BitLocker is Windows default solution for encrypting disk volumes. A large number of organizations protect startup disks with BitLocker encryption. While adding the necessary layer of security, BitLocker also has the potential of locking administrative access to the encrypted volumes if the original Windows logon password is lost. We are offering a straightforward solution for reinstating access to BitLocker-protected Windows systems with the help of a bootable USB drive.
BitLocker Protectors
This isn’t the first article we publish about BitLocker. If you are not familiar with BitLocker encryption, you may find the Introduction to BitLocker: Protecting Your System Disk handy. That article describes the basics of BitLocker as viewed by the computer user. The follow-up article Unlocking BitLocker: Can You Break That Password? reveals much of the detailed under-the-hood operation of BitLocker; we recommend reading that article even if you know about BitLocker.
BitLocker volumes may be protected with one or several protectors of various types that can be used together (for tougher security) or in parallel (for easier recovery). Multiple combinations of such protectors are available. By default, Windows requires the minimum of two protectors when the user creates an encrypted volume. The volumes are commonly using TPM (the first protector), while the backup Recovery Key (a 48-character numeric password) is created and stored in the AD, the user’s Microsoft Account, or on the hard disk or removable USB drive.
What’s essentially wrong with this approach is that Microsoft offers no straightforward path to reinstate access to the user’s Windows account located on a BitLocker-encrypted system volume even if the backup protector (e.g. the recovery key) is available. Granted, one can still boot from a Windows recovery disk and mount the encrypted volume by supplying the recovery key. However, subsequent steps require either reinstalling Windows or backing up the data off the encrypted volume.
We are offering an easier way. Starting with version 7.05, Elcomsoft System Recovery can be used to unlock BitLocker volumes when you boot from the ESR USB drive. By booting from a USB drive, you can now do the following:
- Unlock all BitLocker volumes to which you have one of the supported protectors (see below), including the system (boot) volume.
- Access the user’s Windows account. For example, you can reset the user’s Windows account password, assign administrative privileges to a certain user, extract stored passwords and do a lot more as detailed in the How to Unlock Windows Systems with a Bootable Flash Drive
Supported BitLocker Protector Types
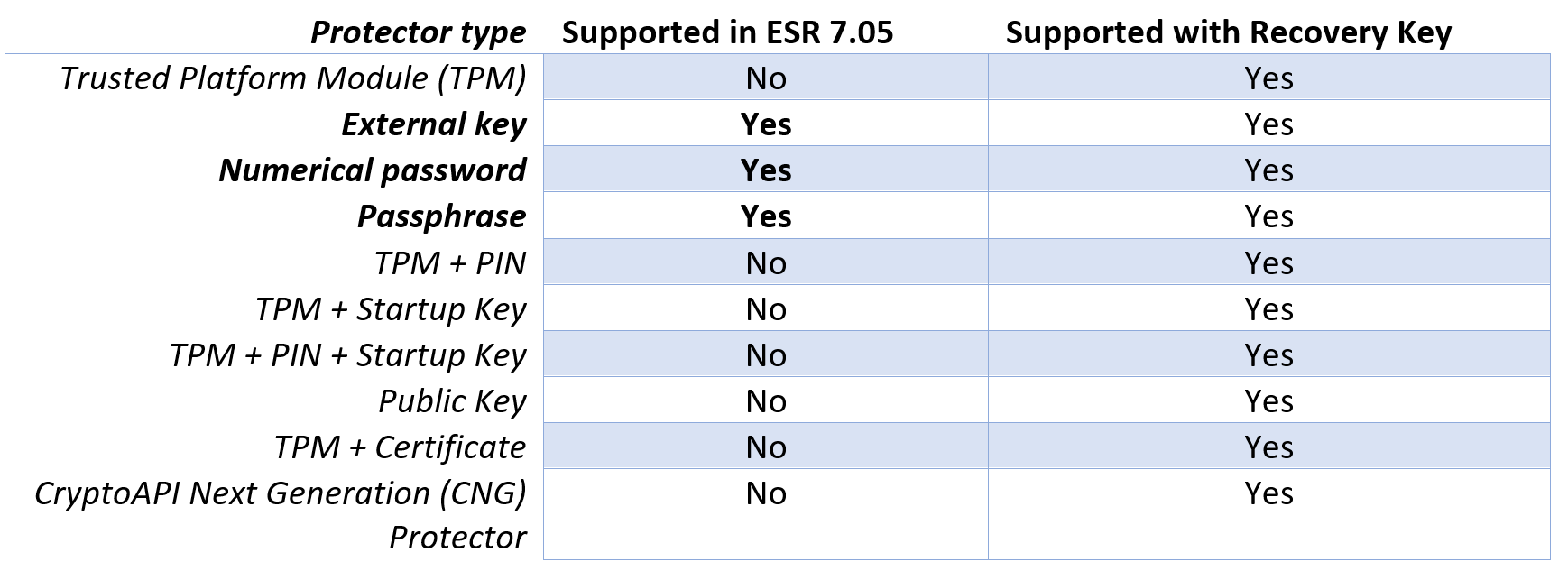
Not all protectors are created equal. When it comes to recovery access to a locked-out computer, things suddenly become more complicated than you might have imagined after reading the Unlocking BitLocker: Can You Break That Password? article.
