The two recent jailbreaks, unc0ver and Electra, have finally enabled file system extraction for Apple devices running iOS 11.4 and 11.4.1. At this time, all versions of iOS 11 can be jailbroken regardless of hardware. Let’s talk about forensic consequences of today’s release: keychain and file system extraction.
The Jailbreaks
iOS is secure enough. Privilege escalation alone is not enough to develop a working jailbreak. Today’s jailbreaks exploit a chain of vulnerabilities to escape sandbox, obtain root privileges, remount the file system and perform several other steps to deliver a package that can be installed and used by an expert, developer or enthusiast.
Discovering vulnerabilities that can be exploited is even more difficult, requiring coordinated efforts of teams of researchers. One of such teams is called Google Project Zero. The work of this team helped jailbreaking community develop working jailbreaks for the last versions of iOS 10 and most versions of iOS 11 prior to iOS 11.4.
Thanks to Project Zero, we now have two jailbreaks for the two last versions of iOS 11: iOS 11.4 and 11.4.1.
unc0ver
Download: https://github.com/pwn20wndstuff/Undecimus/releases
Instructions: https://www.youtube.com/watch?v=TqHYjLHO0zs
Electra
Download: https://coolstar.org/electra/
Google Project Zero (Exploit with tfp0 for iOS 11.4.x to 12.1.2):
https://bugs.chromium.org/p/project-zero/issues/detail?id=1731#c10
Note: If you search for jailbreaks, the first results may lead you to one of the many Web sites distributing malware. Please make sure to download the jailbreaks directly from the two links listed above.
How can the forensic community use these jailbreaks? We use them to perform the full file system extraction.
File System Extraction
The required pre-requisite to accessing the file system is unlocking the device. If you don’t know the passcode, you’d have to break it first with a solution such as GrayKey. However, extracting the content of the device is far from trivial even if you do know the passcode or the passcode is empty.
Since early days, iOS devices were using secure encryption to protect user data against hardware attacks. iOS 8 brought additional improvements, making even Apple unable to extract information without a passcode. The release of the iPhone 5s brought yet another security measure. Secure Enclave now protects the encryption key.
For older iPhones, physical acquisition used to mean the imaging of the data partition with subsequent decryption of the data. Low-level storage access was required to perform the imaging. This low-level access could be only provided by a jailbreak (or privilege-escalation exploit based on similar principle). Starting with the iPhone 5s, the encryption key is no longer accessible even with a jailbreak. The key is protected by Secure Enclave, a hardware and software subsystem introduced with Apple’s first 64-bit SoC. For the iPhone 5s and all newer iPhones (except for the iPhone 5c), experts using physical acquisition will receive a copy of the file system (files and folders) as opposed to full memory dump.
A working jailbreak is still needed to access the file system. Until today, public jailbreaks were available for all versions of iOS 11 except the two last releases: iOS 11.4 and 11.4.1. unc0ver and Electra jailbreaks have finally broken these two versions of iOS, allowing forensic experts to gain low-level access to the content of iOS devices via physical acquisition.
Physical acquisition offers numerous benefits compared to all other acquisition options. Thanks to the low-level access to protected parts of the file system, experts can extract information stored in apps’ sandboxed data sets, gain access to system logs, temporary files, write-ahead logs and much more. With low-level access to the file system, experts can analyze comprehensive location history and detailed usage history of the device. They can read email messages and conversation histories of many instant messaging apps; those are not present in cloud or local backups (even if one manages to break or reset the password).
While we developed methods to decrypt the content of both local and iCloud Keychain, physical acquisition remains the only method for decrypting keychain items targeting the highest protection class. In other words, file system extraction gains full access to application sandboxes and all system areas.
Installing a Jailbreak
All of the latest jailbreaks are installed by sideloading the jailbreak .ipa file via Cydia Impactor from a computer or by using an online service to perform the same task on the iPhone. The online service method is easier to use, but has many security implications since nobody knows exactly what’s going to be installed on the iPhone being jailbroken.
