With more than 127 million users in multiple countries, Apple Pay is one of the more popular contactless payment systems. Unlike some competing payment technologies, Apple Pay is not only tightly integrated into Apple’s ecosystem but is exclusive to Apple devices.
Apple Pay serves as a digital wallet, digitizing user’s payment cards and completely replacing traditional swipe-and-sign and chip-and-PIN transactions at compatible terminals. However, unlike traditional wallets, Apple Pay also keeps detailed information about the user’s point of sale transactions. Due to the sheer amount of highly sensitive information processed by the system, Apple Pay is among the most securely protected vaults in compatible devices. In this article we’ll show you where and how this information is stored in the file system, how to extract it from the iPhone and how to analyse the data.
Apple Pay and Privacy Considerations
What do we expect of a modern payment system? If, for example, we look at PayPal transactions, we can access pretty much everything about the purchase. PayPal keeps information about the date and time of transaction, amount and currency, as well as both parties (“buyer” and “seller”). However, in addition to all that, PayPal may receive (and store) information about what exactly the money was paid for.
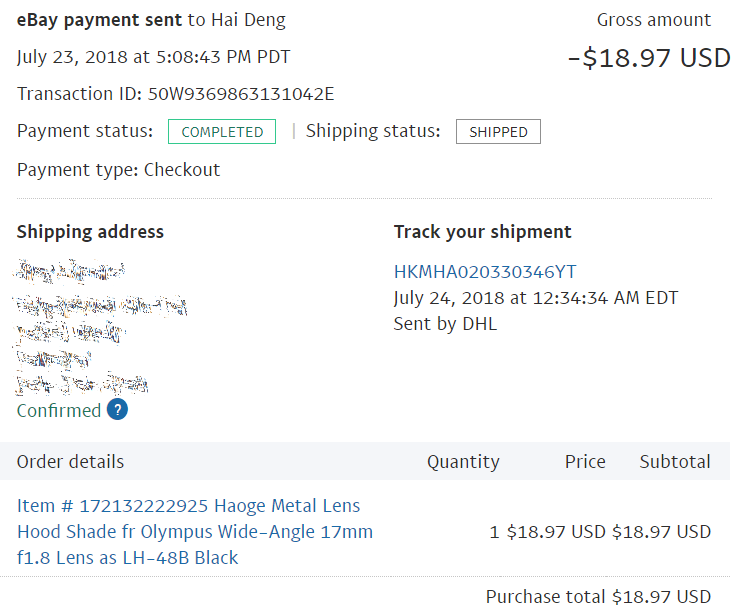
Apple Pay uses a very different model, at least when it comes to physical transactions. During the launch of Apple Pay, Senior VP Eddy Cue said: “We are not in the business of collecting your data. So, when you go to a physical location and use Apple Pay, Apple doesn’t know what you bought, where you bought it, or how much you paid for it.”
As a result, merchants accepting Apple Pay as a payment method do not transmit information about what exactly the user purchased (and paid for). On the one hand, this creates a serious limitation; even obtaining a simple receipt is not possible with Apple Pay data alone (this would be similar to a credit card statement). On the other hand, Apple does not receive, process or store any more information than is absolutely required to authorize and authenticate transactions. The limitation becomes a feature lauded by privacy protection advocates.
“Tap-to-pay is easy enough, but today’s users expect evolving, personalized experiences that sync as they shop. They willingly share personal information to foster enhanced experiences with services like Netflix, Amazon, and others. Retailers, meanwhile, are jumping through hoops to discover everything they can about their consumers so they can deepen those relationships”, say Marc Freed-Finnegan & Jonathan Wall in “Apple Pay ‘no-data-collection’ isn’t a feature. It’s a problem”.
Whether this is a feature or a severe limitation is debatable. The matter of fact is: Apple does not collect or store more information than your typical credit card issuer. Knowing this allows experts to set their expectations accordingly when doing forensic analysis of Apple Pay data.
Apple Pay Data
Apple Pay transactions are not synchronized across devices. Instead, they are stored locally on the device itself. A transaction you make with your Apple Watch will not appear on your iPhone, and vice versa. There are no user-accessible Apple Pay statements to download, even if Apple itself retains transactions on the server.
