We have discovered a way to unlock encrypted iPhones protected with an unknown screen lock passcode. Our method supports two legacy iPhone models, the iPhone 5 and 5c, and requires a Mac to run the attack. Our solution is decidedly software-only; it does not require soldering, disassembling, or buying extra hardware. All you need is iOS Forensic Toolkit (new version), a Mac computer, and a USB-A to Lightning cable. In this guide, we’ll demonstrate how to unlock and image the iPhone 5 and 5c devices.
Passcode attacks: know your options
Apple implements strong protection to defend its devices against brute force attacks. While newer devices (the iPhone 5s and subsequent models) rely on Secure Enclave to slow down attacks to a crawl, 32-bit devices such as the iPhone 5 and 5c are not equipped with a hardware security coprocessor. As a result, both the escalating time delays after the entry of an invalid passcode at the Lock screen and the optional setting to wipe the device after 10 unsuccessful attempts are enforced in software by iOS. Disabling these mechanisms removes the risk of losing the data and turns off the escalating time delay, enabling the attack to work at a full speed of exactly 13.6 passcodes per second, which is very close to Apple’s target of 80ms between passcode attempts.
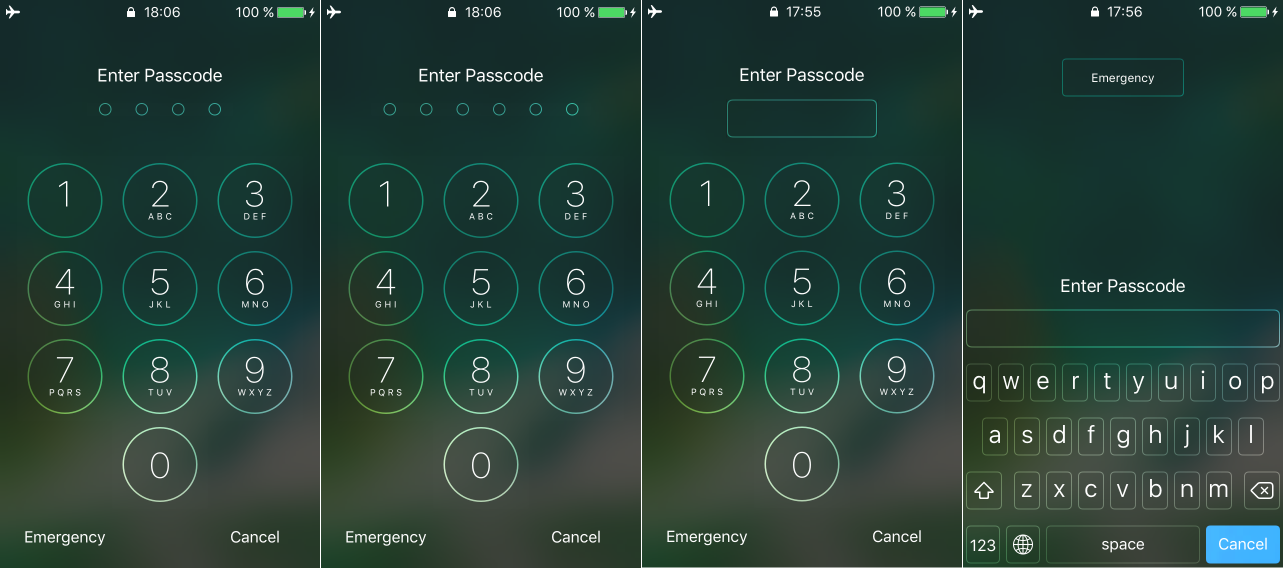
Breaking 4-digit and 6-digit PINs
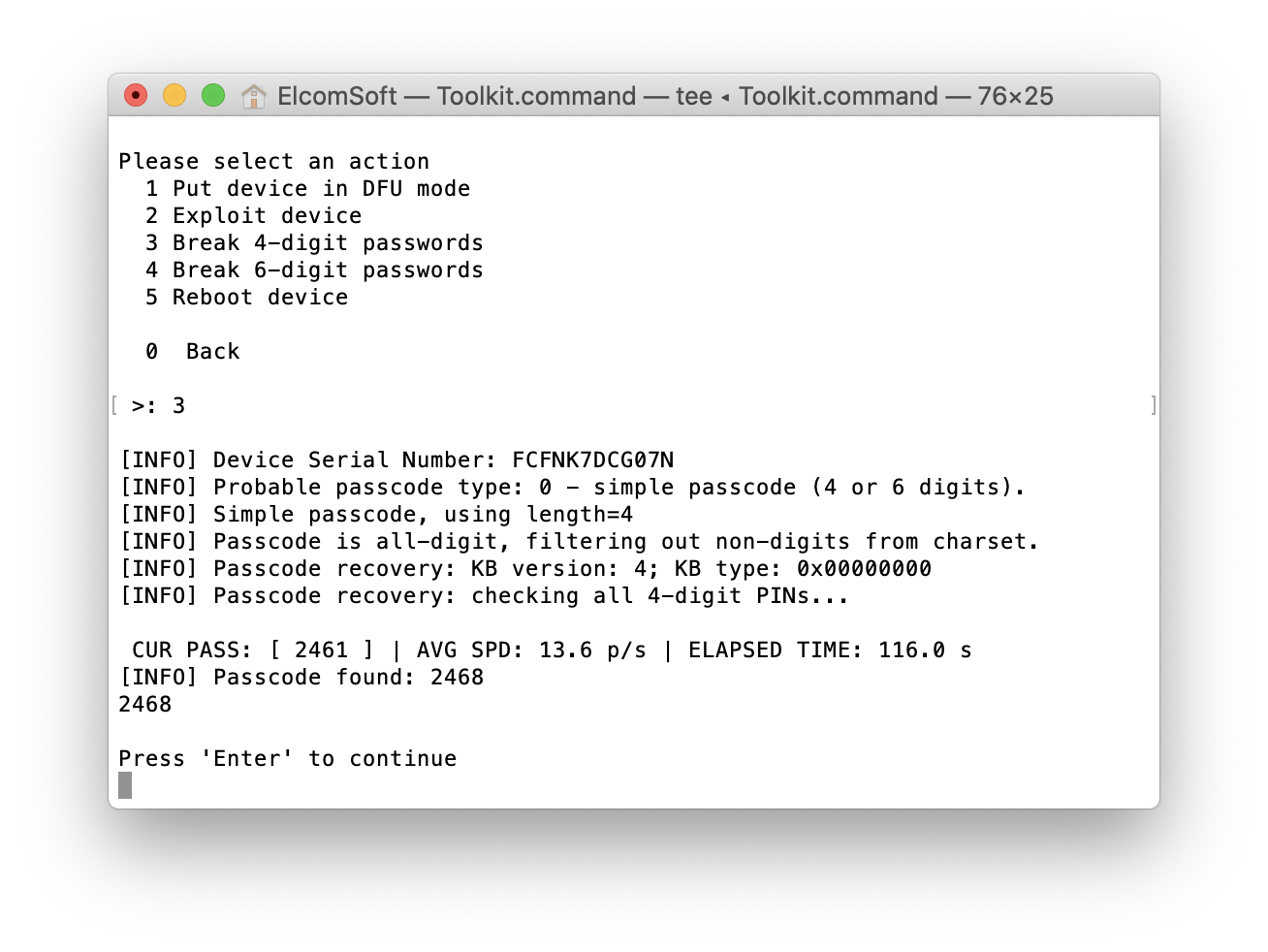
Considering the speed of 13.6 passcodes per second, it only takes 12 minutes to try all possible combinations of 4-digit PINs. The enumeration of all 6-digit PINs, however, will take up to 21 hours. For this reason, we’ll try the most popular passcodes first. There are 2910 commonly used 6-digit PINs, and it only takes about 4 minutes to test them all. Following this list are the 6-digit PINs based on the user’s date of birth; there are around 74K possible combinations that take about 1.5 hours to try. Only after these options are exhausted do we start the full brute-force attack that lasts around 21 hours.
