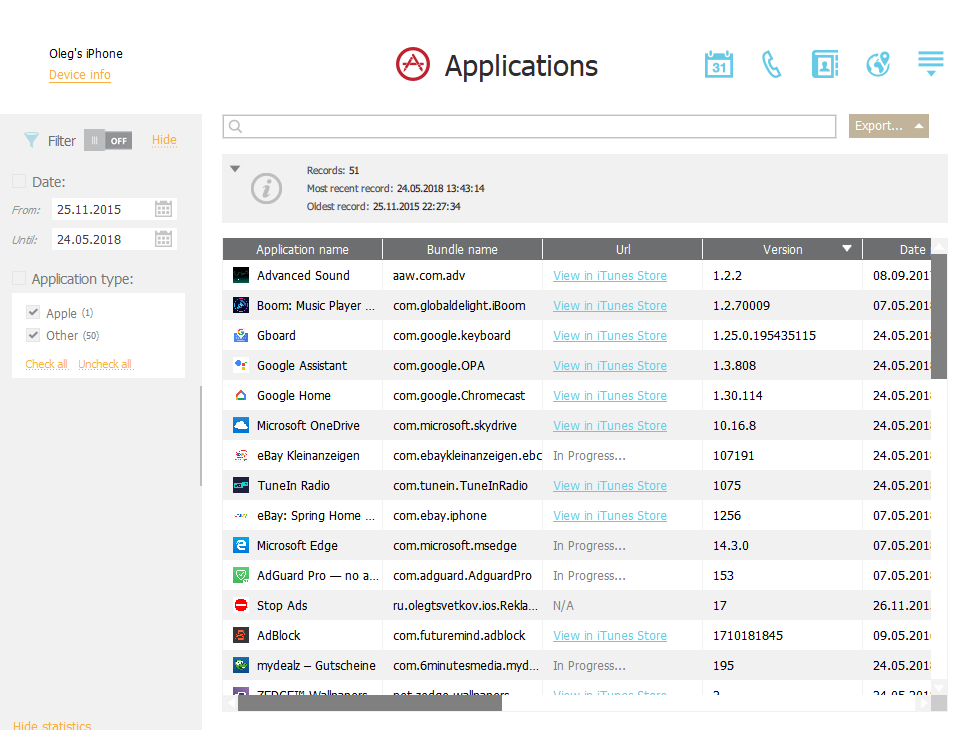
If your computer has Internet access, you’ll be prompted to allow matching package names against iTunes database. This allows seeing the actual name of the app as opposed to the name of the package.
If you want to access a data set of a particular app, scroll to the rightmost column, which contains information about the full path to the app’s data set in the TAR archive.
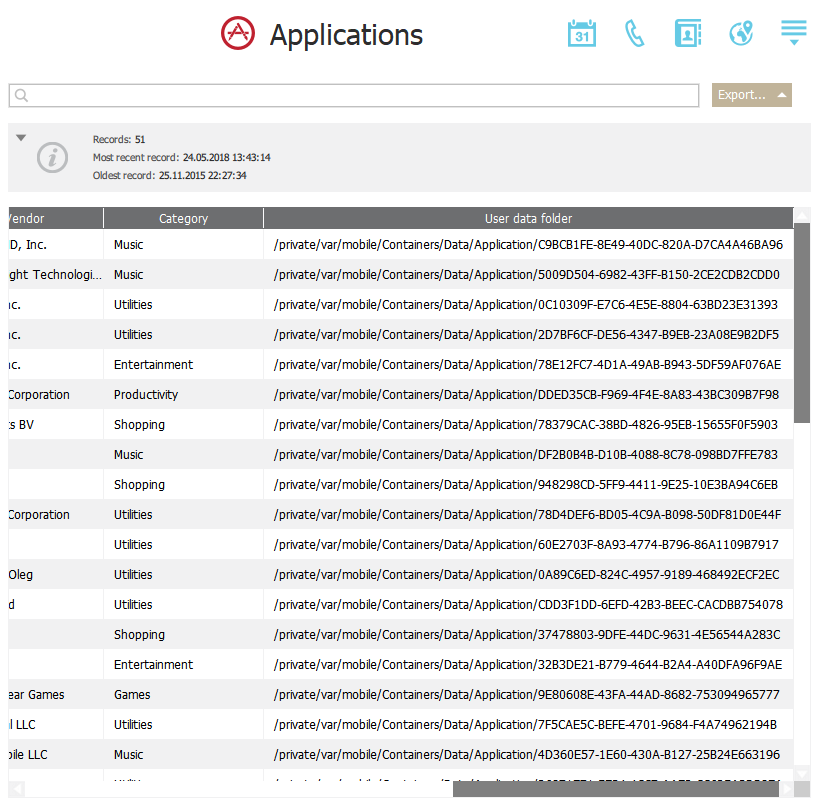
Locations? We have them for you:
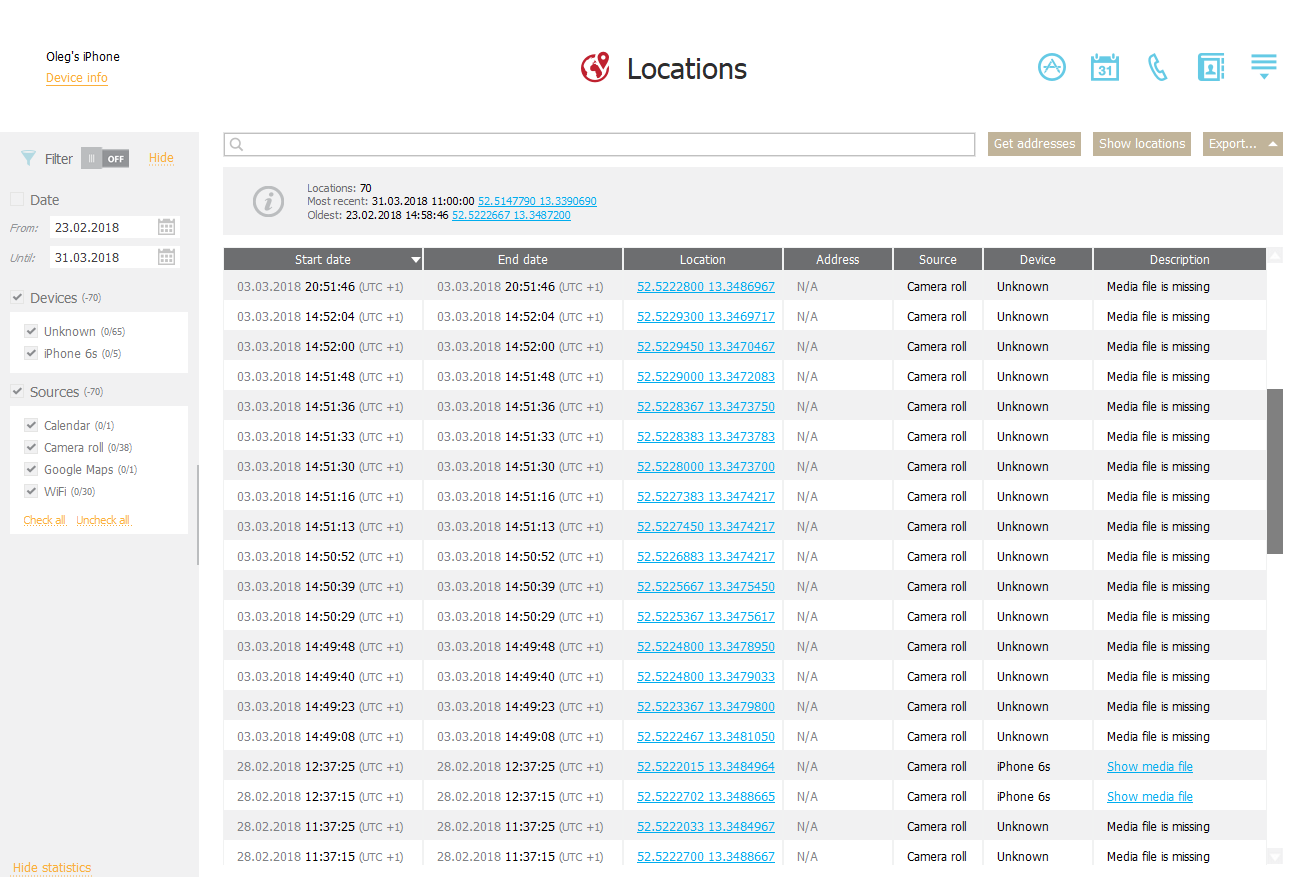
As you can see, we aggregate location data from multiple sources including the logs, geotags in media files and even calendar events:
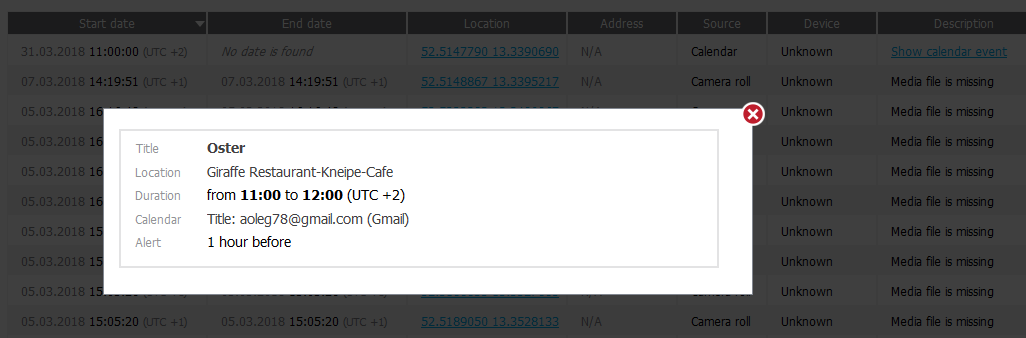
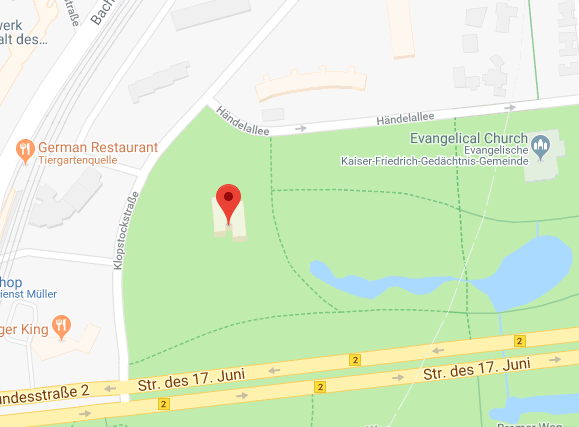
If you click on the coordinates, the map will open:
In addition, you can analyze the user’s Safari bookmarks and browsing history, notifications, call logs and messages, and a lot more as shown on the following screen shot: