BitLocker is one of the most advanced and most commonly used volume encryption solutions. BitLocker is well-studied and extensively documented solution with few known vulnerabilities and a limited number of possible vectors of attack. BitLocker volumes may be protected with one or more protectors such as the hardware-bound TPM, user-selectable password, USB key, or combination thereof. Attacking the password is only possible in one of these cases, while other protectors require a very different set of attacks. Learn how to approach BitLocker volumes depending on the type of protector.
Under the Hood
The Introduction to BitLocker: Protecting Your System Disk describes how BitLocker works from the user’s perspective. Let’s dig into more details about the various encryption keys used by BitLocker to protect your data and the encryption key.
BitLocker implements staged protection and employs multiple keys, each serving its own purpose.
According to Microsoft, raw data is encrypted with the full volume encryption key (FVEK), which is then encrypted with the volume master key (VMK). The volume master key is in turn encrypted by one of several possible methods depending on the chosen authentication type (that is, key protectors or TPM) and recovery scenarios.
Does the VMK in this scheme looks redundant? It has its purpose. The use of intermediate key (VMK between FVEK and any key protectors) allows changing the keys without the need to re-encrypt the raw data in a case a given key protector is compromised or changed. When changing a key protector, a new VMK will be created and used to encrypt the old FVEK with the new VMK.
Where are all of these keys stored? The full volume encryption key (FVEK) is encrypted by the volume master key (VMK) and stored in the encrypted drive. The volume master key is encrypted by the appropriate key protector and also stored in the encrypted drive.
The thing is, it would not be possible to access the encrypted data if the appropriate encryption key was not stored in the computer’s volatile memory (RAM). While the BitLocker volume is mounted, the volume master key (VMK) resides in the computer’s RAM. By creating a memory dump and extracting the VMK from that dump with Elcomsoft Forensic Disk Decryptor, experts can instantly mount or quickly decrypt the content of the volume regardless of the type of protector used.
BitLocker Protector Types
BitLocker volumes (or, rather, the volume master keys) can be protected with various methods called protectors. With some of these protectors, the protection is hardware bound. As a result, in order to unlock the volume and decrypt the data, you will need either the original piece of hardware (and possibly other credentials); the brute force attack will not be feasible. Let us check which key protectors exist, how they are used, and how to approach the attack of a BitLocker volume protected with a given protector type.
You can determine the types of protectors enabled for a given BitLocker volume by executing the following command while the volume is mounted:
manage-bde -protectors -get X:
where X: would be the drive letter. (Source: BitLocker: Use BitLocker Drive Encryption Tools to manage BitLocker).
TPM only
This is by far the most used protector type on portable devices such as notebooks, Windows tablets and two-in-ones. Your system will boot to login prompt; the VMK will be decrypted with a storage root key (SRK) that is stored in the TPM (or Intel PTT) module and only releases if the system passes the Secure Boot check. This is the most convenient option that effectively protects hard drives but offers weaker protection if the intruder has access to the whole system (computer with TPM and the hard drive).
It is important to understand that a fully encrypted BitLocker volume will be automatically mounted and unlocked during the Windows boot process, long before the user signs in to the system with their Windows credentials. The TPM module will release the encryption metadata and decrypt the protected volume master key (VMK) automatically during the boot sequence, as shown in the image below.
