Media files (Camera Roll, pictures and videos, books etc.) are an important part of the content of mobile devices. The ability to quickly extract media files can be essential for an investigation, especially with geotags (location data) saved in EXIF metadata. Pulling pictures and videos from an Android smartphone can be easier than obtaining the rest of the data. At the same time, media extraction from iOS devices, while not impossible, is not the easiest nor the most obvious process. Let’s have a look at tools and techniques you can use to extract media files from unlocked and locked iOS devices.
Ways to Extract Media Files
There is more than one way you could use to extract media files.
Physical acquisition remains the best acquisition method available for the platform. However, if the device is locked (and you don’t know the passcode), or if it is running a version of iOS without a jailbreak, physical acquisition remains more of a wishful thinking rather than a real possibility. (On a side note, we have reasons to believe a public jailbreak for iOS 10.3 and 11.0 through 11.1 may appear in near future). All things considered, logical acquisition remains the go-to approach for the law enforcement.
Logical acquisition is a safe, easy alternative to physical. Returning almost as much information (and pretty much everything as far as media files are concerned), logical acquisition is a clean and relatively fast method of obtaining the files of interest. Better yet, logical acquisition may work even for locked iOS devices if you have a valid lockdown file (pairing record) pulled from the suspect’s computer, which allows making an iTunes-style backup from locked devices even if the passcode is not known.
Logical acquisition is not without its share of issues. A backup password, if enabled, can become a major roadblock to accessing information. While it could be possible to reset the backup password on devices running iOS 11, one still needs to know (and enter) the user’s passcode in order to perform the reset. On older devices, backup passwords are even more of a roadblock. While updating to iOS 11 and removing the password might be a viable strategy in many cases, for some other purposes the process is just not sufficiently forensically sound. In addition, as mentioned above, you must know the passcode in order to upgrade the OS and remove the backup password. If the device is locked and all you have is a lockdown file, logical acquisition may not be an option after all.
If the phone is unlocked, or if it is locked but you have a lockdown record (and that phone was unlocked at least once after it was powered on or rebooted), you now have the third option.
Media extraction via iOS Forensic Toolkit 2.50 and newer (the ‘M’ command) uses a dedicated mechanism to access and extract media files including Camera Roll (pictures and videos), information on photos & videos editing, books from the iBooks app (including e-books and PDF files), voice recordings and items from the iTunes media library.
This method is absolutely not an exploit of a newly discovered vulnerability. iOS Forensic Toolkit makes use of a service running on the iPhone. Desktop operating systems (Windows and Mac) are connecting to this service when transferring pictures with Image Capture (macOS) and Photos (Windows 10) apps. However, iOS Forensic Toolkit pulls significantly more information compared to those apps. Compared to Windows/Mac apps, iOS Forensic Toolkit does the following:
- Extracts music, iBooks and PDF files in addition to Camera Roll items
- For every picture, iOS Forensic Toolkit pulls information about if (or when) the image was edited
- Supports lockdown records to pull media files from a locked device
Now when you know the basics let’s switch to iOS Forensic Toolkit and have a look at how media extraction actually works.
How to Extract Media Files with iOS Forensic Toolkit
In order to extract media files from an iPhone using iOS Forensic Toolkit (version 2.50 or newer required), follow one of the two guides depending on whether or not you can pair the device to your computer.
Unlocked iPhone (iOS 11: passcode is known)
If the iPhone you are about to extract is already unlocked and (in the case it runs iOS 11) you know its passcode, do the following steps.
- Launch iOS Forensic Toolkit by invoking the Toolkit-JB command.
- Connect the iPhone to the computer using the Lightning cable. If you are able to unlock the iPhone, pair the device by confirming the “Trust this computer?” prompt and (in the case of iOS 11) entering device passcode.
- From the main window, enter the “M” (Media) command.
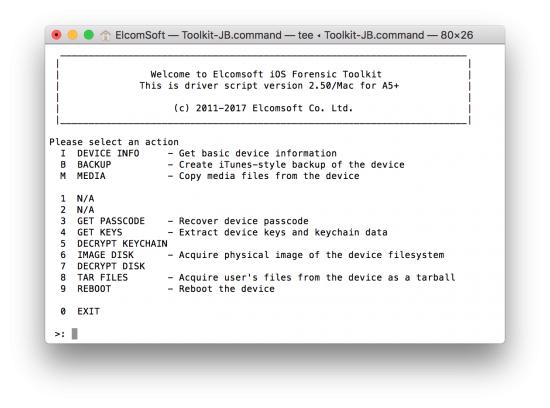
- Of the device is not paired with the computer yet, you will be prompted for a lockdown file. Provide path to the lockdown record (hint: when prompted, you can drag and drop the lockdown file onto the iOS Forensic Toolkit window). We have a couple of comprehensive writeups on lockdown files and their exact location on the user’s computer here and here. If the lockdown file is valid, you will be also prompted for path to save the media files to (AFC by default; in the current folder on Windows or under user’s Home folder on macOS).