Alphanumeric passcodes
At the given speed, the recovery of an alphanumeric passcode becomes extremely iffy unless you have targeted dictionary of the user’s other passwords. For the time being, iOS Forensic Toolkit does not support alphanumeric passwords. If an alphanumeric passcode is detected, you’ll see the “unsupported” message, and the attack will stop. We will probably add support for alphanumeric passwords in the next version.
Compatibility and pre-requisites
In order to launch the attack, you will need all of the following.
- A compatible iPhone model. Supported devices include the iPhone 5 (A1428, A1429, A1442) and iPhone 5c (A1456, A1507, A1516, A1526, A1529, A1532) models.
- A desktop or laptop computer with macOS 10.12 (Sierra) through 10.15 (Catalina).
- A Lightning cable. Please use USB-A to Lightning due to known incompatibilities in Apple’s and most third-party USB-C to Lightning cables. You can use the optional USB-C to USB-A adapter if needed.
- iOS Forensic Toolkit 6.40 or newer.
Steps to unlock the iPhone 5c
First, install iOS Forensic Toolkit and make yourself familiar with the checkra1n jailbreak by following these preliminary steps:
- Download Elcomsoft iOS Forensic Toolkit. Insert the USB dongle.
- Install the toolkit by following the instructions in How to Install and Run iOS Forensic Toolkit on a Mac. Note that there is an extra mandatory step on macOS Catalina.
- Check out checkra1n Installation Tips & Tricks, in particular:
- No hubs!
- Use USB-A to Lightning cable only (no USB-C to Lightning);
- Make sure the phone is charged to at least 20%.
Once you have installed, configured and launched Elcomsoft iOS Forensic Toolkit, enter ‘P’ in the main window to access the passcode cracking functionality.
The following options will be available:
[1] Put device in DFU mode
[2] Exploit device
[3] Break 4-digit passwords
[4] Break 6-digit passwords
[5] Reboot device
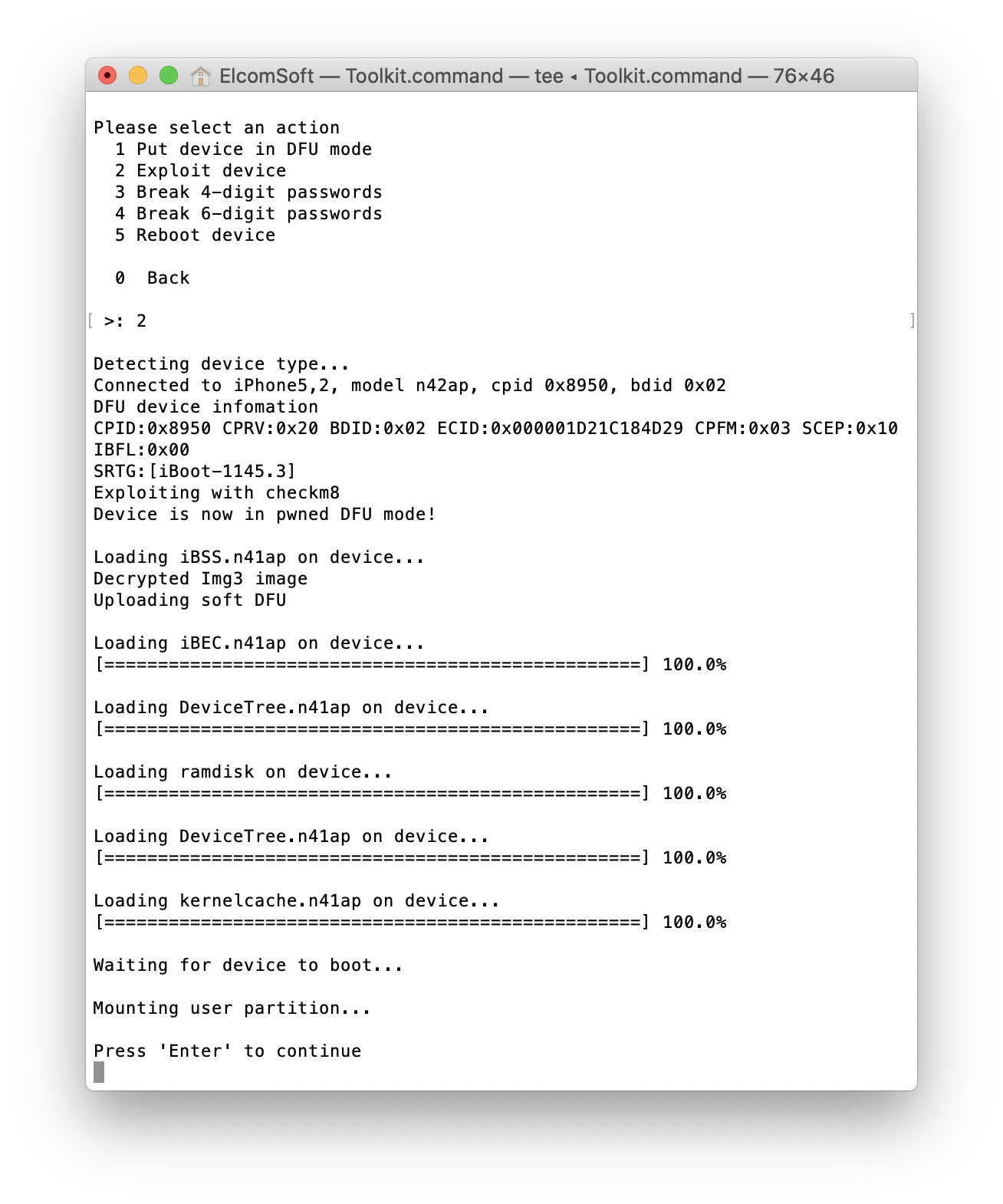
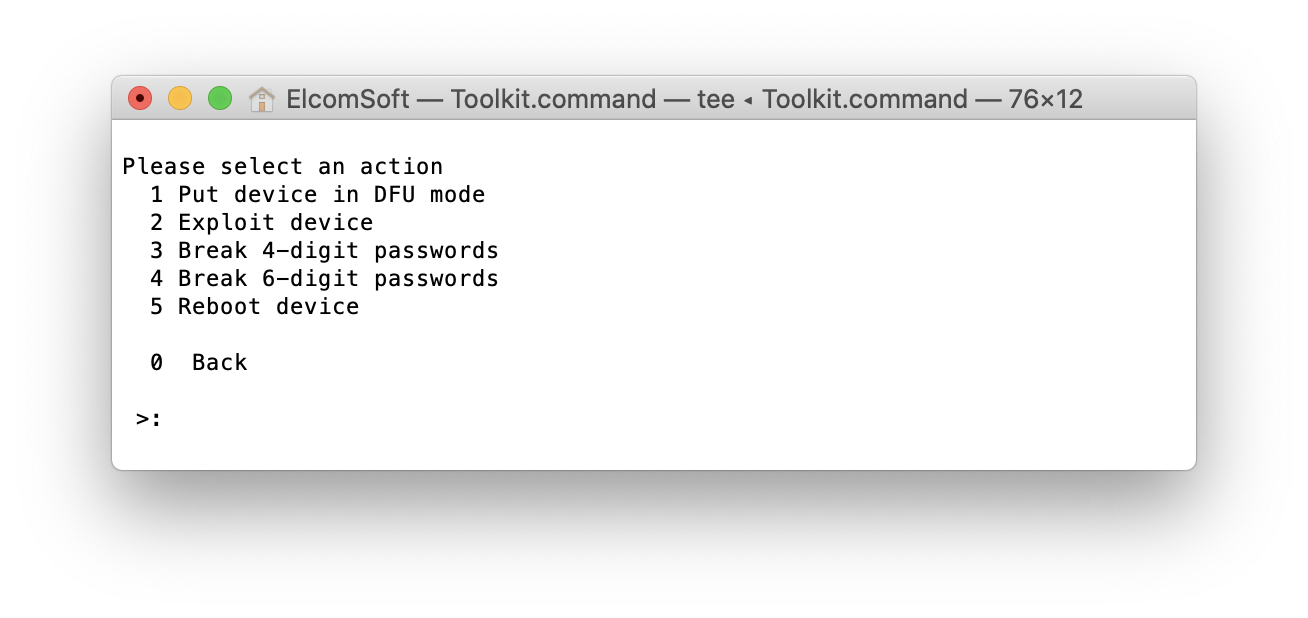 Since the passcode recovery functionality is based on the checkm8 exploit, you will need to switch the device into DFU mode. This can be only done manually on the device. However, selecting the [1] option in the Toolkit will guide you through the process.
