The wide spread of full-disk encryption makes live system analysis during incident response a challenge, but also an opportunity. A timely detection of full-disk encryption or a mounted crypto container allows experts take extra steps to secure access to encrypted evidence before pulling the plug. What steps are required and how to tell if the system is using full-disk encryption? “We have a tool for that”.
In December 2021, we added BestCrypt Volume Encryption 4 и 5 to both Elcomsoft Encrypted Disk Hunter and Elcomsoft Distributed Password Recovery.
The Challenge
Full-disk encryption is an ongoing challenge for forensic experts. Accessing evidence stored on encrypted disk volumes may not be possible without breaking the encryption first. The classic workflow had always involved pulling the plug, taking the disks out, write-blocked imaging and subsequent analysis of the image files.
The classic workflow is flawed. Not only does it lock experts out of evidence stored on encrypted volumes that have been mounted during the acquisition, but depending on the type of protector used to secure the volume the evidence may become completely inaccessible once the disk is removed from the original computer.
We are suggesting a way for securing access to evidence during incident response by analyzing the live system for signs of full-disk encryption. If one or more encrypted volumes are detected, or if there a signs that full-disk encryption might have been used on the system, additional steps must be taken to further investigate the live system in order to secure and preserve evidence that could be lost if the computer was powered off.
Detecting Full-Disk Encryption
In order to detect the presence of full-disk encryption, we suggest using Elcomsoft Encrypted Disk Hunter.
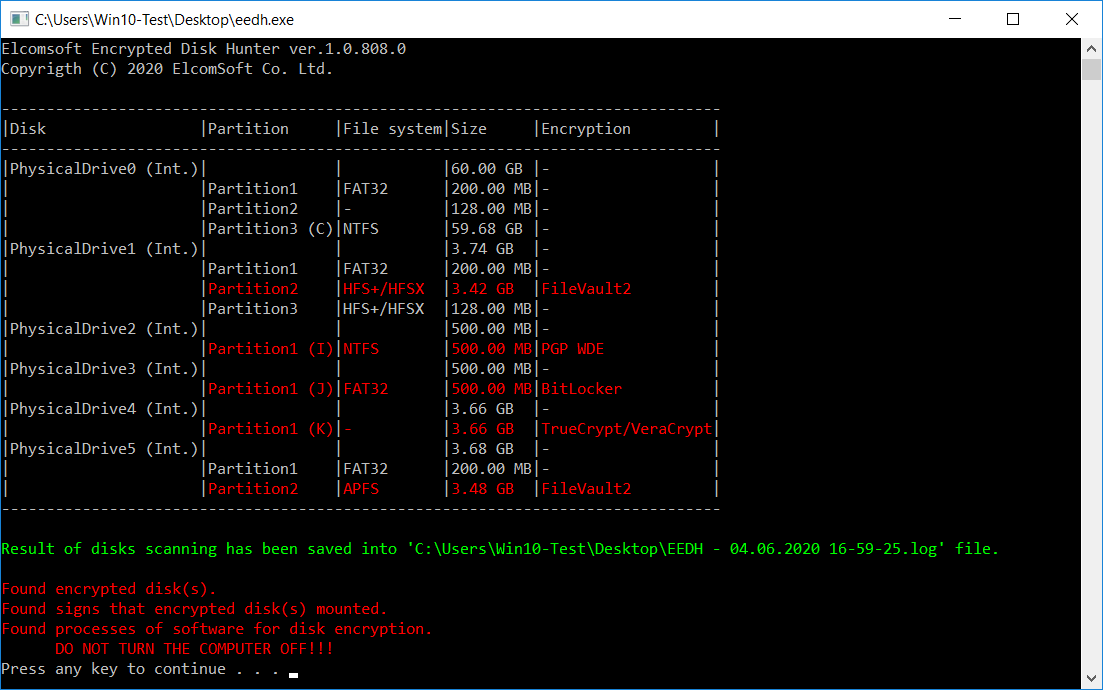
Elcomsoft Encrypted Disk Hunter is a free portable command-line tool to help experts quickly discover the presence of encrypted volumes when performing live system analysis. The tool can detect TrueCrypt/VeraCrypt, BitLocker, PGP WDE, FileVault2, BestCrypt and LUKS. While FIleVault2 and LUKS-encrypted disks that are connected to a Windows computer are rarely encountered in the wild, we have them covered just for those rare cases when you might need them. If the computer is normally running macOS or Linux, you may want to boot from a flash drive using Elcomsoft System Recovery.
