In iOS forensics, cloud extraction is a viable alternative when physical acquisition is not possible. The upcoming release of iOS 13 brings additional security measures that will undoubtedly make physical access even more difficult. While the ability to download iCloud backups has been around for years, the need to supply the user’s login and password followed by two-factor authentication was always a roadblock.
Some five years ago, we learned how to use authentication tokens to access iCloud backups without a password. In Breaking Into iCloud: No Password Required we discussed the benefits of this approach. During the next years, we learned how to use authentication tokens to access other types of data stored in iCloud including the user’s photo library, browsing history, contacts, calendars and other information that Apple synchronizes across all of the user’s devices that are signed in to the same Apple account.
Many things have changed since then. Tokens can no longer be used to access iCloud backups, period. Tokens cannot be used to access passwords (iCloud Keychain), Screen Time, Health and Messages. Sometime last year Apple pinned authentication tokens to a particular computer, making them usable just from the very PC or Mac they’ve been created on. It took us more than a year to figure out a workaround allowing experts to transfer authentication tokens from the user’s computer. Even today, this workaround is only working if the user had a macOS computer. With this number of restrictions, are authentication tokens still usable? What can you obtain from the user’s iCloud account with an authentication token, and what can be accessed with a login and password? How two-factor authentication affects what’s available in an iCloud account, and why knowing the screen lock passcode (or Mac system password) can help? Keep reading to find out.
iCloud Security
Apple does not own the servers (or, rather, services) that store their users’ data. iCloud backups, photos, messages, and even passwords are kept on third-party servers owned by Amazon, Microsoft, Google, AT&T and the Chinese government (for users residing in continental China). This, however, does not mean that Amazon, Google or the Chinese government has access to any of that data. Let’s have a look at how Apple secures iCloud data against physical threats, taking an iCloud backup as an example.
The user’s iCloud backup is broken into chunks, with each individual chunk being uploaded (in seemingly random order) to one or more servers. Each chunk is encrypted with a unique, individual encryption key. Without those keys, the chunks, even if assembled in the right order, will remain being blocks of encrypted binary data.
What about the encryption keys? The keys are always stored on Apple’s own servers in a data center in Cupertino. They are never passed to Apple’s partners, contractors or the Chinese government (unless serving a legal request).
A few things become immediately obvious when considering this protection scheme.
- Apple has full access to encrypted information as the company has both the data and the encryption keys.
- Apple can decrypt the data and pass it along to the law enforcement.
- Someone with proper authentication credentials can access both the data and the encryption keys, thus retrieving and decrypting the backup.
iCloud Backups Security
Speaking of iCloud backups, it is important to understand that while most parts of the backup can be decrypted with proper credentials, certain content of iCloud backups will be additionally encrypted with highly secure, hardware-based encryption keys. The encryption happens inside an iOS device (on the iPhone or iPad itself); none of that data leaves the device unencrypted in any form. As a result, such content can be only restored onto exactly the same hardware device it was backed up from. In iOS 12 and iOS 13 (beta), this content includes:
- The keychain. User’s Safari and third-party app passwords remain securely protected within an iCloud backup (remember, we are speaking about the keychain stores in iCloud backups only; more on cloud keychain protection and extraction later). The keychain can be only decrypted on the device that produced the backup. Neither Apple nor law enforcement can access this part of iCloud backups without having the original device.
The following items are never included in iCloud backups:
In addition, some items are specifically excluded from iCloud backups if the user enables iCloud sync for that data category. These items include:
- iCloud Photos
- Messages (SMS and iMessages)
iOS 13 additionally excludes the following two data categories (new!):
iCloud Backups and Tokens
In our 2014 article Breaking Into iCloud: No Password Required we discussed the use of authentication tokens to access iCloud backups. This is no longer possible (for a long time).
iCloud authentication tokens cannot be used to access iCloud backups. Period.
Synchronized Data
Since the appearance of iCloud backups back in 2011, Apple is slowly moving things away from backups. The introduction of iCloud Photo Library made photos sync across devices via a dedicated service in iCloud. Once the user enabled their cloud photo library, the pictures would no longer save into iCloud backups. Similarly, once the user enabled iCloud Messages (requires iOS 11.4 and newer), the messages would no longer save in iCloud backups, but rather sync via the user’s iCloud account. iOC 13 will stop including Call Logs and Safari history in iCloud backups; these two categories will be available exclusively as synchronized data.
Authentication tokens are good for extracting synced data (except protected categories). The following summarizes the protection of synchronized information in iCloud:
- To access synced iCloud data, one only needs the user’s Apple ID, password and 2FA code.
- You can also use authentication tokens to access synced data.
- Apple has technical ability to access synced data in iCloud.
- Synced data is provided when serving government requests.
- Synced data is provided when serving GDPR requests.
- Finally, third-party apps such as Elcomsoft Phone Breaker can extract synced iCloud data.
Some iCloud Data is Encrypted with a Passcode
Certain data categories receive a different treatment.
The following data types can be only decrypted if you know the screen lock passcode (or Mac system password) of a device registered with the same Apple ID:
- iCloud Keychain. The keychain contains the user’s synced logins and passwords from Safari browser and third-party apps and some authentication tokens. Most importantly, the iCloud Keychain also stores the encryption keys protecting the other encrypted data types (you cannot decrypt e.g. Messages without first decrypting the iCloud Keychain).
- Messages in iCloud. This includes SMS and iMessages.
- Since iOS 12, Health data. The protection of synced Health data has changed in iOS 12 compared to iOS 11; more on that in the next chapter.
In order to access these protected data categories, you will need all of the following:
- The user’s Apple ID and password
- One-time 2FA code (there will be no iCloud sync for any of those categories without 2FA)
- Passcode or system password to a device already enrolled in iCloud Keychain
Consecutively, the following access restrictions apply:
- Authentication tokens cannot be used to access any of these types of data.
- A typical user will have no problems syncing the Keychain, Health or Messages with iCloud. When initializing a new iPhone to receive synced data, they just need to provide their screen lock password code to their old iPhone (or any device that has iCloud Keychain enabled including Mac computers).
- Apple does not have access to synced passwords, messages or Health data. Even if the data is stored on Apple servers, Apple cannot decrypt it.
- Apple will not provide any data belonging to protected categories when serving government requests or GDPR requests (with one exception).
- Extraction with third-party apps is restricted yet still possible if one knows the device passcode/system password (Elcomsoft Phone Breaker).
Exception: Protection and Extraction of Health Data in iOS 11 and iOS 12
Starting with iOS 11, Apple implemented health data sync with iCloud. In iOS 11, all types of data except CDA records would sync with iCloud in exactly the same manner as other types of synchronized data such as pictures or contacts. There were no additional protection for activities, sleep, nutrition, mindfulness and similar types of data.
Protection of Health data in iCloud: iOS 11
- To access synced Health data, one only needs the user’s Apple ID, password and 2FA code.
- Apple has technical ability to access Health data in iCloud.
- Health data is provided when serving government requests.
- Health data is provided when serving GDPR requests.
- Finally, third-party apps such as Elcomsoft Phone Breakercan extract Health data.
Protection of Health data in iCloud: iOS 12 and 13
iOS 12 implements a different approach to protecting Health data in iCloud, employing secure encryption with a key stored in iCloud Keychain. The actual data is now stored in a different (encrypted) container compared to iOS 11. Interestingly, the old (unencrypted) container could remain available for some time after the user updated their last device to iOS 12.
The encryption key is protected with the user’s passcode (screen lock password or system password) of a device already participating in Health sync. This ensures that Apple cannot access Health data (or the iCloud Keychain if that matters) stored in the cloud. We consider this protection mechanism to deliver sufficient security.
In order to access Health data synced with iCloud by devices running iOS 12 and newer, one needs all of the following information:
- The user’s Apple ID and password
- One-time 2FA code (there will be no iCloud sync without 2FA)
- Passcode or system password to a device already enrolled in Health iCloud sync
Consecutively, the following access restrictions apply:
- When initializing a new iPhone, the user needs to provide their screen lock password code from old iPhone (or any device that has iCloud Keychain enabled including Mac computers) to receive synced Health data.
- Apple does not have access to synced Health data. Even if the data is stored on Apple servers, Apple cannot decrypt it.
- Apple will not provide Health data when serving government requests or GDPR requests.
- Extraction with third-party apps is restricted yet still possible (Elcomsoft Phone Breaker).
Two-Factor Authentication: Advantages
In Apple’s land, two-factor authentication affects… everything. If the user enables two-factor authentication on their account, they gain a range of abilities that aren’t available for accounts without 2FA. They can instantly reset their Apple ID password from their iPhone using just the passcode. They can disable Find My iPhone without knowing the iCloud password. Forensic experts find a few other features useful when it comes to two-factor authentication. Only accounts with two-factor authentication can do the following:
- Sync passwords through iCloud (iCloud Keychain)
- Sync Messages (SMS and iMessages)
- Sync Health data
- Sync Screen Time data (including Screen Time data of dependents’ accounts)
In a way, two-factor authentication is a blessing for the law enforcement because accounts with 2FA sync more information through iCloud compared to unprotected account. Passing the 2FA prompt can be as simple as obtaining the user’s SIM card and using it in another device to receive a text message with the one-time code.
Alternatively, one can use authentication tokens to skip the 2FA prompt altogether. And here’s where we come to restrictions.
Tokens and Two-Factor Authentication: Restrictions
When we initially researched iCloud authentication tokens, we had no problem using them for obtaining pretty much everything from the cloud including backups. Today, Apple limits the use of authentication tokens. You can no longer use authentication tokens to access iCloud backups for accounts that use two-factor authentication. While you can still use a token to download iCloud backups from non-2FA accounts, the lifespan of these tokens is limited to just one hour since the token was created.
Regardless of two-factor authentication status, you can still use authentication tokens (without obvious time restrictions) to access the following categories of synced data:
- Many categories of synced data including Contacts, Calendars, and Notes
- Safari browsing history and open tabs
- Wallet cards
- Call logs
- iCloud Photos
- Files from iCloud Drive including many third-party app containers (1Password, WhatsApp, Viber etc.)
- Recovery token for FileVailt2-encrypted drives
- Cloud mail
Two-factor authentication is enabled:
- iCloud backups cannot be accessed with a token
Two-factor authentication is NOT enabled:
- iCloud backups can be accessed with a token, but only within 1 hour since the token was created
The following categories are INACCESSIBLE with authentication tokens:
- Passwords (iCloud Keychain)
- Health
- Screen Time
- Messages (SMS and iMessage), if Messages in iCloud are enabled *
* If Messages in iCloud are not enabled, the messages are stored in iCloud backups.
Windows vs. macOS
A much less obvious restriction of authentication tokens lies in the computer you extract it from. While Apple serves both Windows and Mac users with respective versions of iCloud software, the authentication tokens created on these platforms are different.
On Windows computers, the token is buried deep in the file system. It’s also encrypted with user credentials, so you must be able to sign in to the user’s account (or at least know their login and password) to decrypt the token. Elcomsoft Phone Breaker can do it automatically; just launch the tool, push a few buttons, and the token will saved into a text (XML) file, ready to use with EPB.
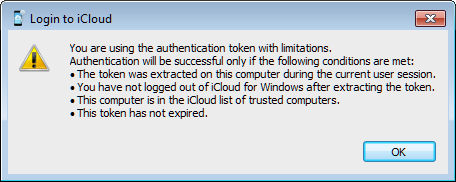
Is it that simple? Yes and no. While you can extract the token from a Windows computer, decrypt it and use with Elcomsoft Phone Breaker to access select data categories in iCloud (refer to the “Restrictions” section for details), you can do all of that only on the very same computer the token was created on. You can’t even use it from a virtual machine created of the user’s disk image; it must be the physical computer the token was created on. We refer to these tokens as limited.
If the user has a Mac, you might be able to extract a full, unrestricted token in addition to the limited one. Within its controlled ecosystem, Apple was able to implement a stronger protection (with token pinning for 2FA accounts). We were able to circumvent this protection in Elcomsoft Phone Breaker, allowing you to extract, transfer and make use of these full authentication tokens. The full token can be used on any computer, Windows or Mac; you’ll just need a recent version of Elcomsoft Phone Breaker.
Extracting and Using Authentication Tokens
There are several supported scenarios for extracting authentication tokens.
- Windows computer, extracting a limited token from the currently signed in account;
- Windows computer, extracting limited tokens from other accounts;
- macOS computer, extracting limited and unrestricted tokens from the current user (keychain password required);
- macOS computer, extracting limited and unrestricted tokens from the keychain database (keychain password required);
- iOS device, keychain obtained from password-protected backup or via physical acquisition.
Windows, current user
What you need: Elcomsoft Phone Breaker (Forensic Edition). Must be signed in as a user whose token you are about to extract.
Launch atex.exe from the command line. The tool will automatically extract the authentication token. That’s it! You have just extracted the limited, non-transferable token pinned to the current computer (saved into the text file). Note that you can only use the extracted token on the computer you have extracted it from.