Since the passcode recovery functionality is based on the checkm8 exploit, you will need to switch the device into DFU mode. This can be only done manually on the device. However, selecting the [1] option in the Toolkit will guide you through the process.
More than one method of switching the phone into DFU mode may exist for the device (more on that here). We found the following one to be easier than the others. Follow these instructions:
- Make sure the device is not connected to the computer and turned off.
- Press the Home button, insert the lightning cable, keeping the Home button pressed until the device reads “Connect to iTunes” on the display; release the Home button.
- Press and hold the Home and Sleep/Power (top) buttons together for 8 seconds (Apple logo will appear for some time, then the screen turns black).
- Release the Sleep/Power button but keep the Home button pressed for 8 more seconds.
- Release the Sleep/Power button. If you did everything right, the screen should remain blank, and the phone should appear in iTunes or Finder (depending on your macOS version) as an iPhone in recovery mode. Now it is ready for further steps.

Once the device is in DFU mode, select the second option to exploit by making it boot a special custom firmware. This process is safe for the phone data. It does not change anything on the device since the exploit works entirely in the device volatile memory. There will be no traces left on the device.
If the exploit fails for any reason, repeat the process from the beginning. Note that you will have to reboot the device by pressing Home and Power buttons simultaneously for 8 seconds, and re-enter the DFU mode. Also note that, from the point of view of installing the exploit, going straight to DFU works in most cases. However, if you have errors when attempting to exploit the device, we’ve seen reports where going through the Recovery mode fixes the issues. The developers of the checkra1n jailbreak also recommend using the Recovery mode first. You may try it either way; if the exploit does not work when going straight the DFU, try to get through Recovery mode. This is how the error message may look like:

Another common error is Failed to upload iBSS. This is generally nothing to worry about. Your device is still compatible with the checkm8 exploit and our method in general, you just need another try. Sometimes it takes up to 5 attempts, and there is nothing we can do about that: this is more about the hardware and the driver quality, the issues that cannot be fixed in our software.
Once the device is successfully exploited and the user partition is mounted, you can run the recovery of 4-digit or 6-digit passcodes.
Breaking a 4-digit PIN normally takes 12 minutes or less, while the complete enumeration of all possible 6-digit passcodes may take up to 21 hours. Alphanumeric passwords are not supported at this time.
After the passcode is discovered, reboot the iPhone by selecting the last menu item. Now when you have access to the device, the data extraction will be another thing. We will soon add keychain decryption and full file system extraction for these devices.
Conclusion
The iPhone 5 and 5c are now almost 7 years old, yet many of them are still stored in forensic labs, waiting to be extracted. In some parts of the world, these inexpensive iPhones are still in active circulation. It took years for the first exploit to appear at an outrageous price, and even more time for reasonably priced solutions. Today, we are bringing the cost of high-speed iPhone 5 and 5c unlocks down, offering a software-only solution that requires no soldering, no disassembling and no extra hardware.










