Using and Troubleshooting the checkm8 Exploit
October 31st, 2023 by Oleg Afonin
Category: «General»
The bootloader vulnerability affecting several generations of Apple devices opens the door to forensically sound extraction. In today’s article we’ll discuss the compatibility and features of this exploit with different devices, iOS versions, and platforms. In addition, we’ll provide security professionals and researchers with valuable insight into potential issues and solutions when working with checkm8.
Understanding Bootloader Vulnerabilities
Bootloader vulnerabilities exist in several generations of Apple devices. checkm8, the most famous bootloader exploit, is available for chips that range from the Apple A5 found in the iPhone 4s and several iPad models to A11 Bionic empowering the iPhone 8, 8 Plus, and iPhone X; older devices such as the iPhone 4 have other bootloader vulnerabilities that can be exploited to similar effect. checkm8 plays a significant role in iOS forensics, enabling forensically sound extraction for a wide range of Apple hardware including several generations of iPhones, iPads, Apple Watch, Apple TV, and even HomePod devices.
In mobile forensics, checkm8 allows for low-level access to the device’s file system, making it a valuable tool for security professionals and researchers. While the exploit itself does not alter any data on the device’s system or user partitions, its various implementations including the checkmra1n jailbreak that are not as forensically sound as the underlying exploit. Here at ElcomSoft we developed a checkm8-based extraction process that is both repeatable and verifiable.
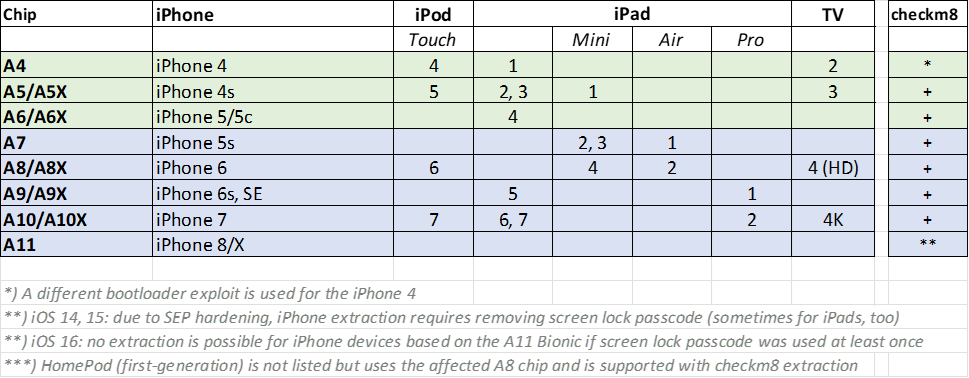
checkm8 Compatibility
The checkm8 exploit is available for a wide range of hardware platforms. Being a bootloader-level exploit, checkm8 was initially believed to be fully OS-agnostic. While the exploit itself can indeed be applied to a vulnerable device regardless of the OS version, newer versions of iOS largely mitigate its forensic effect, blocking access to the file system on certain combinations of hardware and software. In particular, iPhone 8, 8 Plus, and iPhone X devices running iOS 16 utilize SEP hardening measures that make it impossible to access the file system even after successfully applying the exploit if the device had a passcode enabled at any time after setup. The same devices running iOS 14 and 15 require passcode removal prior to extraction; the same measures may be required when extracting iPads based on the same chip.
checkm8 compatibility matrix (green cells indicate 32-bit devices, blue cells indicate 64-bit devices):
Using checkm8 for Data Extraction
The pure checkm8 exploit alone is not enough to extract the file system. We built a comprehensive solution based on the checkm8 exploit allowing to extract a copy of the file system from affected devices in a safe, forensically sound manner. For this to work, you’ll need a copy of Elcomsoft iOS Forensic Toolkit 8 and a macOS computer (Intel or Apple Silicon). Please note that the Windows edition of iOS Forensic Toolkit does not support checkm8, while the upcoming Linux version will include support for checkm8 extraction.
The complete step-by-step instructions for checkm8 extraction are available in the following articles:
Using checkm8 requires placing the device into DFU. We wrote several articles on the subject:
checkm8 Troubleshooting
Using checkm8 for device extractions may present challenges without obvious solutions. In this chapter, we will talk about the problems and solutions.
After checkm8 extraction, device always reboots into Recovery
This is expected behavior caused by the autoboot flag set by iOS Forensic Toolkit during the initial stage of applying the exploit. When the device boots into iOS, it alters the data on the user partition, causing checksum mismatch on repeat extractions. The iOS boot sequence may start, for example, if one makes a timing mistake when placing the device into DFU. For this reason, iOS Forensic Toolkit automatically alters the boot behavior of iOS devices by flipping the autoboot flag, making the device boot into Recovery instead of iOS. When you have finished processing the device and are ready to return it, connect the device to the computer with iOS Forensic Toolkit installed and execute the following command (the device must be in Recovery):
./EIFT_cmd tools autobootTrue
After this command, the device will automatically reboot into iOS.
Q: Does flipping the autoboot flag break forensically sound extractions?
A: No. The flag is stored in the device’s NVRAM and not on the data or system partition, so flipping the flag will not alter the checksum.
Detailed explanation: Forensically Sound checkm8 Extraction: Repeatable, Verifiable and Safe.
Important: iOS Forensic Toolkit automatically flips the autoboot flag only after successfully applying the checkm8 exploit, which happens in DFU mode. To prevent the device accidentally rebooting into iOS while you attempt to place it in DFU, we strongly recommend placing the device into Recovery first, then manually flipping the flag as follows:
./EIFT_cmd tools autobootFalse
Error attempting checkm8 extraction on a 32-bit device
When: unlockdata fails on a 32-bit device.
Cause: This is expected behavior.
Solution: For 32-bit devices without Secure Enclave we developed a unique process known as “perfect acquisition”, which, instead of a copy of the file system, makes and decrypts an image of the data partition. This in turn requires a different command sequence compared to the standard checkm8 extraction process.
Detailed explanation and extraction steps: Perfect Acquisition Part 4: The Practical Part
Screen lock passcode reset: when and why
Sometimes you may receive an error early during the boot stage. The error may look as follows (the values for code, line, and commit may vary):
[ERROR] EIFT: failed with exception:
[exception]:
what=Failed to open connection to device
code=11993119
line=183
file=../../../ra1nsn0w/iOSDevice.cpp
commit count=191
commit sha =1d674084639c73f1397535ee8aec50b35f1760d6
If this happens, it may mean that you need to remove the screen lock passcode from the device, then repeat the extraction. This is caused by SEP hardening measures developed by Apple in an attempt to mitigate the checkm8 exploit.
When: The device is an A11 Bionic device running iOS 14 or 15 (always required), or a 64-bit device running iOS 16 (only if error occurs).
Solution: Boot the device into iOS; unlock with passcode (passcode must be known); open Settings; on devices with Face ID: Tap Face ID & Passcode; on devices with a Home button: Tap Touch ID & Passcode; then tap Turn Passcode Off.
Troubleshooting: Mind the autoboot flag (see above), which must be manually set to ‘true’ if previously attempted checkm8 extraction.
Forensic consequences: Passcode reset causes loss of certain types of data (e.g. downloaded Exchange mail, Apple Pay transactions and more) and removes the trusted device status (if accessing Apple ID/iCloud from that device afterwards).
Cannot place device into DFU
There can be several issues preventing the device DFU mode.
Insufficient charge. This is a common cause for devices with depleted batteries. The issue with this situation is that if you start charging, the device will automatically boot into iOS when the battery reaches a certain level. The only way to prevent this behavior is placing the device into Recovery first, which can be done at any charge level.
Broken or rattling physical buttons. DFU requires following a sequence of button presses with precise timings. If a button is faulty or ‘rattles’, this conditions cannot be satisfied. Solution: use DFU for Devices with Broken Buttons instead (warning: requires disassembly). For A11 devices (iPhone 8/8 Plus/X), you may use a Raspberry Pi Pico instead, which does not require disassembly: Automating DFU Mode with Raspberry Pi Pico.
Incorrect timings, human mistake. We strongly recommend practicing DFU mode beforehand with a known good device of the same model.
General considerations
DFU mode requires some skill. If you have trouble entering DFU mode or exploiting the vulnerability, first try again. Then try changing the cable (preferably use the original Apple part) and/or connecting the device to a different USB port. Do not use USB-C to Lightning cables; if needed, use a USB-C hub or adapter with a regular USB-A to Lightning cable. If this does not help, use another computer (if available). Finally, try entering DFU mode using a different method.
Unmatching or undefined version of firmware
When: More then one link or no link to Apple firmware are displayed, or the device reboots or fails to unlock the data partition when using the firmware image or link.
