The cloud becomes an ever more important (sometimes exclusive) source of the evidence whether you perform desktop or cloud forensics. Even if you are not in forensics, cloud access may help you access deleted or otherwise inaccessible data.
Similar to smartphones or password-protected desktops, cloud access is a privilege that is supposed to be only available to the rightful account owner. You would need a login and password and possibly the second factor. These aren’t always available to forensic experts. In fact, it won’t be easy to access everything stored in the cloud if you have all the right credentials.
Apple iCloud is one of the most advanced cloud solutions on the market, with lots of services available. These include comprehensive device backups, synchronization services across the entire Apple ecosystem including the Apple TV and Apple Watch devices, file storage, password management, home IoT devices, Health data and more. And it is pretty secure.
Let’s review all the possibilities of accessing Apple iCloud data with or without a password.
Before we begin
Apple can provide iCloud data to the government through the course of legal requests. As Apple keeps all the data, they have access to some parts of the data. While all the data is encrypted, Apple holds the encryption keys for most of the cloud data as well. Only the most critical information (such as the user’s passwords, Health or Messages) is encrypted in P2P mode and so not accessible to Apple. (Yes, we know that P2P is not a perfect description of what’s going on with that data on Apple servers). All that Apple needs to access the data is the user’s Apple ID, or the device serial number, or the phone number. All that properly documented. The problems are:
- It is not easy to comply (even if you work for LEA)
- Processing government information requests is very slow due to the large volumes
- Still not all data is returned (p2p-encrypted records are not included)
- The data that is returned is very hard to parse and analyse (requires special software and proper skills)
So we will review the other ways to access iCloud.
The easy way: no 2FA
I’d say that two-factor authentication is a must nowadays. Many (simple or common) passwords can be easily guessed; some can be broken using “reverse brute-force attacks”; phishing attacks become smarter and smarter; keyboard sniffers (software and hardware) can steal everything your type; password reuse is a common reason why even complex passwords can be often recovered.
If there is no 2FA, there are several places to look at in order to obtain the password:
- (Windows) Passwords can be saved in the browser, whether it is Google Chrome, Mozilla Firefox, Microsoft IE or Edge, or less popular Opera. Simply use Elcomsoft Internet Password Breaker to discover all saved passwords, and look at those used for apple.com or icloud.com
- (macOS) The system keychain. You can find it with built-in Keychain utility, or analyze with Elcomsoft Password Digger
- In the device keychain. Use Elcomsoft Phone Breaker to access the keychain (using encrypted iTunes backup as a data source; the backup password should be known or recovered). You can use iOS Forensic Toolkit if you have the device itself and it has an iOS version that can be jailbroken. Use it if the backup has a password set but it is not known and cannot be reset
The hard way: 2FA
Apple started using the second factor as an additional security measure a long time ago. The initial implementation (the Two-Step Verification, or 2SV) was lacking in many respects. Initially, 2SV did not protect iCloud backups. It was Celebgate that forced Apple to introduce 2SV protection for backups. Finally, Apple implemented the fully-functional and secure Two-Factor Authentication (2FA), and forced 2SV to 2FA migration.
Apple provides no statistics on the number of accounts that use 2FA, but does its best to promote this security measure. If you set up a new Apple ID today and click through the configuration wizard, 2FA will be enabled automatically. You cannot easily turn it off. Finally, some iCloud-related features now require 2FA.
According to our own statistics (which is probably not perfect), just about 30% of iCloud users have 2FA. Some sources says that 2FA usage reaches up to 60%, though I personally think that this number is overestimated.
More information on 2FA is available here. The second factor can be difficult to get: you need either the trusted device itself, or the ability to receive an SMS with a code, so in fact you’ll need a SIM card (or its clone).
If (and only if) 2FA is enabled and the phone is protected with a passcode (and you know the passcode), the phone becomes the key to everything. Using just the phone (and the passcode), you can change iCloud password (without the need for the original one) and even add or replace trusted phone numbers. More on that here.
Finally, you can access iCloud without the password. We have discovered this method (and implemented it in our software) as long as five years ago, see: Breaking Into iCloud: No Password Required
What are authentication tokens and how to obtain them
An authentication token is similar to a cookie saved by your Web browser when you log in to a Web site. The token serves as a “replacement” of your standard credentials (the login, password and second factor). Technically, a token is a small portion of binary data generated by the server after successful authentication (including the second step). It can be used to authenticate with that server instead of a password. There is no way to get login or password back from the token; also, tokens may expire after some time that can range from several seconds to several months.
