How can you obtain the highest amount of data from an iPhone, iPad, Apple TV or Apple Watch? This is not as simple as it may seem. Multiple overlapping extraction methods exist, and some of them are limited to specific versions of the OS. Let’s go through them and summarize their availability and benefits.
Compatibility
We did our best to compile the compatibility information into a single table. Sorry, the iPads are missing from the table; however, the compatibility is normally dependent on the version of iOS/iPadOS (that are in sync) and the SoC model. Note: FFS stands for “full file system” (acquisition).
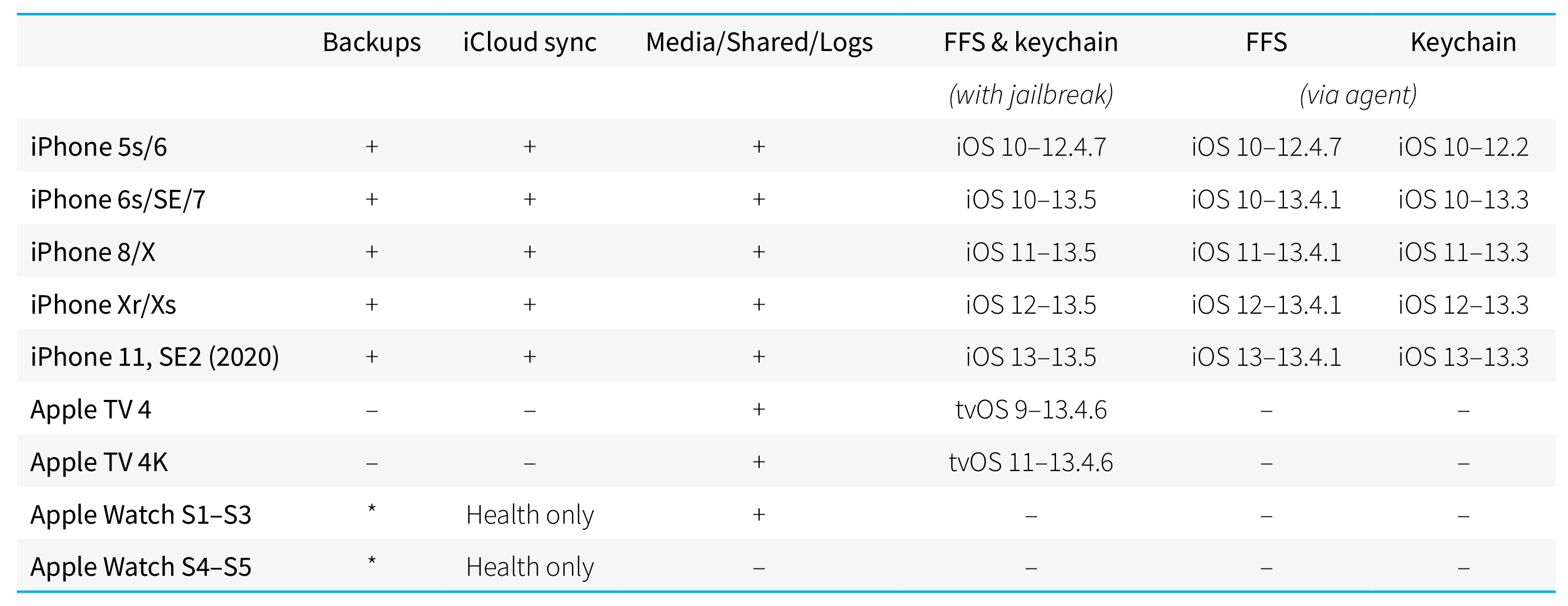
There are also some caveats.
By device type
iPhones and iPads (iOS/iPadOS)
iOS (and iPadOS) is the system we have the largest number of available acquisition methods for. All you need is just a Lightning cable, or a USB Type-C cable for the iPad Pro. For acquisition with checkra1n, however, we recommend a USB-A to Lightning cable (like this one), but not the USB-C to Lightning, as you may may get problems with it, especially when entering device into DFU mode.
Apple TV (tvOS)
For Apple TV 4, nothing extra is required as it is equipped with a USB Type-C port. For the 4K model, a special cable that connects to the hidden Lightning port is required; see Jailbreaking Apple TV 4K for details (please ignore the article subject; the same cable is required for logical acquisition, although it is theoretically possible to extract the data over Wi-Fi).
If you prefer using checkra1n over the unc0ver jailbreak (e.g. when the tvOS version is not compatible with unc0ver), please note that an adapter alone will not be enough. You will also need a special breakout cable to put the device into DFU mode.
Without jailbreaking, you can extract media files and metadata, plus some diagnostic logs.
Apple Watch (watchOS)
Here is where you will always need an adapter, see Apple TV and Apple Watch Forensics 01: Acquisition for details. IBUS is the keyword 😊. Right now adapters exist only for S1/S2/S3 watches, but not for S4 and S5. At the same time, some of the data (mostly Health) collected by Watch is synced into the iCloud (through the iPhone it is connected to). Complete Watch backups are not available, but some Watch data is also available inside iPhone backups.
By acquisition method
Logical acquisition is the fastest, simplest, safest and most compatible acquisition method, and even if it provides only the limited amount of data, it is still the very first method to try. But there are still some things to note.
- There are differences in content between local and iCloud backups.
- There are also differences between local backups with and without a password (see The Most Unusual Things about iPhone Backups); password-protected backups contain more data.
- Cloud backups are often difficult to obtain (and this is not just the 2FA issue).
Next, remember that a backup is only part of logical acquisition. You can also extract media files along with metadata even if the backup is password-protected and the password is not known. In addition, you can extract some shared files (usually documents, but sometimes other user data ranging from pictures to databases) and diagnostic logs, which may help to build the device usage timeline. This method is the only one that works on non-jailbroken Apple TV, and with Apple Watch S1 to S3 devices.
The full file system image is of course much better than a backup, even complemented with media extraction. With the file system image, you receive everything from the device, including sandboxed application data and system databases with multiple recorded location points, usage info and lots of other stuff.
The keychain is a gold mine! We are now preparing a whitepaper on the keychain. The keychain is a storage for all of the user’s passwords, encryption keys, certificates, credit card data and more. By acquiring and decrypting the keychain, you will be able to decrypt chats from the most secure messengers, access other cloud services used by the device owner, and do a lot more. If you are not extracting the keychain, you are missing a solid part of evidence.
To obtain the file system and the keychain, we recommend the Agent acquisition method (when/if compatible), as it is the safest and most reliable method. However, there is a slightly wider support of iOS versions and device models with jailbreaks.
And finally, the iCloud acquisition (honestly, our favorite). There are so many advantages of this method that they are worth another article. No need to hold the device in your hands. You can access the current and previous data sets that have been already deleted from the device. You can get some data from other devices connected to the same account, and do a lot more.
By OS version
For logical acquisition including the extraction of media files and logs, the system version does not matter at all. We can do it for all OS versions ranging from the ancient iOS 4 to the not-yet-released iOS 13.6 beta (the latest version available at the time of writing this article); the results are about the same. The first beta version of iOS 14 will be released next week, and we are almost sure we will be able to do logical acquisition for it from the get go.
We cannot say the same for jailbreak-based acquisition, as well as the acquisition performed with our agent. These methods rely on the availability of exploits. They do exist for most versions of iOS up to and including iOS 13.5, but some particular versions are not fully covered. For example, we can only extract the file system but not the keychain for iOS 12.3 through 12.4.7 for iPhone 5s and iPhone 6 devices, as well as any devices running iOS 13.3.1 through 13.4.1. Finally, while a jailbreak is available for iOS 13.5 allowing to acquire both the file system and the keychain, you have to take care of jailbreaking yourself; the agent will not help. For iOS 13.5.1 to 13.6 beta 2, you can use checkra1n (for compatible models only).
With tvOS, the situation is significantly worse. Similar exploits exist, but jailbreaks are available only for a very limited number of versions in the tvOS 9-12 range. Only tvOS 13 is fully open to checkra1n jailbreak, theoretically including the latest 13.4.8 beta, which we have not yet checked. We may develop agent-based acquisition for older tvOS versions in the future, but there is no ETA as of yet. At the same time, Apple updates tvOS automatically by default, so the user’s Apple TV will be normally running the latest version of tvOS.
As for watchOS, forget about the file system acquisition regardless of the watchOS version. watchOS is vulnerable to the checkm8 exploit. However, there were no publicly available jailbreaks for watchOS 5.2 and later (the current version being watchOS 6.2.8 beta 2). On the other side, the majority of information collected by the Apple Watch is available either from the iPhone it is paired with, or from the cloud. You can, however, extract media files and metadata (for S1-S3 series watches) if you have an IBUS adapter.
Conclusion
As we have already wrote before, there is no “one-button solution” when it comes to analyzing Apple devices, although we try to make the workflow as straightforward as possible. It is important to understand the available acquisition options for each combination of hardware and software, and make an informed decision when choosing the extraction method.
backup, checkra1n, EIFT, full file system, iCloud backup, iOS, iOS backup, iPadOS, iTunes backup, jailbreak, keychain, logical acquisition, tvOS, unc0ver, WatchOS