Speaking of LUKS encryption, there are two versions: LUKS1 (the common one) and LUKS2 (newer but still rarely used). Elcomsoft Encrypted Disk Hunter only supports the first version for the time being; we are working on adding support for the second.
How does it work?
First and foremost, it requires administrative privileges on the system you are analyzing. Without administrative privileges there is no low-level access to the disks, the computer’s volatile memory and the driver chain.
Once you launch Elcomsoft Encrypted Disk Hunter (which you can do from a portable flash drive), the tool checks the system’s attached storage devices for encryption by looking for characteristic signatures in the drives’ MBR. If one or more encrypted volume is detected, the tool lists the encrypted disks.
After that, the tool checks if any of the encrypted volumes are currently mounted. If no obvious signs of disk encryption are found, Encrypted Disk Hunter checks the system driver chain for TrueCrypt, VeraCrypt and PGP WDE drivers. If a full-disk encryption driver is recognized (we’re looking for truecrypt.sys, veracrypt.sys, PGPdisk.SYS, Pgpwdefs.sys, and PGPwded.sys), the tool will report that an encrypted volume might have been used in the system, even if not currently mounted or attached. This might be your best bet, as certain tools (PGP WDE) routinely block access to disk volumes that are not currently mounted.
What Next?
Depending on the result and after performing the risk assessment, you may want to pursue one of the following routes.
- If no signs of full-disk encryption are found: optionally capture the memory dump; pull the plug and follow the classic routine.
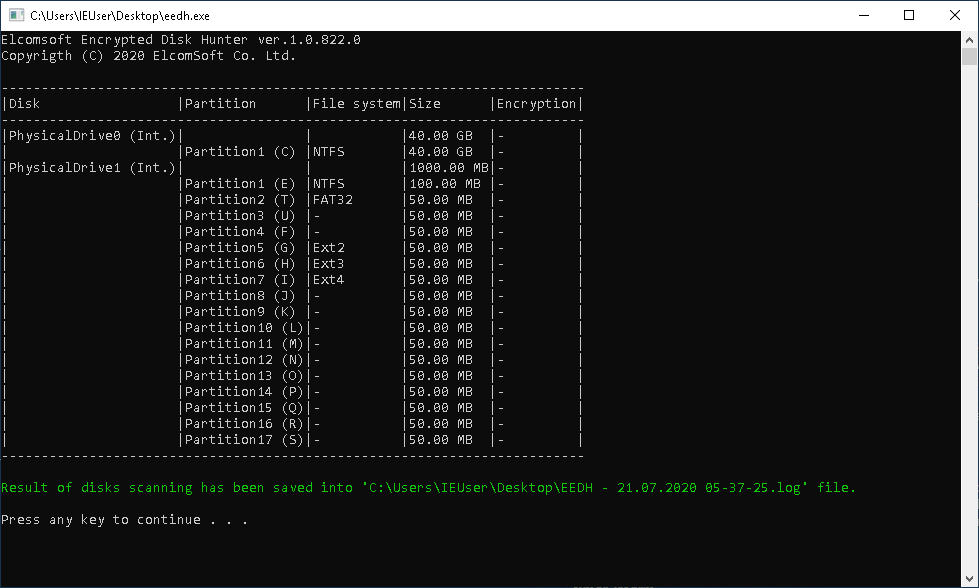
Image 1: No signs of full-disk encryption found
- If signs of full-disk encryption are found: capture the memory dump; investigate live system further.