Let’s start with the device itself. Here the token is saved in the iOS keychain, and can be easily located at com.apple.account.AppleAccount.token record.
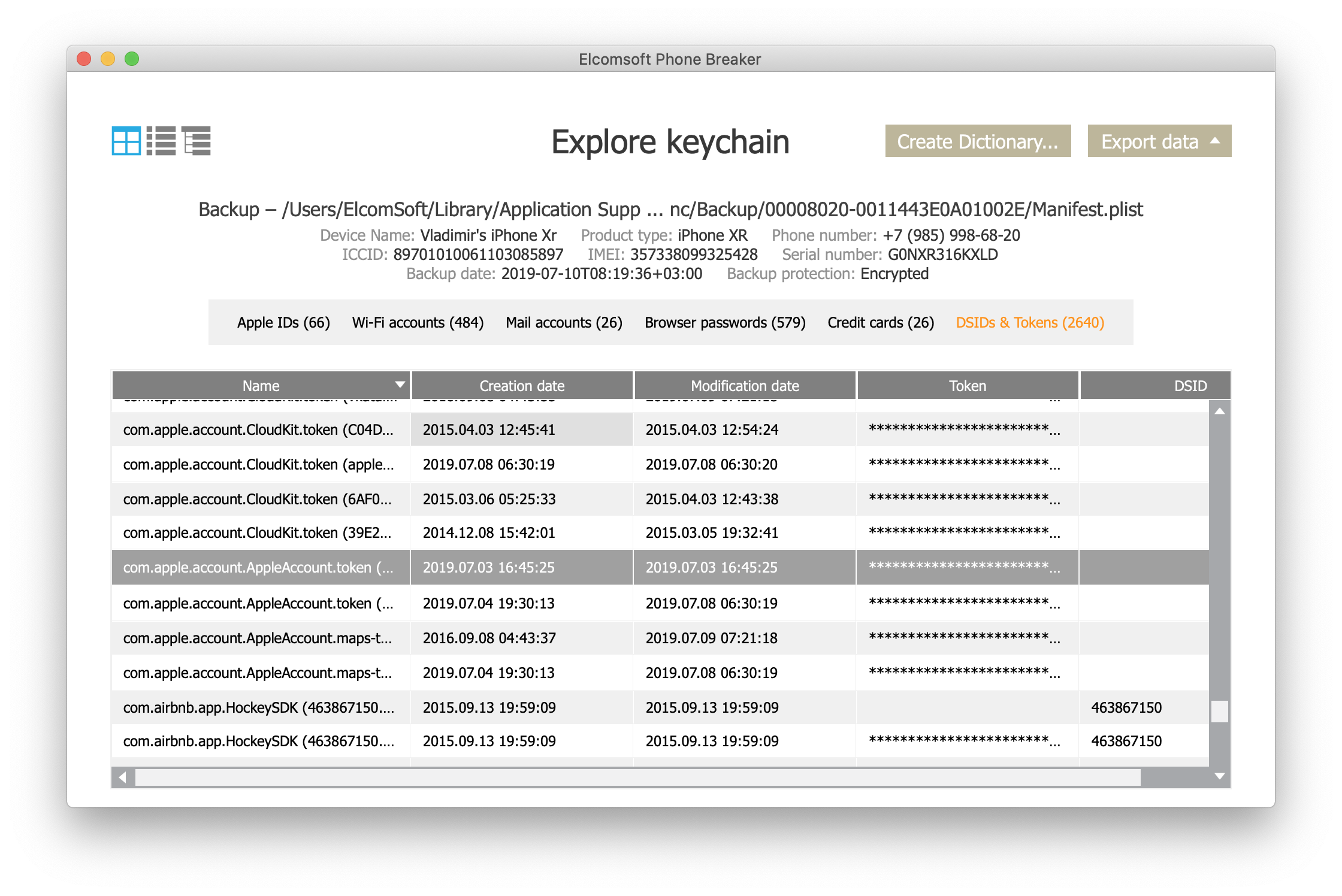
And here is the first issue. For 2FA accounts, Apple pins tokens to that specific device. If you extract the token and try to use it on a different device (another iPhone, Windows or Mac computer), you’ll be prompted for a password. Still, for accounts without 2FA, the token can be used as a limited replacement of the login and password. Some data can be only downloaded from iCloud with a real login and password (more on that later).
On Windows, the token is hidden deep inside the system, and is encrypted. We developed a tool to extract and decrypt it. The tool is quite simple to use: just run it, and the token is saved into a text (XML) file, ready to use with Elcomsoft Phone Breaker.