Note: in order to obtain a certificate for sideloading the jailbreak .ipa onto the iPhone, you will need to provide a login and password to an Apple ID. While you can use your own Apple ID for that, we recommend creating a disposable Apple account without two-factor authentication.
- Back up data with iTunes or Elcomsoft iOS Forensic Toolkit (if backup password is empty, specify and record a temporary password).
- Obtain the jailbreak of your choice (unc0ver or Electra) using one of the links mentioned above.
WARNING: If you try to Google one of these jailbreaks, you may stumble upon one of the many Web sites distributing malware. We urge you to only download unc0ver and Electra jailbreaks only from trusted sources.
- Download the Cydia Impactor app (Windows, Mac, Linux)
- Cydia Impactor (developed by Saurik) is used to sign the IPA file so that the jailbreak tool can be executed on iOS devices. You will need to use valid Apple ID credentials for signing the IPA. We recommend using a newly created Apple ID for signing the certificate.
- Connect the iOS device to the computer, trust the computer on the iOS device and launch Cydia Impactor.
- Drag the jailbreak IPA onto Cydia Impactor app.
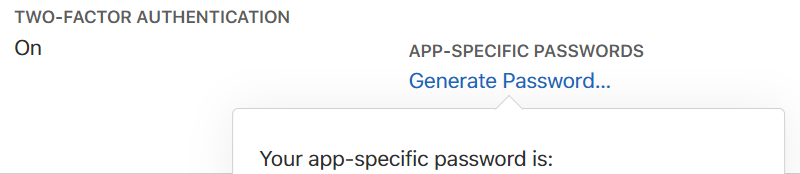