Windows, other users
What you need: Elcomsoft Phone Breaker (Forensic Edition). Must be signed in as a user whose token you are about to extract.
You will be using the main GUI to extract tokens from other users’ accounts. The procedure is very complex; please refer to the User Manual for details.
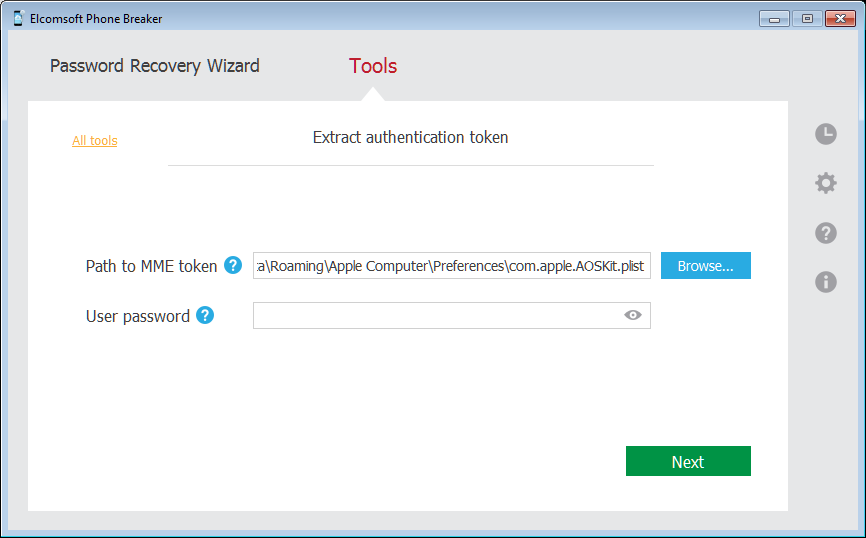
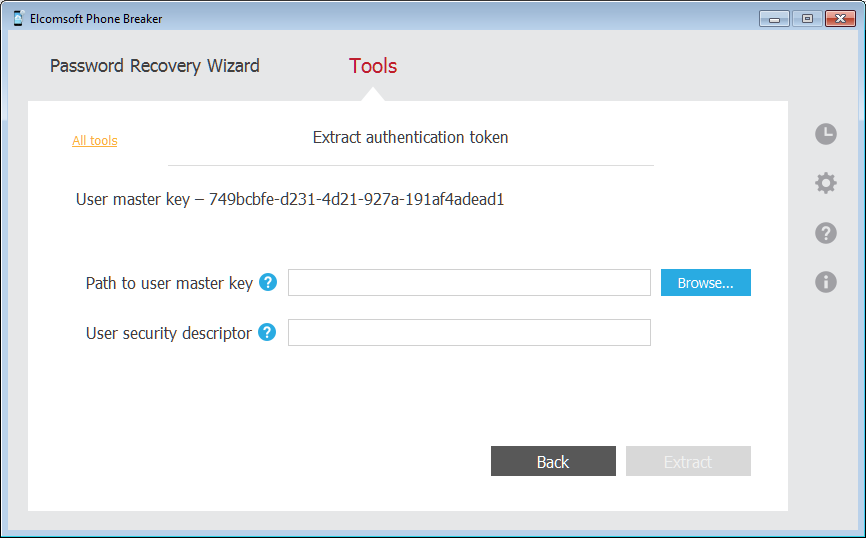
macOS, current user
What you need: Elcomsoft Phone Breaker (Forensic Edition). Must be signed in as a user whose token you are about to extract. Must know keychain password (often, but not always, the same as account password). Note: extracts both full and limited tokens.