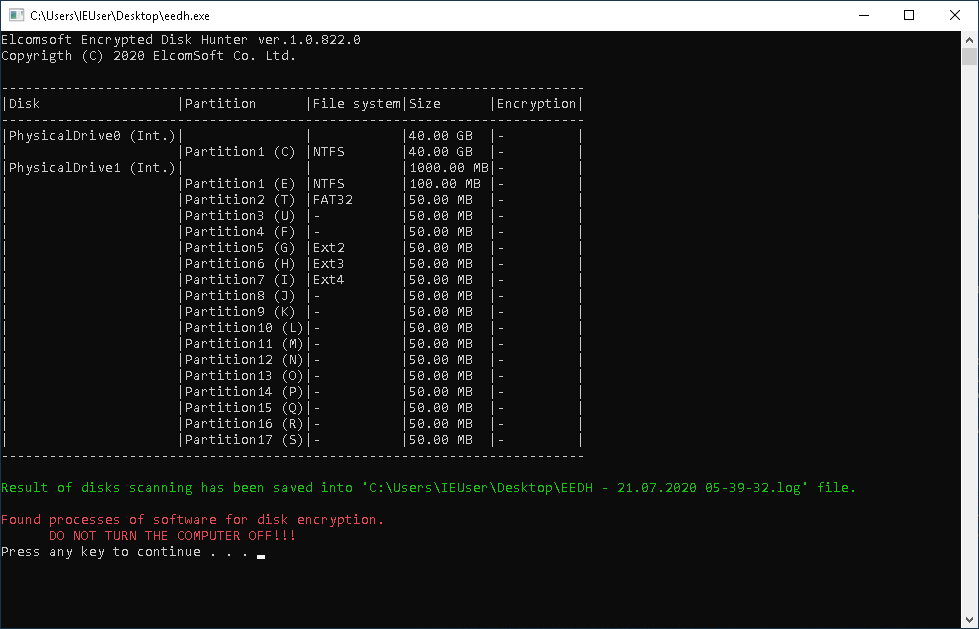
Image 2: While no encrypted volumes are discovered, an active full-disk encryption process is detected. Further investigation required. Do not pull the plug!
- If encrypted volumes are mounted: capture the memory dump; attempt to export recovery keys/escrow keys; time permitting, attempt to extract evidence from encrypted volumes.
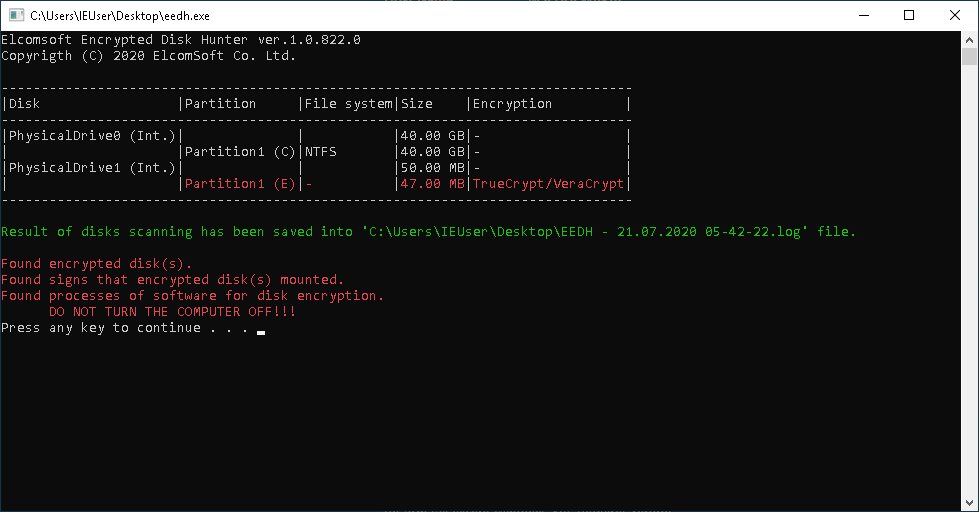
Image 3: A TrueCrypt/VeraCrypt volume is currently mounted. Further analysis mandatory. Do not pull the plug!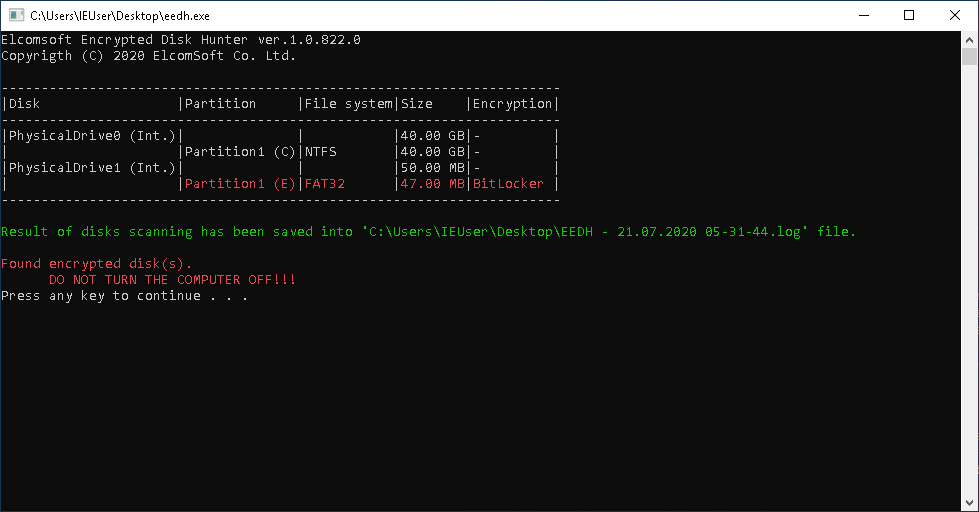
Image 4: A BitLocker volume is detected. Further investigation required. Do not pull the plug!
If at least one encrypted disk partition is mounted, that means that you are either at risk, or you are lucky, depending on which side you are on: protecting your privacy or collecting critical evidence. In the first case, check out our article Introduction to BitLocker: Protecting Your System Disk to avoid common mistakes when protecting your data, and keep in mind that leaving encrypted disks mounted while leaving your computer unattended is a huge risk.
If you are an expert doing the extraction work, read the Unlocking BitLocker Volumes by Booting from a USB Drive article to find out why attacking the password might be fruitless in the case of full-disk encryption; learn about the different types of protectors and the different attack workflows. In any case, do get Elcomsoft Forensic Disk Decryptor, and capture the memory dump to secure access to encrypted evidence.
Why do you need the memory dump? You can use Elcomsoft Forensic Disk Decryptor to scan the memory dump for OTFE keys (on-the-fly encryption keys) that can be used to instantly mount or decrypt the volume without brute-forcing the password. OTFE extraction might be the only method available to unlock BitLocker volumes protected with certain type of protectors (e.g. TPM Only). More about breaking full-disk encryption with Elcomsoft Forensic Disk Decryptor in our blog: Unlocking BitLocker: Can You Break That Password?
If this does not help (or if some of the encrypted disks discovered had not been mounted), use Elcomsoft Distributed Password Recovery to attack the password. EDPR implements all possible optimizations while targeting the human factor, but prepare to wait as brute-forcing passwords to encrypted disks can be slow.
Download Elcomsoft Encrypted Disk Hunter
You can download Elcomsoft Encrypted Disk Hunter free of charge from our official Web site.
Download Elcomsoft Encrypted Disk Hunter
The tool is available as a ZIP archive with no installer. The portable command-line tool is digitally signed. Simply unpack the tool, store it on a flash drive and use on the target system with administrative privileges. We strongly recommend launching the tool directly from the flash drive.