Apple treats transaction data as highly confidential information. It is not synchronized with iCloud, and it is not saved in iCloud backups. The data is not part of iTunes backups either. In other words, extracting information about Apple Pay transactions is only possible from a physical device (iPhone, iPad, or Apple Watch).
If you are interested in Apple Pay security, check out the following articles:
Extracting Apple Pay Data
Apple Pay data is stored in the following folder:
private/var/mobile/Library/Passes
In particular, look for the following two files:
private/var/mobile/Library/Passes/<cardid>/pass.json (payment cards)
and
private/var/mobile/Library/Passes/passes23.sqlite (transactions)
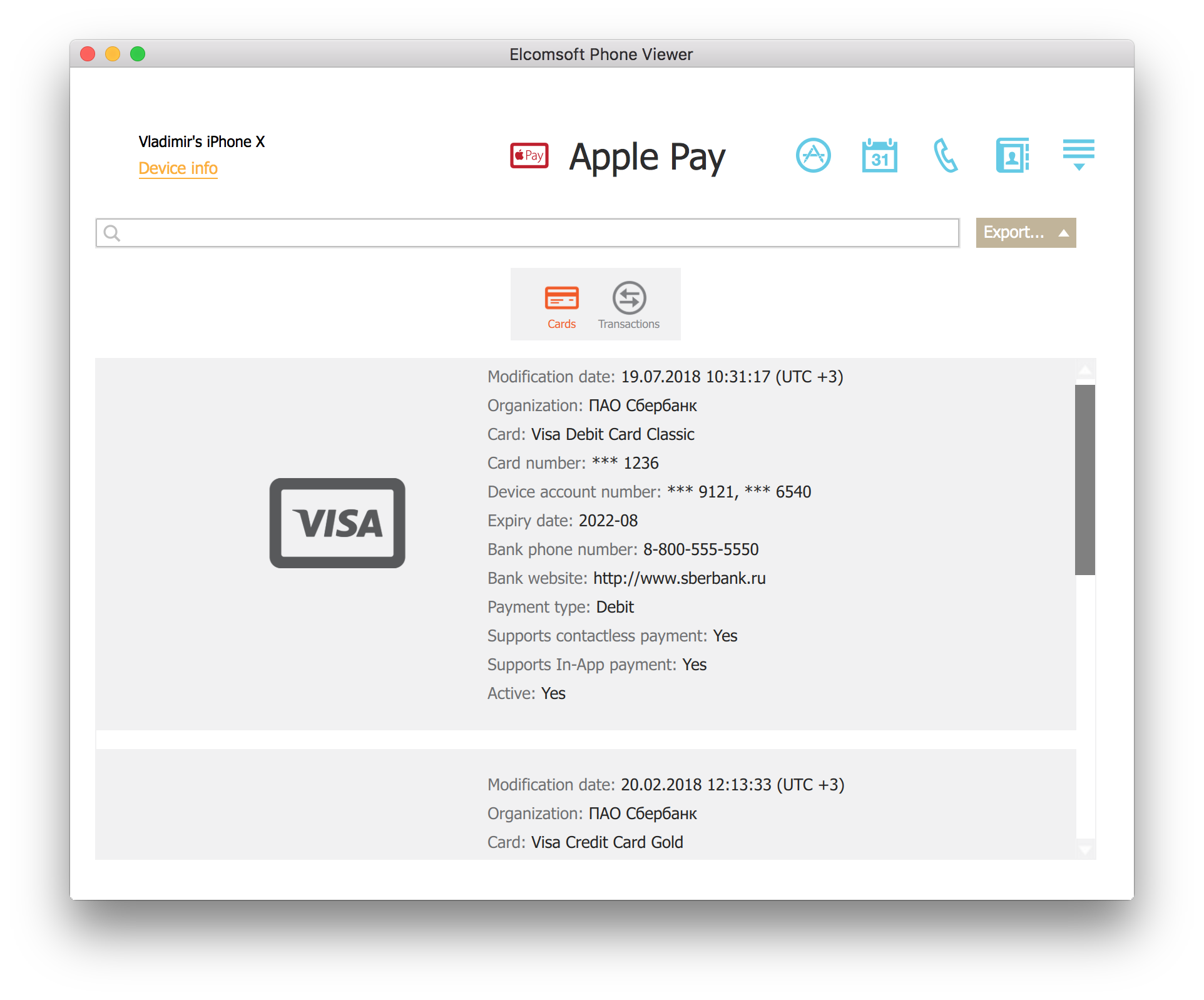
The first file contains information about the payment method (activation data, picture of the card, and 4 last digits of the card number). The following card information is available:
- Organization (passes23.sqlite) – name of the bank or card issuing institutuon
- Card (pass.json) – card name
- Card Number (passes23.sqlite) – last 4 digits of the card number
- Device Account Number (passes23.sqlite) – last 4(5) digits of the device account number. Each card may have several different DAN numbers
- Expire Date (pass.json) – card expiry date
- Modification Date (passes23.sqlite) – date the card was last modified
- Bank Phone Number (pass.json) – issuer’s telephone number
- Bank Website – issuer’s Web site
- Payment Type (passes23.sqlite) – payment card type
- Supports Contactless Payment (pass.json) – whether or not contactless payments are supported
- Active (passes23.sqlite) – whether or not the card is actively linked to the device (at the time of device imaging)
The SQLite database passes23.sqlite (transaction information) includes:
- Date – transaction date and time
- Card Number – last 4 digits of payment card number
- Merchant – the name of the merchant
- Category – type of service
- Location – location data including altitude
- Address – typically, just the city
- Amount – amount and currency
- Status – payment status (accepted, rejected, failed etc.)
- Merchant Phone Number
- Merchant URL – for online payments this field contains the address of the WEB site
- Merchant Location – geolocation data of the merchant
- Merchant Postal Address
- Device Account Number – last 4(5) digits of the device account number at the time of transaction
In addition, the passes23.sqlite also stores other information such as boarding basses, tickets, reservations, discount and loyalty cards etc.
Technically, one can try viewing Apple Pay cards and transactions on the iPhone itself. Interestingly, iOS uses the Wallet app to display Apple Pay transactions on the iPhone. Wallet also stores other data such as boarding passes, reservations, loyalty cards etc. That other data is synchronized with iCloud and is saved in local backups; Apple Pay transactions don’t.
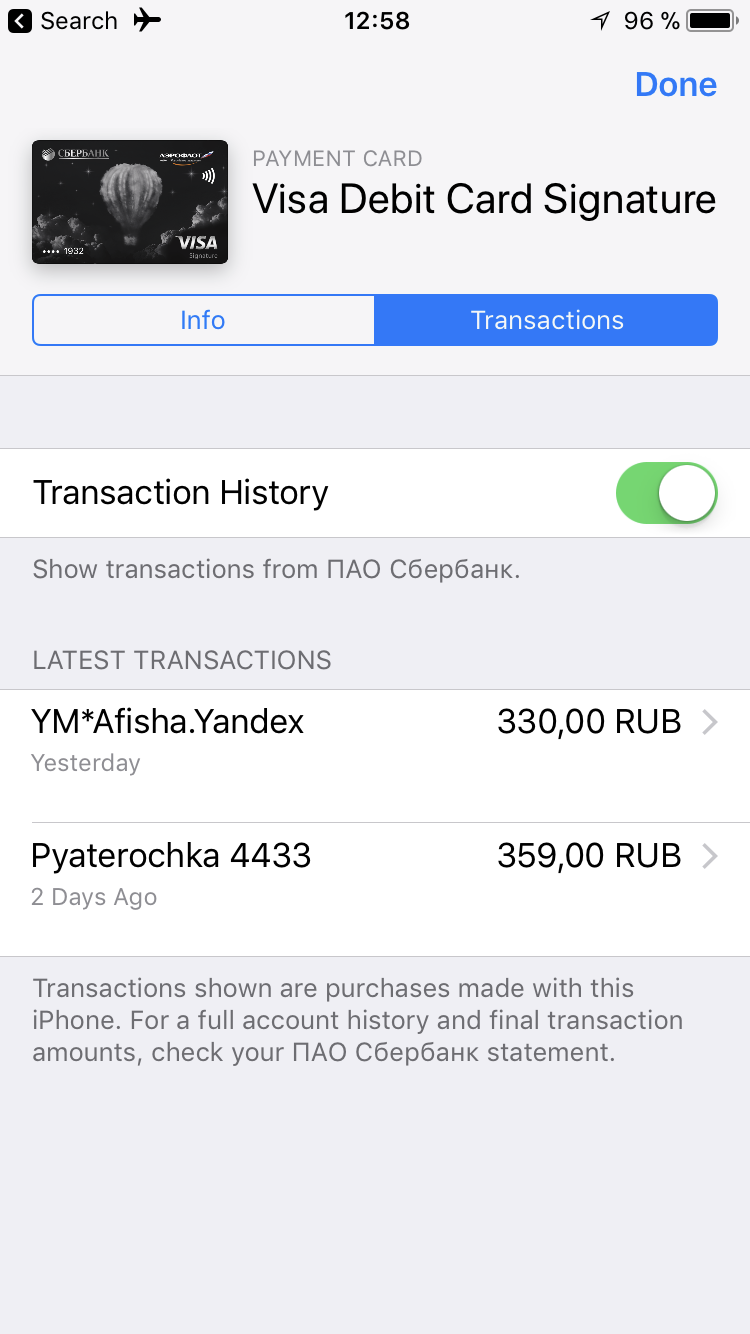
However, Apple limits you to viewing only the last 10 transactions. In fact, the device can store a significantly larger number of transactions; however, they are not accessible through the iOS user interface.
Apple Pay data is neither saved into a local backup nor uploaded to iCloud. As a result, the data is not available via logical acquisition or cloud extraction. You will need to obtain a file system image of the device in order to gain access to Apple Pay digital wallet.