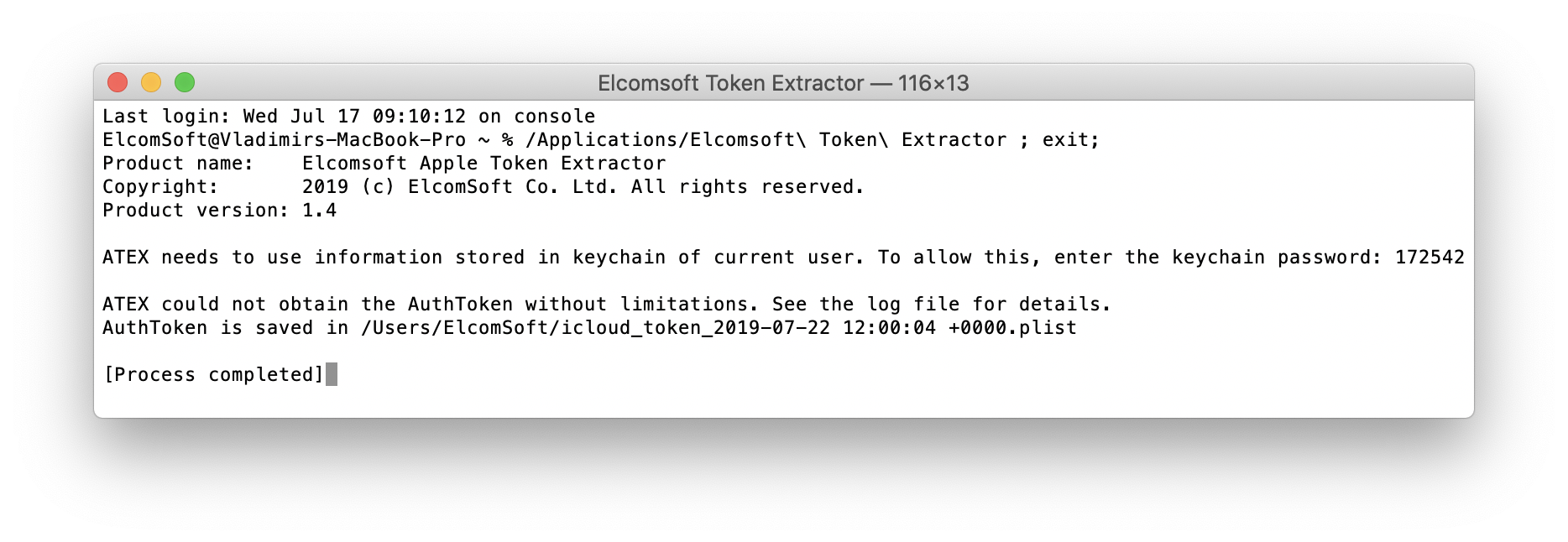
Alternatively, use macOS Keychain utility to extract token.

macOS, other users
What you need: Elcomsoft Phone Breaker (Forensic Edition). Extracted keychain database from the user you’re about to obtain the token from. Must know keychain password.

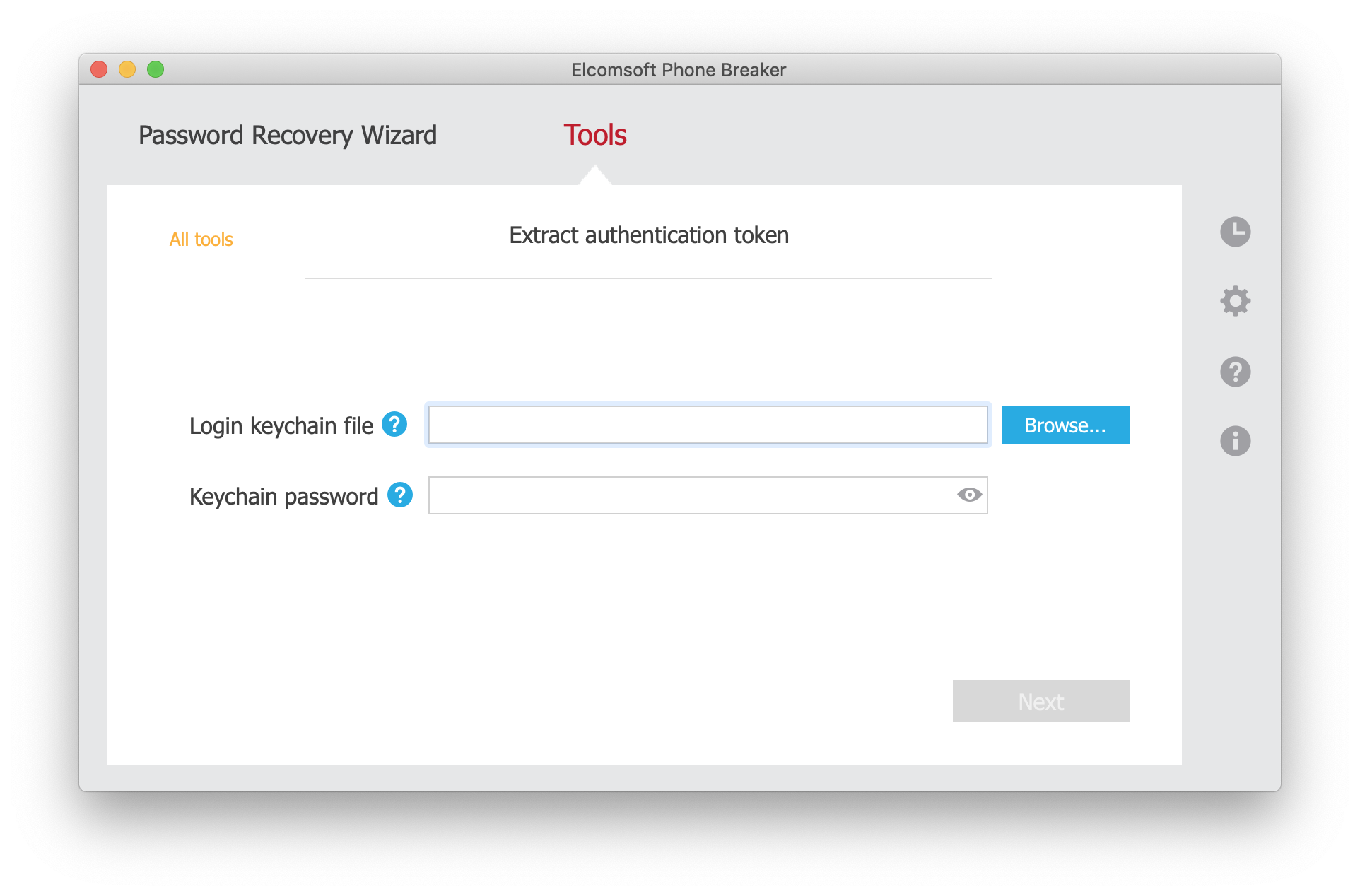
iOS device
What you need: Elcomsoft Phone Breaker (Forensic Edition). Decrypted keychain database (physical acquisition) or password-protected backup (password must be known).
Use Elcomsoft Phone Breaker to manually examine the keychain.

Using Authentication Tokens
What you need: Elcomsoft Phone Breaker (Forensic Edition).