BitLocker offers a range of protection options, mixing the TPM, all-digit PIN codes, recovery keys, passwords (user passphrases) and USB keys. While multiple protectors are commonly used for access recovery purposes, the most security conscious may specify the use of several protectors, all of which must be used together to unlock the encrypted volumes. Let’s see how the choice of BitLocker protectors affect the possibility to successfully unlock the volume.
- TPM only. This is by far the most commonly used protector in corporate environments. The volume master key (VMK) is stored in the secure Trusted Platform Module (TPM), and is only released on verified boot. If the TPM is all that you have (that is, no Recovery Key is available in the AD, the user’s Microsoft Account or as a file/printout), unlocking a volume by booting from a USB drive will not be possible. The volume can be only unlocked with ESR if you have access to the volume’s Recovery Key.
- Password. This is the most commonly used protection scheme for non-system volumes and external drives. Obviously, if you have the password, ESR will be able to mount the volume. When creating password-protected BitLocker volumes, Windows will automatically produce the Recovery Key. If you have that Recovery Key, ESR will be also able to mount the volume.
- USB Key. If the computer is not equipped with a TPM module, an edit to Windows Group Policies can enable BitLocker protection on boot volume with a so-called Startup Key. In this case, BitLocker uses input from of a USB memory device that contains the external key.
- TPM+PIN, TPM+USB, TPM+PIN+USB. These combinations require the presence of all enabled protectors at the same time in order to unlock the volume. You can still mount the volume if you have the correct Recovery Key.
The following table summarizes the experience.
How to mount the BitLocker volume with Elcomsoft System Recovery
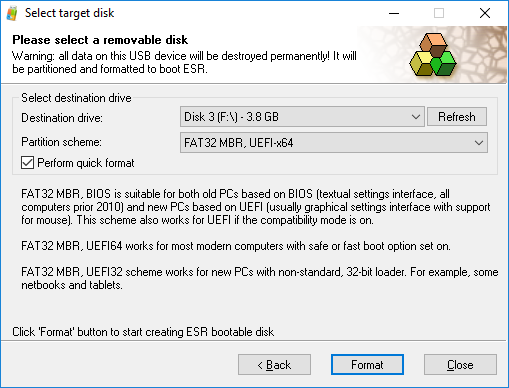
In order to use Elcomsoft System Recovery, you will first need to create a bootable media (e.g. USB flash drive) with ESR 7.05 or newer. To create a bootable flash drive, just launch the tool on your computer (not the suspect’s computer) and follow the wizard.