What about Apple Pay transactions made with Apple Watch? These transaction remain the property of the watch; they are not transferred to or synchronized with the iPhone or iCloud. While you can make a backup of your Apple Watch (it will be part of the paired iPhone backup), Apple Pay transactions won’t be there either. The only thing you can do to extract transactions from the Apple Watch is attempting a WatchOS jailbreak.
Below are step by step instructions on extracting a file system image.
Important: DO NOT REMOVE THE PASSCODE when installing a jailbreak or imaging the device, even if you are instructed to do so by jailbreak developers! Removing the passcode wipes Apple Pay data immediately. What happens if you remove the passcode? In this scenario, all payment cards will be unlinked (but will be retained in the file system as inactive). However, the entire transaction history will be wiped. Notably, the same thing happens if the device logs out of iCloud.
If the device does not have a passcode, it does not have Apple Pay data. You may still obtain a file system image, but Apple Pay information will not be there.
- In order to image an iPhone, you will need superuser privileges. Superuser access is only available via privilege escalation exploits. Some of these exploits are incorporated in publicly available jailbreaks. By the time of this writing, public jailbreaks are available for iOS 10…11.3.1. If you know the passcode, then you can attempt jailbreaking the device to perform physical acquisition.
- Make a local backup of the iPhone with iOS Forensic Toolkit or iTunes (make sure to set a temporary password; you’ll be able to decrypt the backup with Elcomsoft Phone Breaker). Then obtain and install a compatible jailbreak on the iPhone.
- Disable Wi-Fi on the iPhone being imaged, or, better yet, switch it to Airplane Mode. Make sure there are no other iOS devices connected to the same network as your computer.
- Launch iOS Forensic Toolkit.
