Are you excited about the new checkm8 exploit? If you haven’t heard of this major development in the world of iOS jailbreaks, I would recommend to read the Technical analysis of the checkm8 exploit aricle, as well as Developer of Checkm8 explains why iDevice jailbreak exploit is a game changer. The good news is that a jailbreak based on this exploit is already available, look at the checkra1n web site.
The jailbreak based on checkm8 supports iPhone devices based on Apple’s 64-bit platform ranging from the iPhone 5s all the way up to the iPhone 8 and iPhone X. Unlike previous jailbreaks, this one supports most iOS versions, up to and including iOS 13.2.2 at the time of this writing. Support for future versions of iOS is also possible due to the nature of this exploit. Most iPads are also supported. Currently, there is no support for the Apple Watch, though theoretically it is possible for Series 1, 2 and 3. The Apple TV series 4 and 4K are supported by the exploit, and a jailbreak for series 4 is already available.
What does that mean for the forensic crowd? Most importantly, the jailbreak can be installed even on locked devices, as it works through DFU mode. That does not mean that you will be able to break the passcode. While you can extract some data from a locked device / unknown passcode, it won’t be much. From the other side, the jailbreak allows to dump the complete image of the file system if the passcode is known. This works for all devices from the iPhone 5s to X, many iPads, and Apple TV 4.
In this article, we will briefly describe how to install the jailbreak on Apple TV and what you can expect out of it.
Installation
First, connect the Apple TV to the power source and establish connection with the computer (using a USB Type-C cable). Then put the Apple TV into DFU mode. It is simple: press and hold both Menu and Play/Pause buttons on the Apple TV remote for about 7 seconds, until the light on Apple TV starts blinking rapidly.
Then, start checkra1n jailbreak on the computer (note that it is available for macOS only for now):
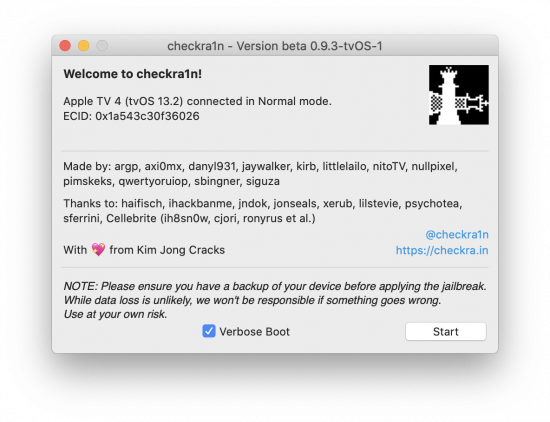
Press Start and follow the instructions; the jailbreak installation starts:
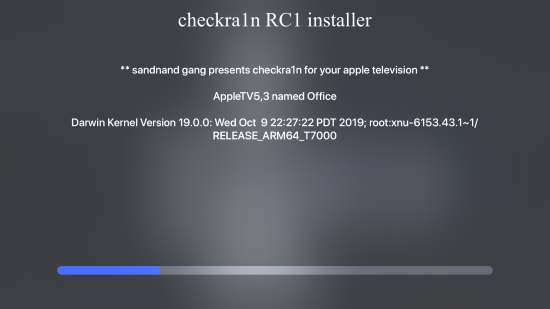
The whole process takes just a few minutes:
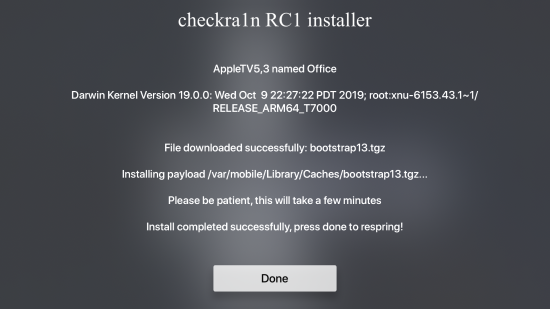
Once the jailbreak is installed, the main screen of the Apple TV magically changes. And yes, SSH is there:
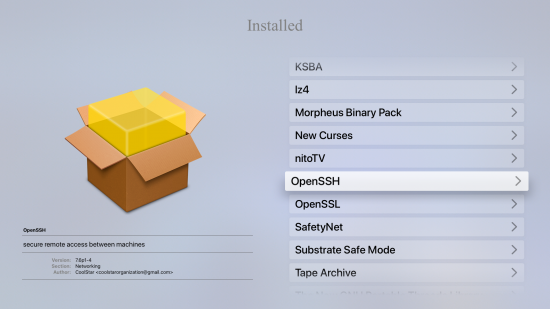
That’s it, you can start extracting the data.
Data extraction
Launch Elcomsoft iOS Forensic Toolkit:
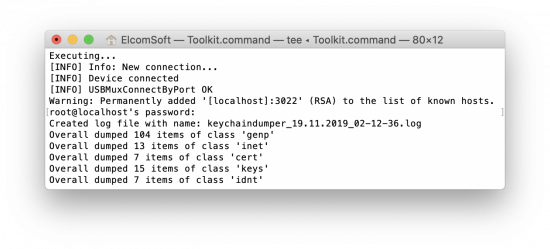
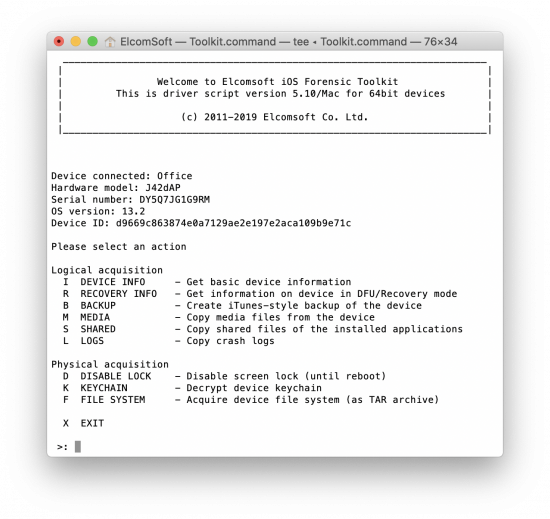 You can perform the full logical acquisition (extract media files and log files in particular), but that could be done even without jailbreaking, so we’ll skip to the physical acquisition phase. Use the option F to perform the full file system acquisition (to obtain a.tar file that can be further analysed with Elcomsoft Phone Viewer). After that (or prior to file system extraction) use the K command to obtain and decrypt the keychain:
You can perform the full logical acquisition (extract media files and log files in particular), but that could be done even without jailbreaking, so we’ll skip to the physical acquisition phase. Use the option F to perform the full file system acquisition (to obtain a.tar file that can be further analysed with Elcomsoft Phone Viewer). After that (or prior to file system extraction) use the K command to obtain and decrypt the keychain:
More information
Unfortunately, Apple TV’s don’t store that much data. They don’t sync with the iCloud keychain, there are no contacts or messages, no browser history etc. Still, the data is worth looking at. For more information, read Apple TV Forensics 03: Analysis. If you find something interesting in the Apple TV file system that we have missed, please let us know!
Conclusion
Jailbreaking is a risky process, but it worth it: by installing a jailbreak, you can definitely extract more information that with classic logical acquisition method. Do not forget about cloud acquisition! It would be hard to imagine that an Apple TV was the only device connected to the user’s Apple iCloud account. For that purpose, Elcomsoft Phone Breaker is probably the best program of a kind, as it allows downloading iCloud backups and lots of synced data including the keychain, Health records, Messages (iMessage and SMS) and more.