Unfortunately, Windows currently saves limited tokens (pinned to a particular device), just like iOS. Still, you can run Elcomsoft Phone Breaker on that computer to use the token.
With macOS, the situation is different. Apple implemented a stronger protection (with token “pinning” for 2FA accounts) just about a year ago, but we have recently found a way to extract and decrypt unrestricted tokens, too. Just in case, we extract both tokens, the limited one and the unrestricted one.
Obtaining the tokens is as simple as running a command-line utility, like with the Windows version. We save both tokens into the same XML file. Remember that limited tokens can be used at this computer only, while the unrestricted one can be transferred to another computer, Windows or Mac.
You might be able to get the token from the macOS keychain, at the same record as on iOS: com.apple.account.AppleAccount.token. Use the Keychain utility for that, no additional software required.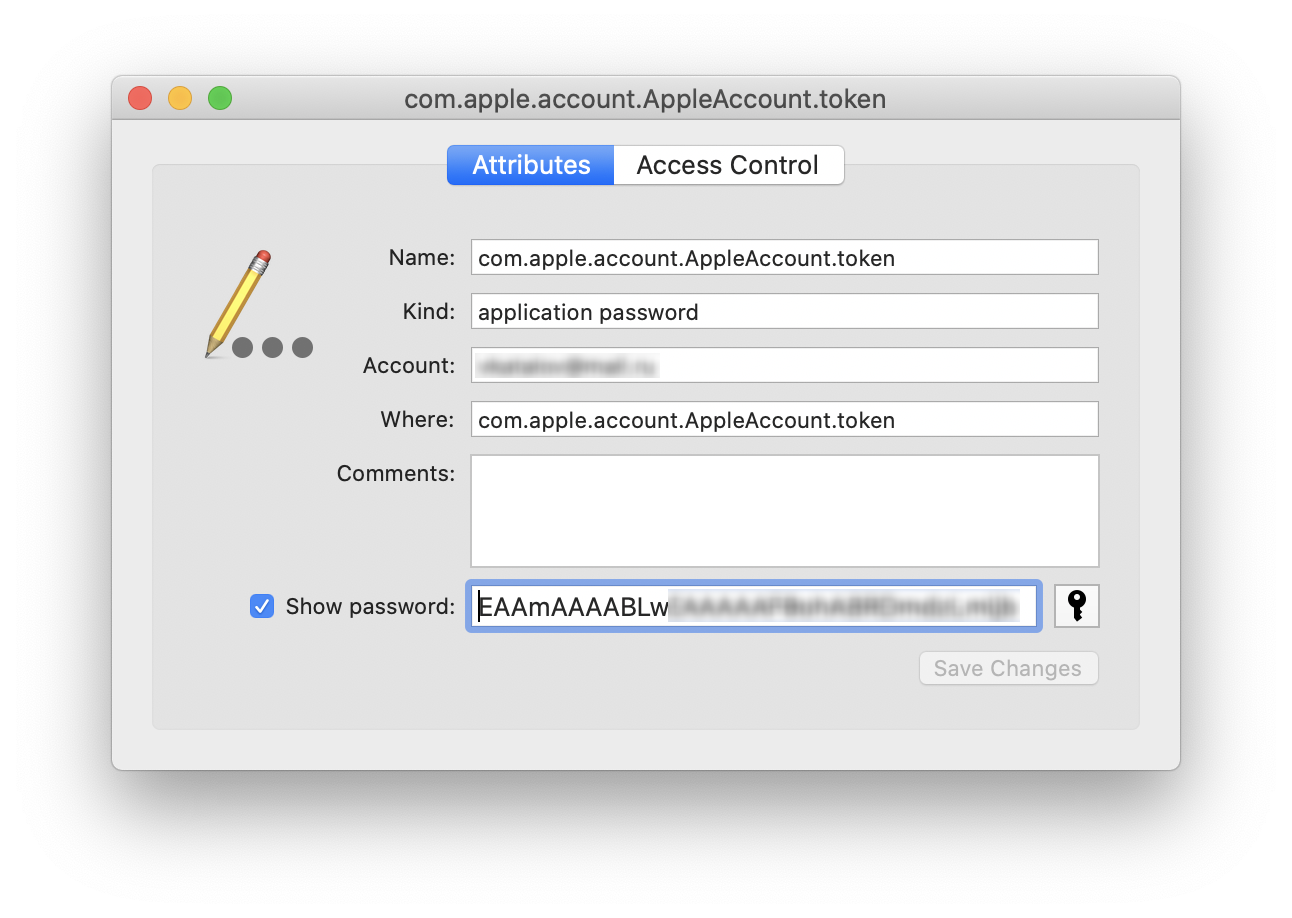 You can also extract the token not only from the live system, but from the disk image (after mounting it, of course), for any user in the system (password will be required, of course); see Elcomsoft Phone Breaker manual for details.
