The number of iOS 14 users is on the raise, and we will see it running on most Apple devices pretty soon. Apple had already stopped signing the last version of iOS 13 on all but legacy hardware. Soon, we will only see it running on the iPhone 5s and iPhone 6 which didn’t get the update, and on a small fraction of newer devices. If you are working in the forensic field, what do you need to do to make yourself ready for iOS 14? Our software may help.
Speaking of iOS 14 itself, it does not bring much new that could be useful for forensic investigators. We’ve covered some of the changes in iOS 14 Forensics: What Has Changed Since iOS 13.7? The first step is always data acquisition, followed by the analysis. Let’s review what you can do with iOS 14 using the updated Elcomsoft iOS Forensic Toolkit released today.
Extended logical acquisition
Right when the first beta of iOS 14 had appeared, we tried all supported acquisition options that include:
- Extended device information, including the list of installed apps and their properties
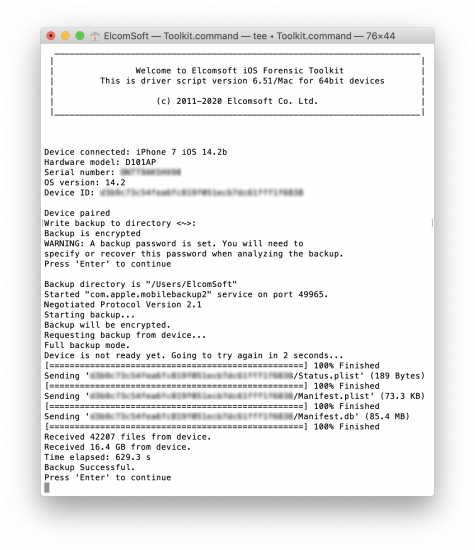
- iTunes-style backups
- Media files (pictures, videos and metadata)
- Crash & diagnostics logs
- Shared app data
Everything worked. But in the final release (or in the late betas), iOS backups stopped working in our tool. We discovered that the backup protocol (which, as you know, is implemented in the iOS itself) was slightly changed, but the fix was easy. So the new version of iOS Forensic Toolkit extracts everything listed above, including backups. Backup acquisition is sometimes harder than it sounds (considering all the password-related issues), read The Most Unusual Things about iPhone Backups for details.
Full file system & keychain acquisition
Speaking of the revolutionary, forensically sound agent-based acquisition method that does not require jailbreaking – it’s not yet ready for prime time. The agent-based extraction method remains compatible with iOS 9 through iOS 13.5, leaving iOS 13.6 and 13.7 out for the time being. As new exploits become available, we will add support for the new versions. For now you are limited only to devices supported by the checkra1n jailbreak. At this time, supported devices include the iPhone 6, iPhone 6 Plus and iPhone SE (first gen) only. The compatible iPad models are also supported, but we have yet to explain what “compatible” devices mean as there are 19 different iPad models. iPhone 7 and iPhone 7 Plus support will be available soon, while iPhone 8 and iPhone X support is questionable; it looks like Apple had found an effective way to protect these models from the checkm8 exploit using Secure Enclave.
What can you do with checkra1n on the iPhone 6s/SE running iOS 14? If the passcode is known, all the data including keychain can be acquired, and it is a lot more than just backups: lots of system databases, third-party application data, temporary and WAL files, etc. If the passcode is not known, you can still perform BFU (Before First Unlock) acquisition even of locked and disabled devices. The scope of the data that can be extracted in BFU mode is modest, but something is still available, and it is much better than nothing.
The following versions of iOS are supported: iOS 14.0, iOS 14.0.1 and iOS 14.2 (beta 1 and beta 2). The latest checkra1n also supports several iPad models including the 5th gen, Mini 4, Air 2 and 1st gen iPad Pro, as well as Apple TV 4 and 4K. Note that some of these models are based on the SoC that is different from the one used in iPhone 6s/SE (A9). No Apple Watch support yet (theoretically it might be possible).
Cloud acquisition
Cloud acquisition is a life-server in many situations, especially when the device is missing, broken or otherwise unavailable. Cloud extraction may return lots of data that is not available on the iPhone itself, including deleted data or data originated from another device. iOS Forensic Toolkit will not help you here, but use Elcomsoft Phone Breaker instead, which is the most comprehensive product of this kind on the market. Supporting all iOS versions (including the now-current iOS 14.2 beta 2), it supports iCloud backups, about 20 categories of synced data (including “end to end encrypted” such as the keychain, messages, Health, Apple Maps and so on), and all files stored on iCloud Drive, including third-party data which is otherwise not available.
Other updates
Extracting a jailbroken device? You have probably noticed the two prompts appearing at the time iOS Forensic Toolkit starts and before it establishes a connection to the iPhone:
- SSH port number
- root password
We have now decided to eliminate them. The root password is ‘alpine’ by default, and it never changes if you install the jailbreak yourself for acquisition purposes. In rare cases where you must provide a different root password, you can change it by modifying the SSHPASS value in the script.
The other option (port number) need an explanation. For all modern jailbreaks, an SSH connection established by OpenSSH or DropBear SSH is made over the standard port 22. There is currently only one exception: checkra1n in BFU mode, when OpenSSH is not installed, and the jailbreak uses the built-in DropBear SSH client. In this situation, the port number is 44.
Since this release, the port number 22 becomes the default in our toolkit. However, if you perform BFU acquisition via checkra1n, change the IPORT setting in the script source and restart the toolkit.
Old but worth mentioning
iOS Forensic Toolkit is a powerful and flexible tool, but sometimes it requires a bit of fine-tuning. Just to remind you a few things (honestly, sometimes I forget about some of them myself):
- macOS: do not forget to clean ‘quarantine’ flag from the DMG file you’ve downloaded
- macOS: do not run the toolkit right straight the mounted DMG, but copy the contents to the local disk first
- Windows: run the toolkit with Administrator privileges
- If you are using agent-based acquisition frequently, you can set Apple Developer Account credentials in AGENT_ID, AGENT_PASSWORD and AGENT_TEAMID to avoid extra prompts
- macOS: in agent acquisition, use the regular (not app-specific) password for both developer and non-developer accounts, then go through 2FA
- Windows: always use an app-specific password
- with non-developer accounts, do not forget to restrict Internet connections
The future
What does the future hold for iOS forensics?
Extended logical acquisition: will most likely stay in its current shape in all future iPhone models and iOS versions, unless Apple removes the Lightning port completely. Even then, it will probably allow to acquire the data over the air; this is extremely hard to predict at this point.
Agent acquisition: depends on the availability of exploits. We cannot make promises, but it looks like we will be able to add support for iOS 13.6 and 13.7 soon. As for iOS 14, there is no ETA, but some rumors on new exploits are already coming.
Jailbreaking: for system-level jailbreaks, the situation is like above. With new exploits, we will get both new jailbreaks and (probably after some time) support for agent acquisition. Speaking of checkra1n, support of iPhone 7 and iPhone 7 Plus running iOS 14 is coming.
Cloud acquisition: the most difficult question. We are doing everything we can to keep things running, but Apple have the technical ability to block our software from working, at least from accessing iCloud backups. Contrary to the acquisition of physical devices, a solid part of iCloud engine is beyond our control.