Cause: Our implementation of checkm8 requires a copy of Apple original firmware, which will be patched on-the-fly and uploaded into the device’s volatile memory. For this to work, the patched firmware version must match the version of the firmware already installed on the device. In many cases, iOS Forensic Toolkit is able to correctly identify the firmware installed on the device, and displays a single download link (you can either download the entire image or pass the link as an argument to EIFT, in which case only the required parts of the image will be downloaded).
However, the detection works based on the iBoot version. There are multiple iOS releases utilizing the same iBoot, which results in several potential matches and multiple firmware download links. While using a slightly different firmware may work, sometimes the device may either reboot (make sure the autoboot flag is set to avoid booting into iOS) or fail to unlock the data partition.
Solution: If this happens, you will have to either:
- Identify the correct version of the OS installed on the device by using Diagnostic mode (which is safer and more forensically sound than booting iOS for the same purpose), or
- Try all firmware links listed by iOS Forensic Toolkit starting from the newest build. This is safe; worst case scenario is device reboot (once again, make sure the autoboot flag is set to avoid booting into iOS).
Sometimes the correct version cannot be determined (e.g. for firmware builds newer than iOS Forensic Toolkit). In this case, you will have to manually locate the download link at ipsw.me.
If the device is running a beta version of iOS, please contact our customer support. Links to beta firmware images are generally not published by Apple.
For Apple TV (often), Apple Watch (always), HomePod (always) and, on rare occasions, even for iPhone/iPad devices there may be no full .ipsw images available. A zipped OTA update may be available instead. OTA firmware links or downloaded .zip files are supported by iOS Forensic Toolkit; there is no need to unpack or rename such files.
‘Snapshot’ warning appears in the output
When: In certain cases, you may see the following output:
Mounts:
[RW] (hfs) /dev/md0 -> /
[RW] (devfs) devfs -> /dev
APFS Volumes:
/dev/disk0s1s1 (Whitetail14A403.D10D101OS) [NONE]
Snapshot: com.apple.os.update-151D1F6F36C3D125B3424A627391C16BCF5FCDA55D4BAE35
C3BE3D65720F574C23EE3363F263A1A37DBF741A65C4CC73
Snapshot: com.apple.os.update-MSUPrepareUpdate
/dev/disk0s1s2 (Data) [NONE]
/dev/disk0s1s3 (Baseband Data) [NONE]
Cause: When you see the “Snapshot” warning in the output log, it usually means your device is in one of two states:
- Update downloaded, not installed: Your device has downloaded a software update, but it hasn’t been installed yet.
- Modified system partition: The device’s system partition has been tampered with; it may have a jailbreak, malware, or spyware.
Solution 1: If the device has a downloaded update, you can manually delete it from the device Settings app.
Steps:
- Open your device’s settings by launching the “Settings” app.
- Select “General.”
- Tap on “iPhone Storage.”
- In the list of apps, find “iOS update” and tap on it.
- Choose “Delete Update” and confirm.
If you can’t find any updates and still see “Snapshot,” contact our customer team.
There is a way to deal with the “Snapshot” warning without deleting the update, but it is somewhat risky. If required, reach out to our support team for assistance.
Important: Be cautious when allowing the device boot into iOS, as it can lead to potential risks.
Solution 2: If the device has a modified system partition, please contact our support team.
Corrupted file system, APFS ‘copy-on-write’ issues
When: Some files have abnormally large sizes.
Cause: File system corruption or the consequences of APFS “copy-on-write” scheme may result in abnormally large file sizes for some files. When using EIFT extraction agent, the issue is detected and fixed automatically. However, this approach is not applicable for checkm8 extractions.
Solution: There is currently no universal solution.
Workaround: If you encounter this issue, you might need to access your device via SSH (iOS Forensic Toolkit does support SSH) or performing selective extraction, manually downloading unaffected files or manually deleting corrupted ones. However, before doing so, we strongly recommend contacting our technical support for assistance.
Future work: We are currently working on a unified extraction agent that will handle file system extractions. This aims to standardize the handling of file system issues while bringing partial data extraction and metadata extraction tools to checkm8 extractions.
Conclusion
This troubleshooting guide provides steps by step instructions to address the various issues occurring during checkm8 extractions. Whether you’re dealing with pending updates or file system issues, our aim is to assist you in resolving these issues effectively and efficiently. If you encounter any issues not covered in this guide, please feel free to contact our customer support team for expert assistance.



