By this time, seemingly everyone has published an article or two about Apple re-introducing the vulnerability that was patched in the previous version of iOS. The vulnerability was made into a known exploit, which in turn was used to jailbreak iOS 12.2 (and most previous versions). We’ll look at it from the point of view of a forensic expert.
Timeline
Here’s a quick timeline:
- iOS 12.2: a vulnerability was discovered allowing hackers to develop a working jailbreak. The vulnerability is also present in previous versions of iOS, making the unc0ver jailbreak backward compatible with all versions of iOS 12.0 through 12.2, as well as with all versions of iOS 11.
- iOS 12.3: Apple patches the vulnerability.
- iOS 12.4: Apple unpatches the vulnerability. Hackers quickly release a working unc0ver jailbreak. This makes it the first time for the last 6 years for a jailbreak to exist for the latest official iOS release *and* hardware (the A12 generation).
- iOS 12.4.1 (today): Apple patches the vulnerability again. iOS 12.4 is still being signed and can be installed by iOS 12.3 users through iTunes on all supported devices. At this time, users can still downgrade from 12.4.1 to 12.4 without losing data.
Why This Matters
At this time, forensic experts who wish to jailbreak iOS 12.3 devices in order to perform physical extraction still have a short window of opportunity to update to the vulnerable but still being signed iOS 12.4. They can then install a jailbreak and perform data extraction.
At this time, devices already updated to the patched iOS 12.4.1 can still be downgraded to iOS 12.4 without losing data.
The Recommended Jailbreak
There are two public jailbreaks exploiting the vulnerability in iOS 12.4, unc0ver and Chimera (we highly recommend using these official links; there are more fake jailbreak sites distributing malware than one can possibly imagine). For now, the unc0ver jailbreak is the only one that works with A12/A12X devices; we can specifically recommend unc0ver 3.5.5 (as opposed to the latest version); for older devices, you can use any of them.
The differences between unc0ver 3.5.5 and later versions of this jailbreak lie in file system remount. unc0ver 3.5.5 does not remount the file system and does not modify the system partition, exhibiting similar behavior to the RootlessJB. However, unlike RootlessJB, unc0ver 3.5.5 did reboot our test devices, which means you’ll have to know the device passcode in order to unlock it again after a reboot.
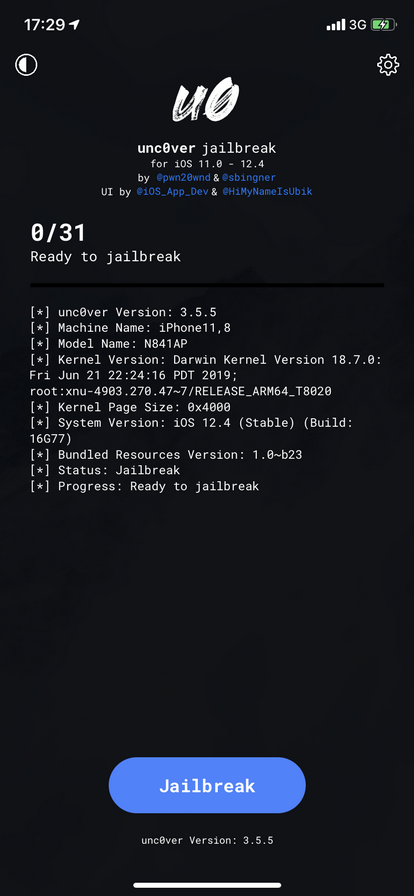
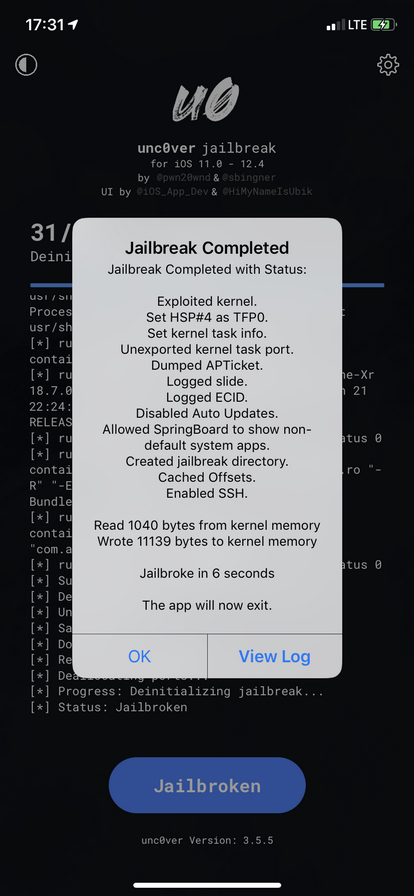
When installing unc0ver 3.5.5, make sure to tap on the gearbox icon in the bop right corner and check OpenSSH.
