When attacking a password, the traditional forensic workflow requires uploading the entire encrypted file or document into a password recovery tool. This approach, while simple and intuitive, has one major drawback if you are using remote computers or cloud instances to perform an attack. If the remote computer is compromised, the entire file or document is leaked complete with its (still encrypted) contents. Learn how to overcome this issue and perform remote attacks without the reason of leaking personal information.
Encryption Metadata
The solution to the problem is obvious: use just the required minimum of information to run the attack. In the case of document passwords, this means you would only need a very small part of a file that contains the encryption metadata such as the hash and salt values. To use encryption metadata, you will need two tools working together: a tool to extract the encryption metadata from the files you are about to attack, and the tool that can use the extracted data to perform the attack.
We have booth tools readily available and shipped as parts of a single package. Elcomsoft Distributed Password Recovery 4.21 introduced the ability to run attacks on tiny files containing encryption metadata instead of the whole document. By using encryption metadata to set up attacks, you are automatically ensuring that absolutely no raw or encrypted data gets into the wrong hands as none is included in the extracted hash files.
The included Elcomsoft Hash Extractor allows you to extract password hashes from many file formats. The available formats include several password manager databases, Microsoft Office, Open Document, Apple iWork, Hancom and Adobe Acrobat documents.
Using hash metadata instead of the original raw document is especially important if you are using Amazon or Microsoft Azure cloud instances to speed up your attacks. If encryption metadata is everything that’s transferred to the remote server, the risk of leaking personal information in a case of a breach is reduced to absolute minimum.
Extracting Encryption Metadata from Live Systems
While Elcomsoft Hash Extractor can be used on your computer (where, presumably, you have Elcomsoft Distributed Password Recovery installed), there are times you may want to use the tool on a live system. For this purpose, we are offering the optional portable version of the tool for better portability and flexibility. To create the portable version of Elcomsoft Hash Extractor, do the following.
- Launch Elcomsoft Hash Extractor and select Create portable version.
- Insert a flash drive and take a note of its drive letter.
- Specify the drive letter of the flash drive you’re about to save the portable version to.
- Click Process.
- In a few minutes or a few seconds depending on the speed of your flash drive the process will be finished.
You may now eject the flash drive and start using the portable tool.
Using Elcomsoft Hash Extractor
Elcomsoft Hash Extractor is a small tool included with Elcomsoft Distributed Password Recovery. The tool enables users to set up attacks on a tiny file instead of the original, potentially large document. Since no raw or encrypted data is included in encryption metadata, the hash files produced with Elcomsoft Hash Extractor offer significantly higher level of privacy, allowing remote and cloud processing without the risk of a data leak.
Historically, we developed Elcomsoft Hash Extractor to help attack databases of several password managers – simply because there were too many formats to plug into EDPR without some sort of pre-configuration; more on that in One Password to Rule Them All: Breaking into 1Password, KeePass, LastPass and Dashlane. Later on, we extended the tool to support additional formats.
To extract encryption metadata, do the following.
- Launch Elcomsoft Hash Extractor and select Create portable version.

- From the main window, specify the type of files or documents you are about to extract hashes from. Currently supported are several password managers and document formats (archives such as ZIP and RAR will be added soon).
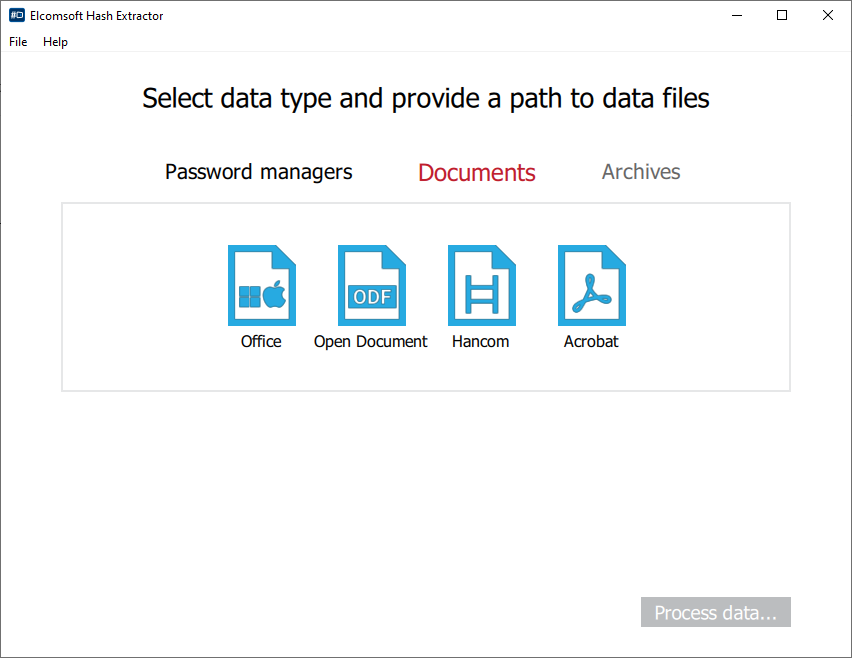
- If you are about to open a Microsoft Office document, select “Office” (which stands for “Microsoft Office”), then specify the file to extract encryption metadata from.
- Specify the drive letter of the flash drive you’re about to save the portable version to.
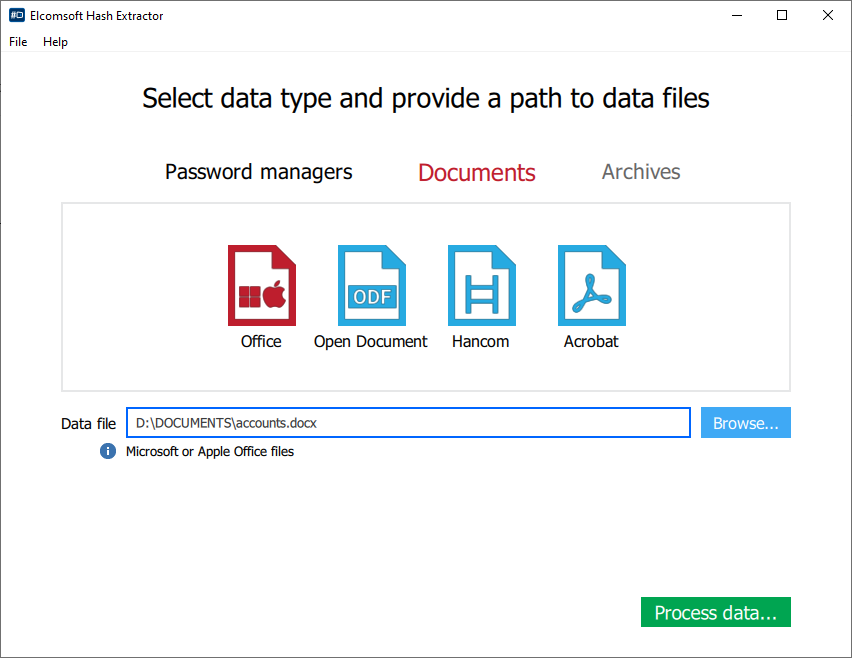
- Click Process.
- In a few minutes or a few seconds depending on the speed of your flash drive the process will be finished.

Once you are done, collect the extracted hash files and open them in Elcomsoft Distributed Password Recovery instead of the original documents.
Conclusion
We are set to continue developing Elcomsoft Hash Extractor to offer even more control over potentially sensitive information. We are about to expand the number of supported formats, and we are working on batch processing to allow extracting encryption metadata from hundreds of files in one go.