- Provide Apple ID and password when prompted. Click OK to allow Cydia Impactor to sign the IPA and upload it onto the iOS device. (A disposable Apple account without 2FA is recommended; there is no need to use the same Apple ID as the main ID on the device). If you are using a non-throwaway account and if that account has Two-Factor Authentication, you will need to create an app-specific password at https://appleid.apple.com/account/manage
- Cydia Impactor will sideload the IPA file onto the iOS device.
- If you attempt to launch the jailbreak IPA at this time, the attempt fill fail as the digital certificate for that app is not yet trusted.
- You will need to trust the certificate in order to be able to launch the jailbreak. To do that, on the iOS device, open Settings > General > Device Management. You will see a developer profile under the “Apple ID” heading; tap the profile to establish trust for this developer. Note: This requires a working Internet connection on the device, which may pose a risk. You can avoid this risk by using a developer certificate (an Apple ID registered as a developer account), in which case this step is not required.
- On the iOS device, find the jailbreak app and run it. Follow the on-screen instructions. If you use unc0ver, you will see the following output:
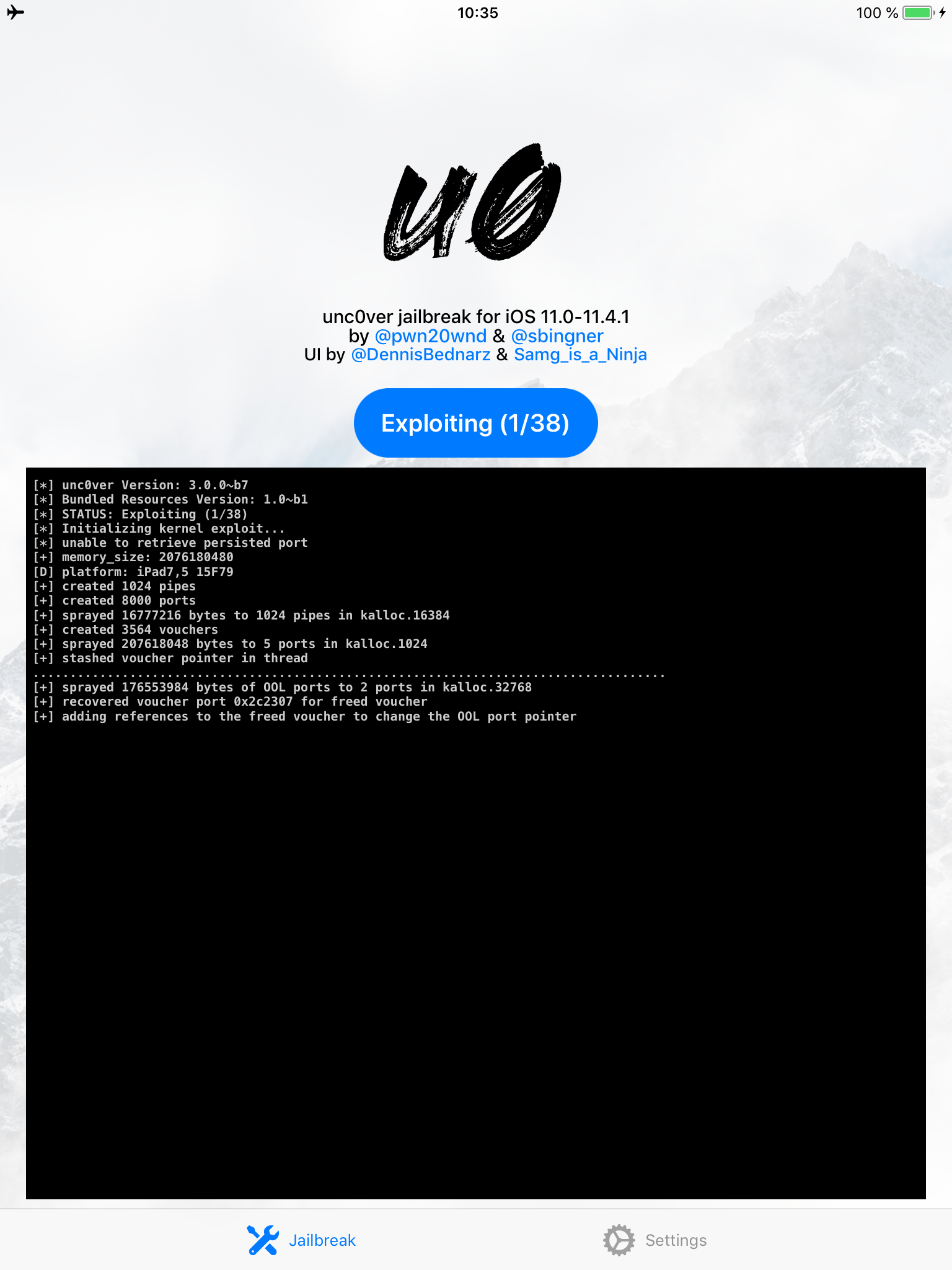
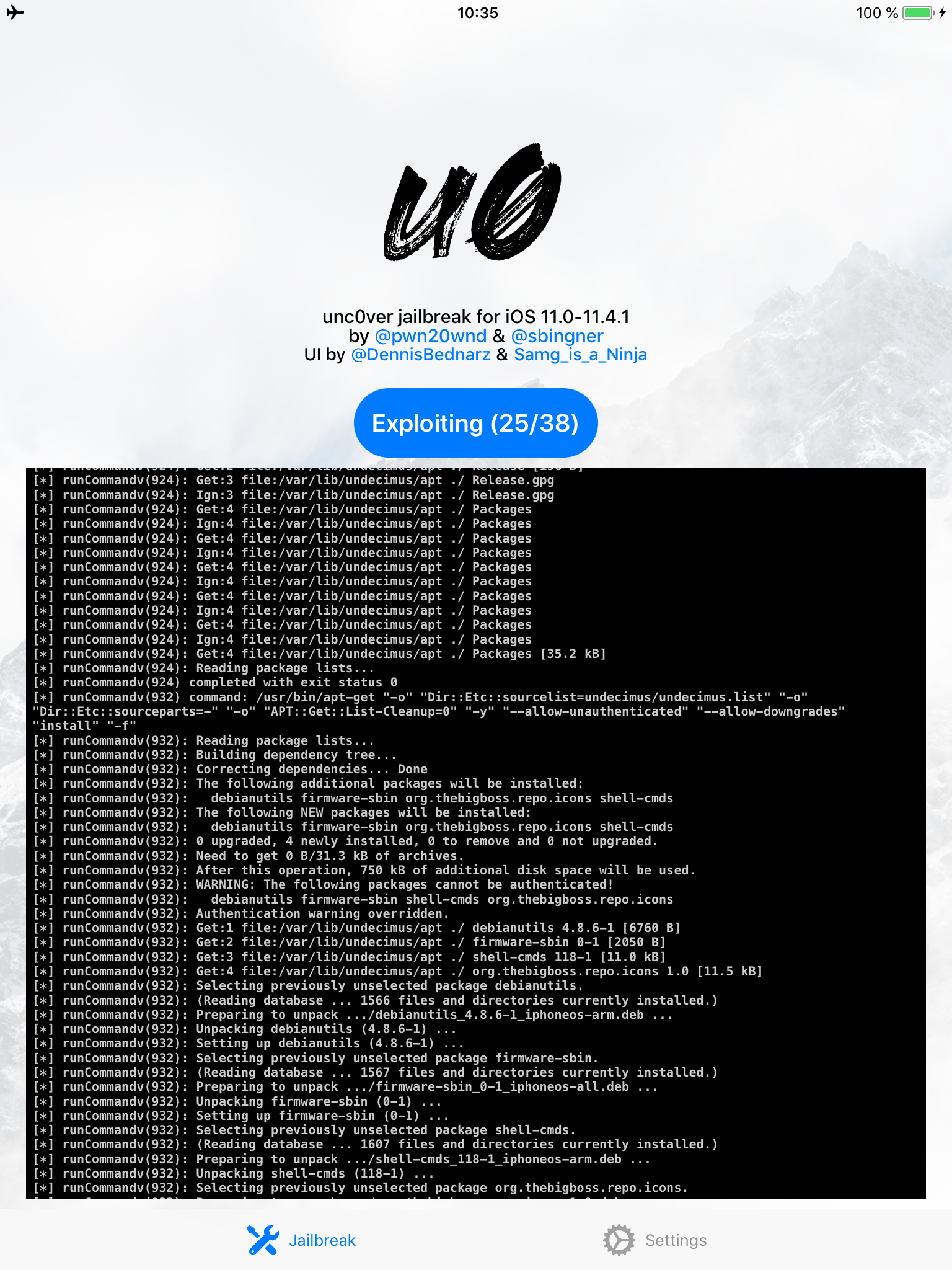
- After you jailbreak, the device will respring. Note: if you see an error such as the one shown below, please refer to the pre-requisites and troubleshooting section above.
- Elcomsoft iOS Forensic Toolkit requires a working SSH connection to image the file system. If you decided to use unc0ver, you will need to install OpenSSH from Cydia. Electra already bundles an SSH daemon listening at port 22.
Note: the unc0ver jailbreak does not come with a bundled SSH daemon. Since iOS Forensic Toolkit requires an SSH connection, we recommend installing OpenSSH from Cydia. The previous version of Electra did bundle an SSH daemon, and OpenSSH installation was not required. We did not test the current version of Electra.
Using accounts with two-factor authentication requires generating an app-specific password:
Signing the Jailbreak: Disposable Apple ID vs. Developer Certificate
As already mentioned, in order to sideload an IPA file and run it on the iOS device, you will need to sign the IPA file. While we generally recommend using a disposable Apple ID account to obtain a digital signature, doing so carries a certain risk. Signing the IPA file requires a working Internet connection on the computer. In order to run the newly signed IPA file, you may be required to “trust” the certificate on the iOS device you’re attempting to jailbreak. Establishing trust requires a working Internet connection, this time on the iOS device itself. This in turn has the associated risk of allowing the device connect to Apple’s Find My iPhone service, making it potentially vulnerable to remote lock/remote erase commands.
You may avoid this risk entirely by using an Apple ID account enrolled in Apple’s developer program to sign the jailbreak IPA. If you sign the jailbreak file with a developer Apple ID, you won’t have to “trust” the certificate on the device, and you won’t need a working Internet connection.
A jailbreak signed with a developer certificate can be used for 1 year. IPA files signed with a disposable Apple ID can be launched during the 7-day period, after which you’ll have to repeat the entire process (starting with sideloading).
Unc0ver or Electra?
There are two different jailbreaks available for iOS 11.4 to 11.4.1. We only had one device running an eligible version of iOS, so we were only able to test one of the two jailbreaks. For our purpose, the unc0ver jailbeak required several attempts with multiple reboots. That said, while we didn’t test Electra, we expect it to work in a similar fashion. We studied the previous version of Electra in Using iOS 11.2-11.3.1 Electra Jailbreak for iPhone Physical Acquisition.
Extracting the File System
Once the jailbreak is installed, extracting the file system is relatively easy.
- Required: Disable Wi-Fi on the iPhone being acquired. Better yet, put the device in Airplane mode.
- Required: Disable Wi-Fi on the computer you are running iOS Forensic Toolkit on. This is required in order to ensure that no other iOS devices are connected to the same network as the one being extracted.
- Run Elcomsoft iOS Forensic Toolkit.
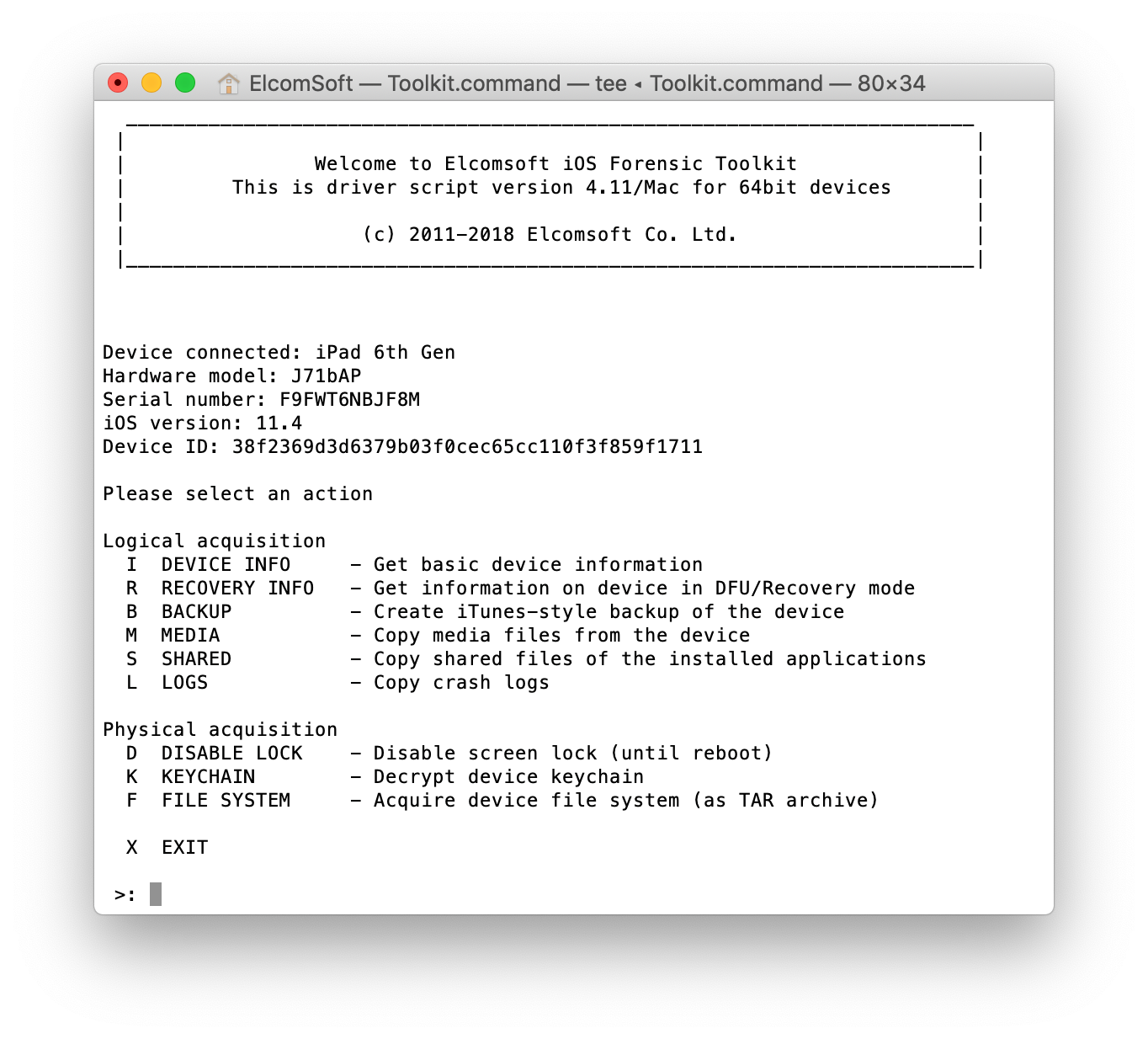
- From the main window, select “D” to disable screen lock. This is required if you want to extract keychain items. If the screen locks at any time during keychain extraction, some records will remain encrypted; and if that happens when file system is being acquired, then some files will not be copied.
- From the main window, select “K” to extract the keychain. Since the keychain is significantly smaller compared to the rest of the data, it will be extracted almost instantly. The ability to extract and decrypt the keychain from 64-bit iOS devices is a unique feature of Elcomsoft iOS Forensic Toolkit; the only other tool that can decrypt the keychain is GrayKey. The keychain contains user’s stored passwords as well as a number of tokens that can be used to sign in to various Web sites and social networks without the login and password.

Note: You will be prompted for superuser password (twice). The default password is alpine.
- Now you can extract the file system by using the “F” command. Depending on the size of the iPhone being extracted, the process may take a while.
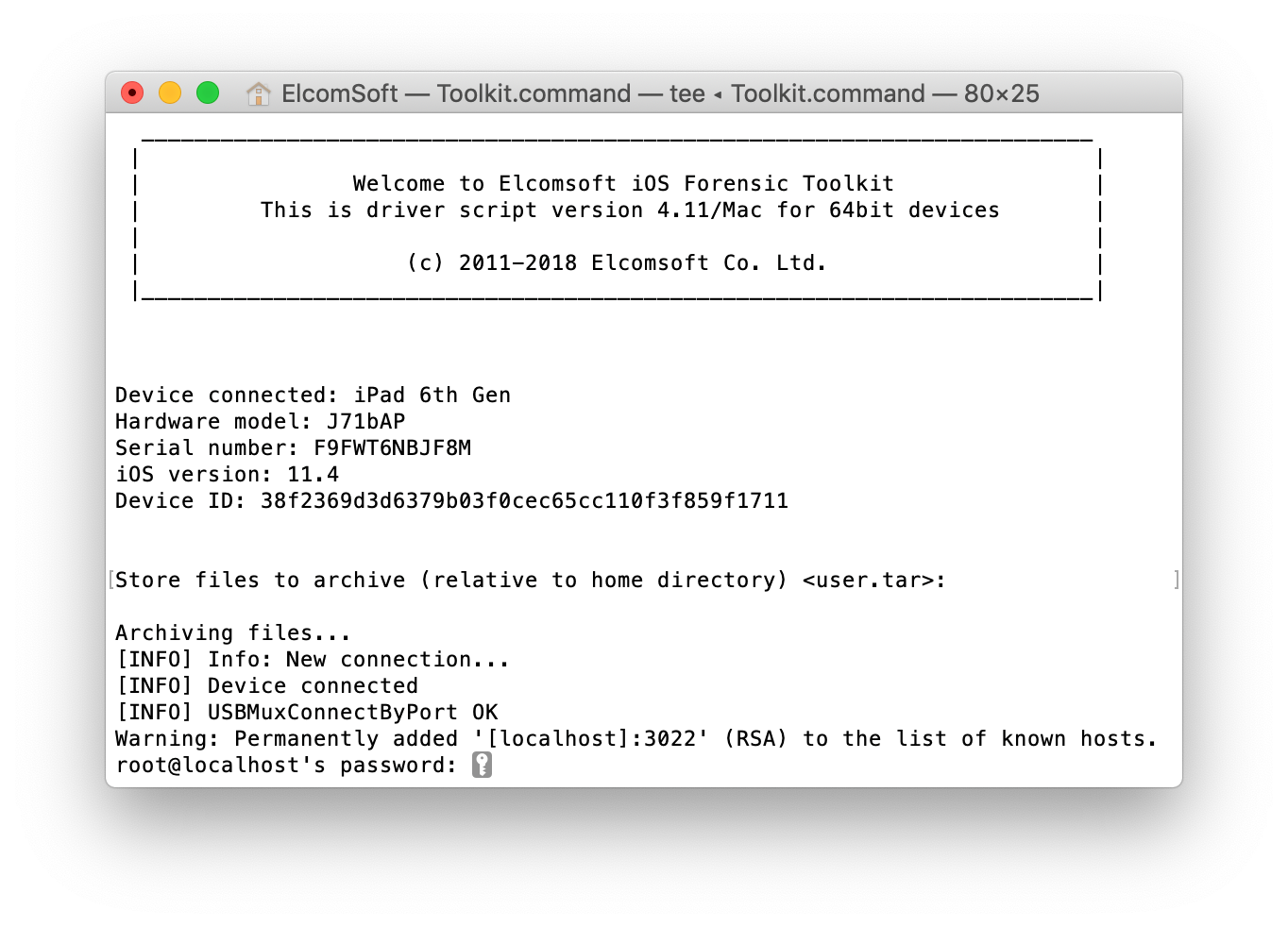
Exploring the File System Image
The acquisition process extracts the complete image of the device file system in UNIX format. Some characters allowed in UNIX paths and file names are forbidden in Windows. For this reason, we chose to make use of the TAR format to save the content of the file system as opposed to ZIP. In order to analyze the data, you may either unpack or mount the TAR archive. However, we built a tool for analyzing such TAR files.