macOS: If you extracted a full (unrestricted) token from macOS, you can copy the file and use it on any computer, Windows or Mac.
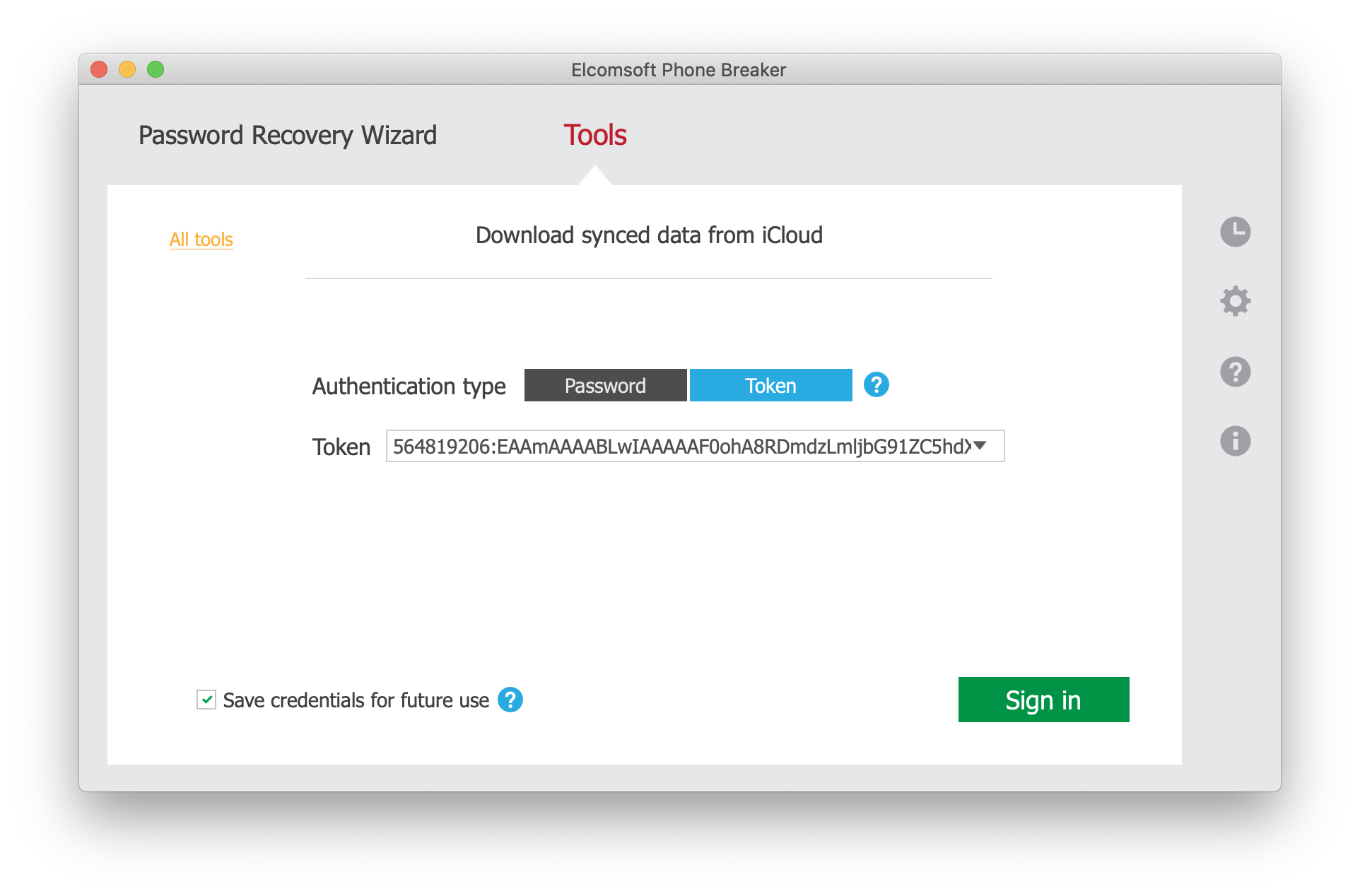
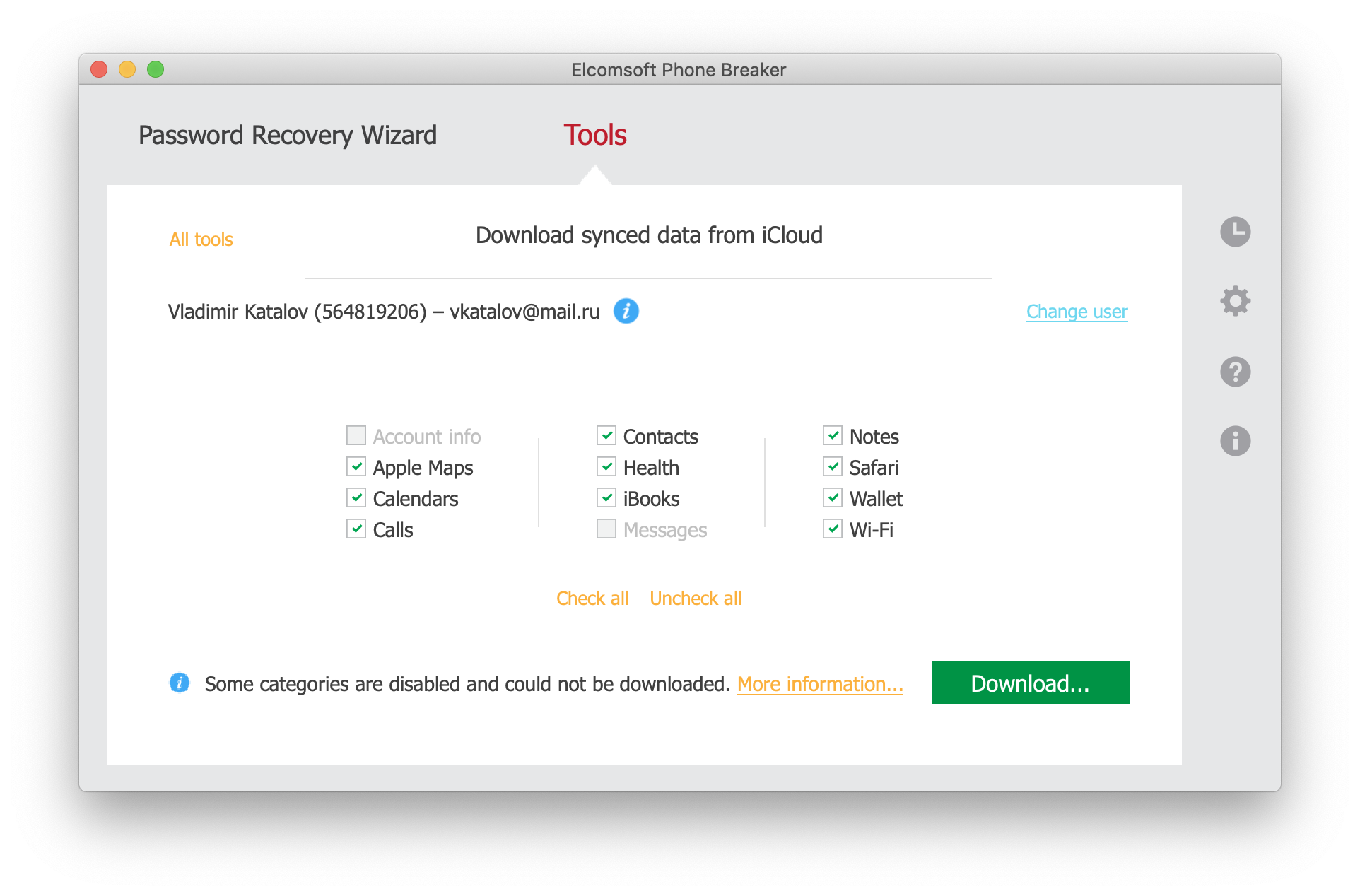
Windows: Limited tokens can only be used to authenticate from the same computer they’ve been extracted from.
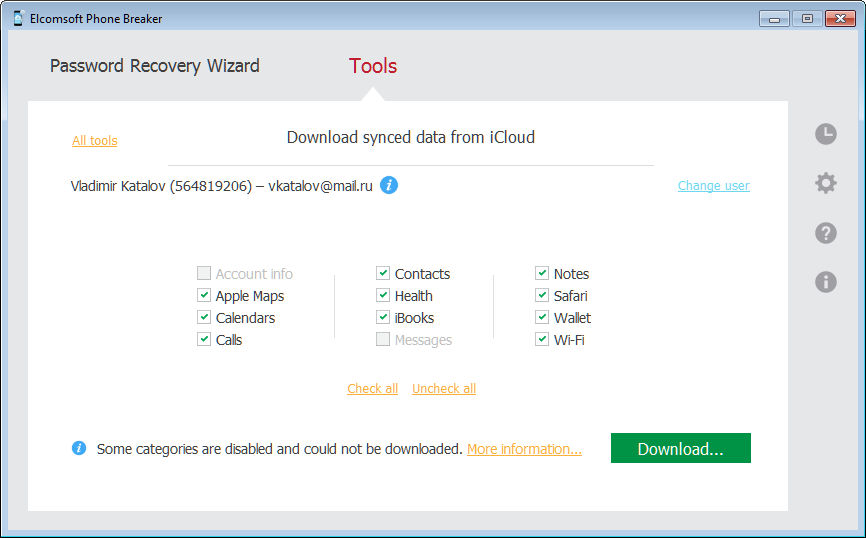
Limited tokens:
Bonus Chapter: Discovering Authentication Credentials
Since authentication tokens can be restrictive, one can have greater success extracting data from iCloud when using the login and password (and passing secondary authentication for accounts with 2FA). One can try the following methods for obtaining the user’s authentication credentials:
- Windows: use Elcomsoft Internet Password Breaker to extract stored passwords from the user’s Web browser. These can be usually found in records for “apple.com”, “icloud.com” or “appleid.apple.com”.
- macOS: use Elcomsoft Password Digger to extract and analyze the macOS keychain. Once again, the login and password can be stored in one of the records that include the words “apple” or “icloud”.
- iOS: if you are able to extract the keychain from an iOS device (via logical or physical acquisition with Elcomsoft iOS Forensic Toolkit), you can use Elcomsoft Phone Breaker to analyze the keychain. Note: the user’s Apple TV may also contain these passwords, so analyzing it may be a good idea.
Note that you would still have to pass two-factor authentication for accessing accounts protected with 2FA.
Conclusion
iCloud authentication tokens are no longer quite as a handy solution as they used to be just a year ago. Encryption and protection of the token combined with access restrictions make authentication tokens useful for accessing select types of synchronized data. The most interesting types of evidence such as iCloud backups, saved passwords, Health and Messages are not accessible with the tokens.