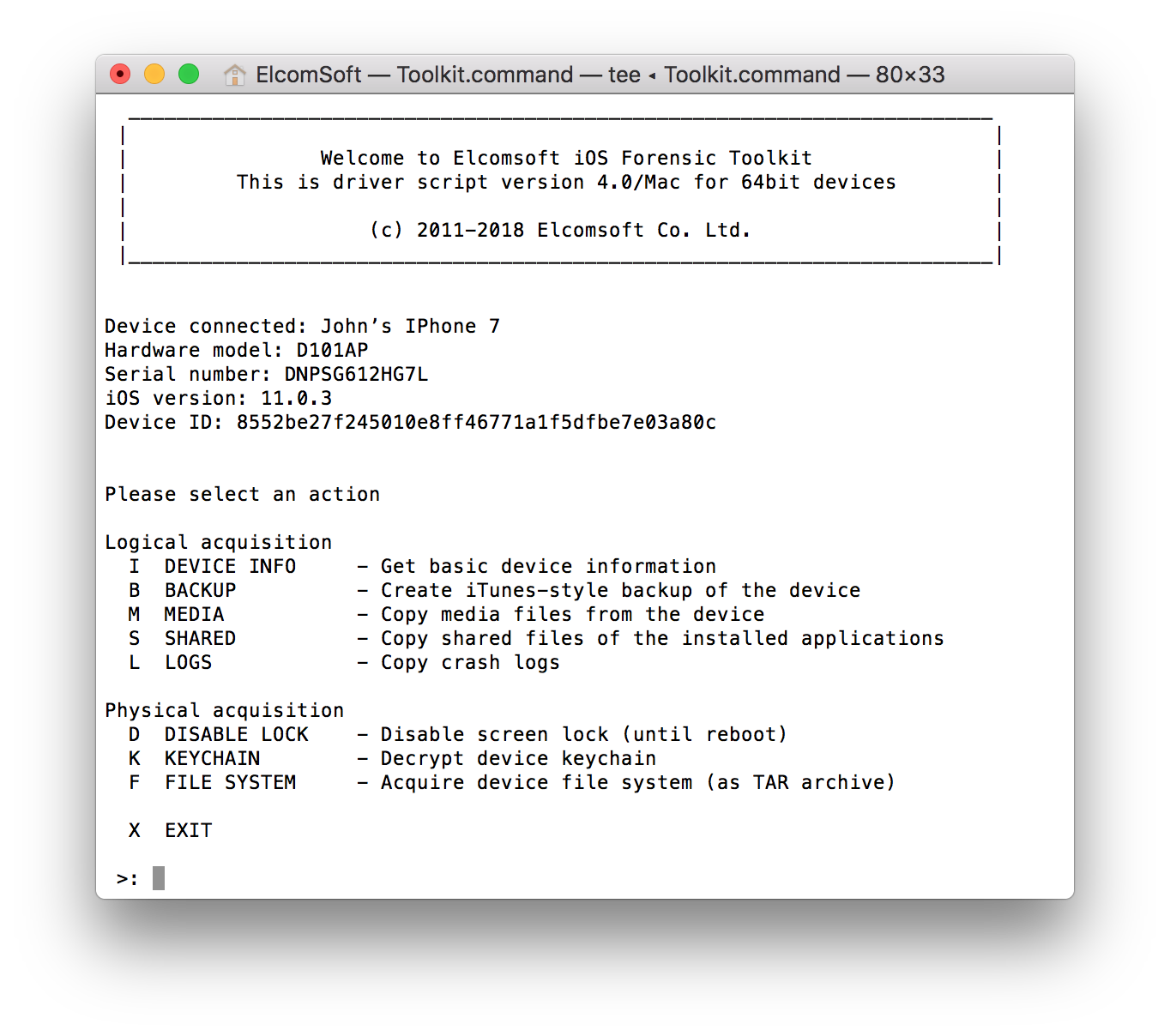
- From the main menu, select “D” – Disable lock. This will prevent the device from locking the screen after a timeout until you reboot the iPhone. Disabling screen lock is important to access and extract Apple Pay data.

- Use the “F” command to extract a file system image. The file system image will be saved on your computer as a TAR file.
- The extraction may take a while (up to 2 hours for 100 GB of data).
Once the extraction is complete, proceed to analysing the TAR file.
Analysing Apple Pay Data
Elcomsoft Phone Viewer 4.0 or newer can be used to analyse Apple Pay data.
- Launch Elcomsoft Phone Viewer 4.0 or newer.
- Open the file system image produced during the extraction.