Elcomsoft Phone Viewer can open iOS TAR files produced by Elcomsoft iOS Forensic Toolkit. In addition, the tool can open ZIP archives of the file system produced by GrayKey. With it, you will get comprehensive location data, history of Apple Pay transactions, notifications and more.
Jailbreak Alternatives
There are alternatives to physical extraction via jailbreak. First, there’s GrayKey, a forensic solution made by GrayShift. GrayKey is exclusively available to select law enforcement and government agencies in select regions. GrayKey uses the same or similar exploits to those that are used in jailbreaks. For obvious reasons, the company does not disclose technical details of their solutions. Unfortunately, GrayShift does not disclose device compatibility matrix either.
If you have access to Cellebrite services, they are a real alternative to jailbreak extraction and GrayKey. This company (based in Israel) is even more secretive than GrayShift, so we can’t really comment on what combinations of hardware and software they support.
Conclusion
Thanks to Google Project Zero, we finally have working jailbreaks for the last two versions of iOS 11. Researchers have already discovered vulnerabilities in iOS 12.0 through 12.1.2 (the latest version of iOS is 12.1.3 at the time of this writing, but downgrading to iOS 12.1.2 and even 12.1.1 is still possible right now). These vulnerabilities have already resulted in successful privilege escalation exploits, yet we’re still far from a working jailbreak. However, it is theoretically possible to gain full access to iOS 12 file system even without a jailbreak but using these exploits directly. Stay tuned for an update!