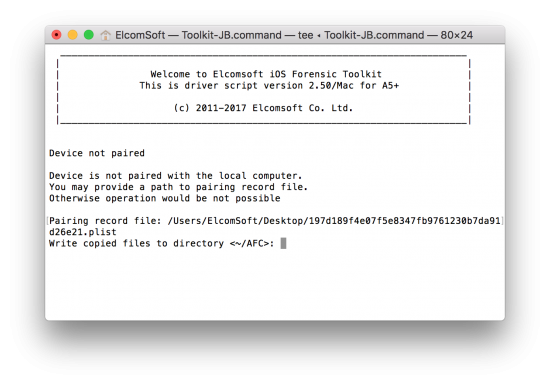
- The files will be extracted and saved on your computer. Depending on the amount of data, the process may take from several seconds to nearly half an hour.
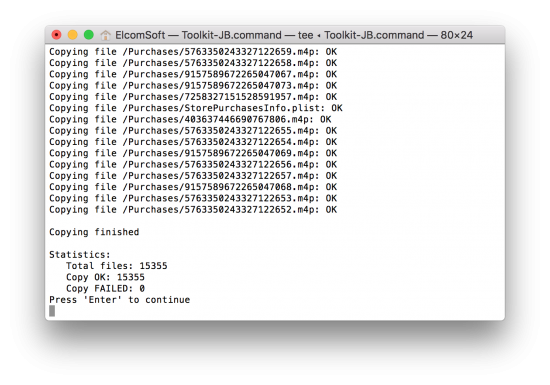
Accessing Extracted Data
Our test device contained over 15 thousand files with the total size of 27GB, and it took about 20 minutes. The extracted files are saved preserving the original Media folder structure of the iOS device being acquired.
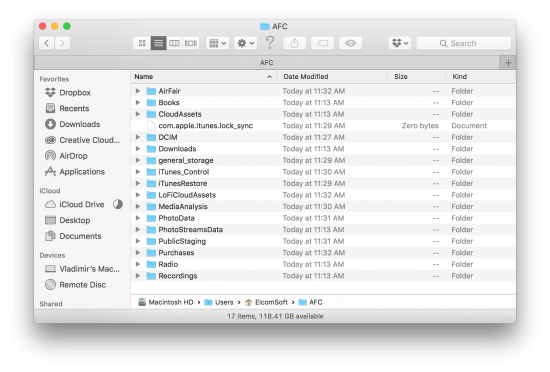
While the number of data may look overwhelming at first, the most important folders are:
- DCIM: contains pictures and videos (Camera Roll). This folder contains multiple subfolders named “XXXAPPLE”, where XXX is a number ranging from 100 to 999.This is actually the only folder that would be available if you accessed the device via standard means.
- Books: files from the iBooks app.
- Purchases: purchased tunes (*.mp4 files). Note that none of these files are included in iOS system backups.
- PhotoData: information about photo edits (cropping, applying filters and special effects etc.); links to photo albums; thumbnails database.
- Media Analysis: photo analysis data (for quickly searching by category/object).
- Recordings: audio recordings such as voice snippets.
In addition to these folders, you will be getting a number of SQLite databases and PLIST files. At this time, we have not analyzed any of those databases. Notably, SQLite databases are extracted complete with WAL (Write Ahead Logs) and SHM data, which includes uncommitted transactions.
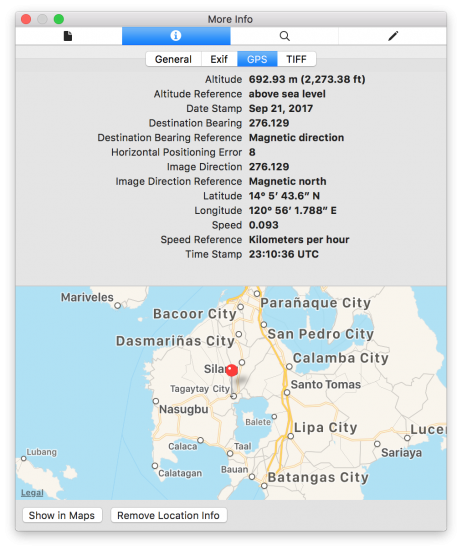
Extracted images may contain EXIF information, of which location data has arguably the most forensic interest (on macOS, select [Tools] | [Show Inspector] in Preview app):
A Word on HEIF/HEVC Files
iOS 11 and macOS 11.13 (High Sierra) added support for HEIF (Hign Efficient Image File Format) and HEVC (High Efficient Video Codec) formats for newer devices including iPhone 7/7 Plus and newer, iPad Pro 10.5 and iPad Pro 12.9 2nd gen (https://support.apple.com/en-us/HT207022).
Since these formats are new and do not currently have native support by any operating systems other than iOS 11 and macOS High Sierra, images captured in these new formats may be automatically converted on the fly while you copy them to your computer. Whether or not the automatic conversion is enabled is controlled by the TRANFER TO MAC OR PC option on the iOS device. If that option is set to Automatic, the images (and videos) will be automatically converted to JPEG and MOV formats respectively while you are transferring them to your computer using Image Capture or Photos on macOS.
Elcomsoft iOS Forensic Toolkit always retrieves photos and videos in their respective original formats regardless of the conversion setting of the iOS device. If the device is locked and you’re accessing media files via a lockdown record, iOS Forensic Toolkit is the only tool on the market to produce a forensically sound extraction of media files in the original format.
Conclusion
The new media extraction method in iOS Forensic Toolkit 2.50 offers a quick and easy way to extract media files from both unlocked and locked iPhone and iPad devices without resorting to local backups.