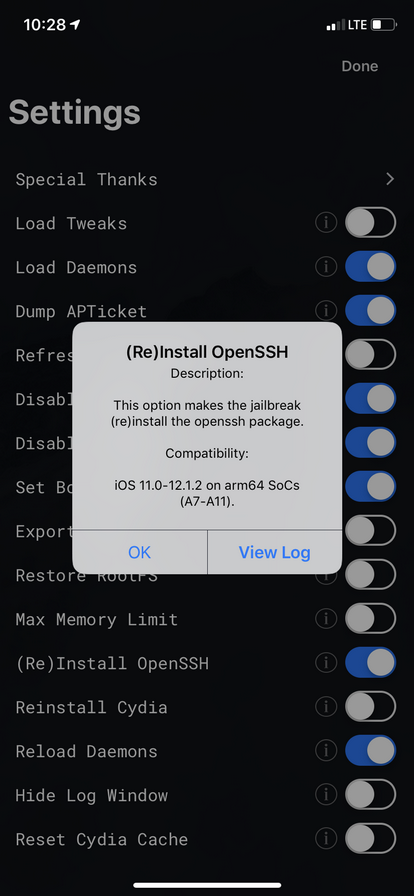
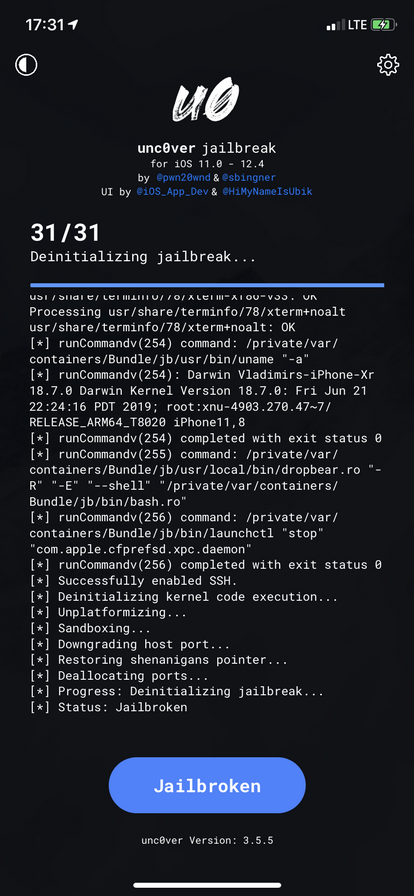
Our Recommendation
If you have any devices on your processing queue that are still running iOS 12.3 (including iOS 12.3.1 and 12.3.2) and you’re considering jailbreaking them for the purpose of physical acquisition, we recommend updating them to iOS 12.4 right away while Apple is still signing this vulnerable version. At this point, it is highly unlikely that the development community will spend the time and effort jailbreaking iOS 12.3. Unless a new exploit is discovered for one of the later versions, iOS 12.3 is likely to remain without a working jailbreak for the time being. Once you’ve updated the device, just wait for a few more days while we’re preparing the update of iOS Forensic Toolkit, our iOS physical acquisition tool, to fully support the latest unc0ver and Chimera jailbreaks (for now, just update to 12.4, and that’s it). tvOS 12.4 can be jailbroken as well, btw: see Apple TV and Apple Watch Forensics for details.
Why Jailbreak?
We have two articles explaining why and how to jailbreak iOS devices, and what are the implications: Step by Step Guide to iOS Jailbreaking and Physical Acquisition and Forensic Implications of iOS Jailbreaking.