You can also extract the token not only from the live system, but from the disk image (after mounting it, of course), for any user in the system (password will be required, of course); see Elcomsoft Phone Breaker manual for details.
Finally, use the token in Elcomsoft Phone Breaker. On the authentication page, switch tabs from ‘Password’ to ‘Token’ and enter the token (long string) into the text box.
What are the limitations of authentication tokens?
Can you get the same set of data with the token compared to what you download with a password? For accounts without 2FA, pretty much. For 2FA accounts, you bump into restrictions.
For a long time, Apple does not allow to download iCloud backups using tokens. Even if 2FA is not enabled, a token works for a very limited time; currently it’s just one hour. Some time ago, the tokens worked perfectly for all data in the cloud including device backups, and without any time limits. Today, you can only use tokens to access backups in Apple accounts without 2FA, and only during one hour after the token was created (the user signed in with their login and password).
Regardless of whether or not the account is protected with 2FA, tokens can still be used to access the following data:
- iCloud Photos
- All files from iCloud Drive, including many third-party app containers (1Password, WhatsApp, Viber etc.)
- Recovery token for FileVailt2-encrypted drives
- Many categories of synced data including contacts, calendars, notes, Wallet cards and more
- Safari browsing history
- Call logs
- Cloud mail
There are some categories that are not accessible. These include iCloud Keychain, Messages, Health data, HomeKit-related data, ScreenTime statistics and possibly more. All that data, as mentioned above, is additionally encrypted and accessible only to trusted devices… and Elcomsoft Phone Breaker! You’ll have to supply the login and password, pass 2FA, and provide the screen lock passcode (or password) of one of the trusted devices. You’ll just need the password, the device itself is not required.
What about Find My?
Find My Phone (or just Find My in iOS 13) is a theft protection feature Apple provides to its users. It features remote lock and remote wipe as well as the ability to track the device location (if it is connected to a wireless or remote network; this particular feature will be further improved in iOS using beacons technology, so tracking will be possible even if device is switched off).
Find My not only allows you to find the lost device or lock or delete its data, but features reliable Factory Reset Protection (also known as iCloud Lock) that prevents subsequent device activation with a different Apple ID (if the device was reset or re-flashed via DFU or recovery mode).
Turning off the Find My feature requires users to enter their Apple ID password. The second factor is not required, you just need the password (same goes for Find My on icloud.com: this feature requires password only, but not the second factor, which is the common case when you’ve lost your only device and cannot receive push notifications and text messages).
So is it possible to unlock the device from the cloud using token(s)? No. You need the actual password.
There are other ways for disabling iCloud lock, too. All of them are listed on Apple web site. You can either work with Apple to regain control over your Apple account or visit an Apple Store and provide a proof of purchase for the device.
A few shady businesses advertise iCloud unlock. The majority of those are cheaters, while the remaining few forge proof of purchase receipts or do it through a crooked Apple employee.
How to protect your iCloud account
It is not as easy as it sounds, but we’ll do our best to give you the most important recommendations.
The following suggestions will help you secure your iCloud account:
- Use a strong password (Apple’s requirements are good enough, but if you created the account a long ago, you may need to update your password).
- Make sure this password is VERY unique (does not even resemble any other password you use).
- Make sure the password you choose does not top the charts of leaked passwords (otherwise you may fall victim of a reverse brute force attack).
- Use two-factor authentication (speaking of Apple, you have almost no choice. Your trusted device(s) will receive push notifications, and you’ll need at least one phone number to receive text messages; both methods are always enabled, and there are no alternatives).
- Make sure to keep your trusted phone number(s) up to date in your Apple Account. Those can be used to receive a 2FA code.
- Keep your Apple Account password in a safe place, whether it is a piece of paper in your locker or the record in a password manager database (which, in turn, should have a different strong password and 2FA).
- Protect access to all your devices that have (or ever had) access to your Apple Account, including smartphones, desktops, laptops, and IoT devices.
- Never sign in to your iCloud account from public devices, even if you have two-factor authentication enabled.
One question probably remains: whether or not you should change your password periodically. It may look like a good idea, but in fact it is not. Considering that passwords should be complex and very unique, you will have a hard time creating and memorizing them. You only have to change the password if you think it might be compromised.