Boot the target computer from the USB drive you have created. Once the computer finishes booting, Elcomsoft System Recovery will be launched. The tool will automatically scan the available hard drives for encrypted volumes. If ESR detects at least one BitLocker volume, the tool will prompt to unlock the drive:
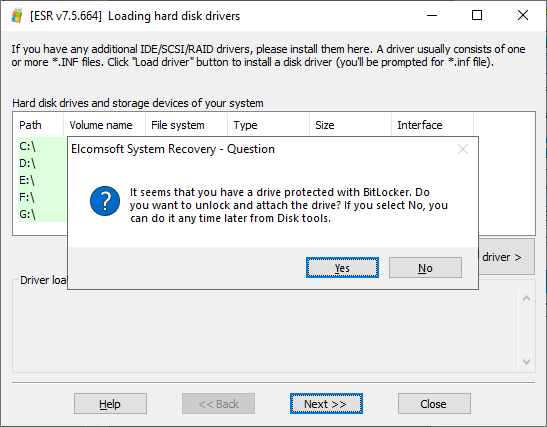
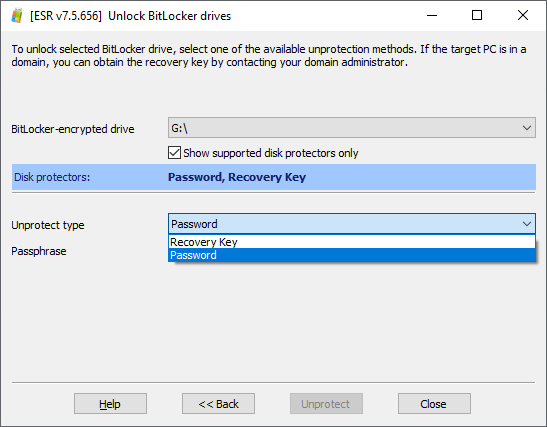
Select “Yes” Next to continue. In the next window, ESR will display the drive letter and the type of protector. Note: if the tool detects that a BitLocker drive has least one unsupported protector (see previous chapter), the unsupported protectors will not appear in the list of disk protectors by default. To display all protectors including the unsupported types clear the “Show supported disk protectors only” check box.
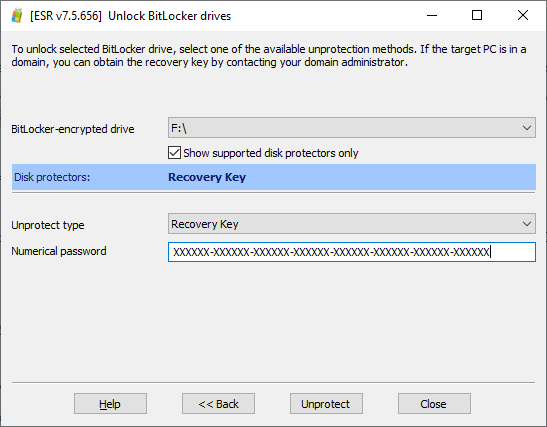
Once the check box is cleared, you will see the unsupported types of disk protectors. In the example below, the startup drive was protected with TPM+PIN with the Recovery Key as a backup protector.
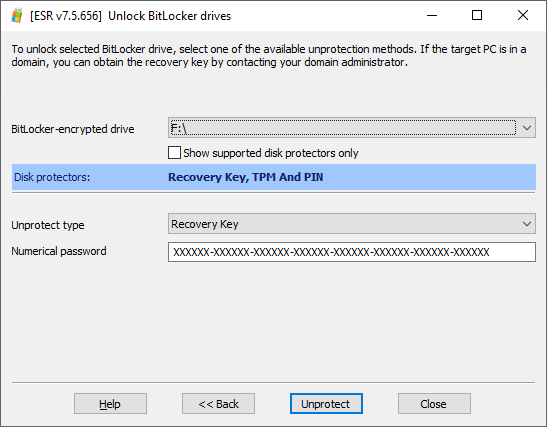
To unlock the drive, enter the Recovery Key (the 48 digits) in the “Numerical password” field, then click Unprotect. If the Recovery Key matches the encrypted partition, the volume will be successfully unlocked.
In some situations, you will encounter BitLocker volumes protected with several disk protectors of the supported type. In the example below, the volume was protected with a password, with the Recovery Key created as an additional (backup) protector. This is the default for non-boot volumes such as additional drives and partitions as well as external devices protected with BitLocker To Go. If this is the case, specify the type of protector you have access to. For example, if you know the password to the BitLocker volume, select “Password” as the “Unprotect type” and type in the corresponding passphrase to unlock the volume.