- Click “Apple Pay”
You’ll be able to access information about payment cards:
List of transactions:
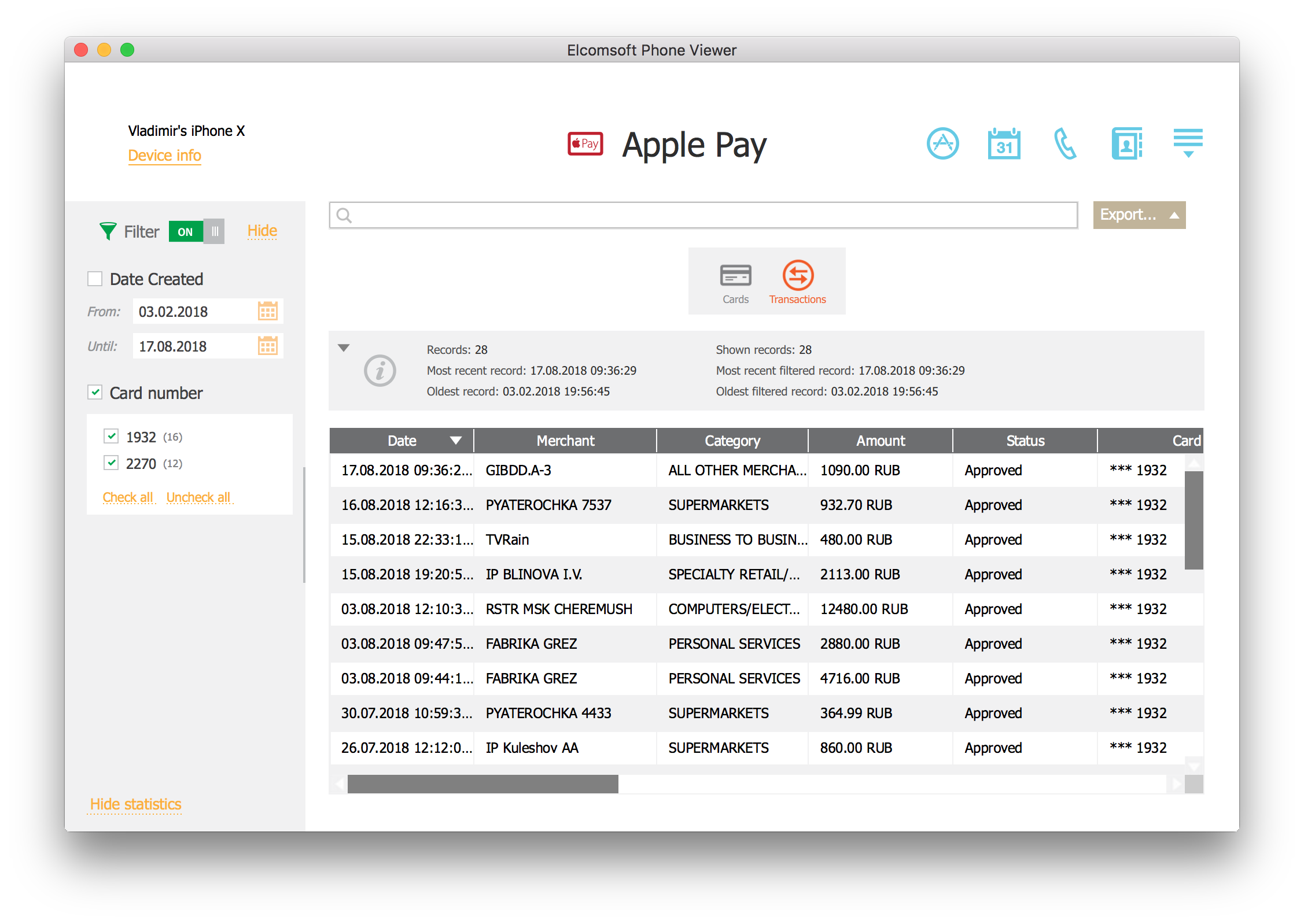
As you can see, Apple Pay transactions contain information that is similar to a bank statement.
Conclusion
iOS contains a large amount of artefacts that can be essential for an investigation. In such a complex system as iOS, we never stop discovering new artifacts. Apple Pay data is a great source of evidence that can affect investigations by presenting, for example, an additional source of location data, thus allowing to establish device presence in a given time at a determined location.