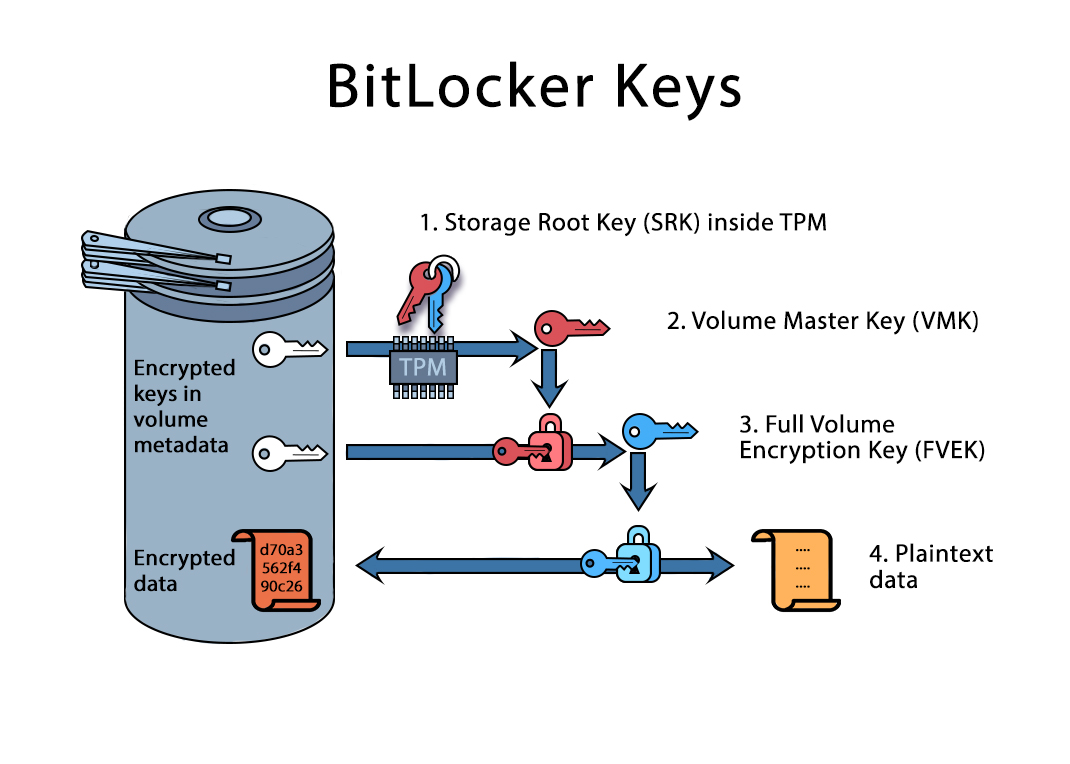
This allows performing a quite unique attack often called the ‘cold boot attack. The attacker would start the computer and wait while the system boots up. By the time the computer presents the login prompt, the BitLocker volume would be already mounted, and the VMK decrypted and stored in the computer’s RAM. The attacker would then dump the content of the computer’s volatile memory (by using a side attack or by physically removing the modules), extract VMK and decrypt the volume.
Attack vectors: Since there is no user-selectable password, attacking TPM only BitLocker volumes requires either of the following.
- BitLocker Recovery Key. Windows creates a recovery key automatically when encrypting BitLocker volumes with BitLocker Device Protection; such recovery keys are automatically (and silently) uploaded into the user’s Microsoft Account. You may be able to request that key from Microsoft or download it by signing in to the user’s Microsoft Account and visiting the following link: https://account.microsoft.com/devices/recoverykey
- BitLocker Recovery Key. Additional options may exist depending on the environment (e.g. Active Directory): Finding your BitLocker recovery key in Windows 10
- Cold boot attack. BitLocker in its default configuration uses a trusted platform module that neither requires a pin, nor an external key to decrypt the disk. When the operating system boots, BitLocker retrieves the key from the TPM, without any user interaction. Consequently, you may be able to simply power on the machine, wait for the operating system to begin booting and then execute a cold boot attack against the machine to retrieve the key. Note that this attack is unavailable if an unavailable protector type was used in addition to TPM.
- RAM dump. If you have access to the user’s computer, and you are able to sign in on that computer or obtain a memory dump via a FireWire/Thunderbolt attack, you may be able to retrieve the encryption keys cached in memory. Elcomsoft Forensic Disk Decryptor has tools for both dumping the memory and analyzing memory dumps.
TPM + PIN
In this mode, the TPM module will only release the encryption key if you correctly type the PIN code during pre-boot phase. Even though the PIN code is short, entering the wrong PIN several times makes TPM panic and block access to the encryption key. This option arguably offers the best balance between security and convenience, combining “something that you have” (the TPM module) with “something that you know” (the PIN code). At the same time, this option may not be convenient in multi-user environments.
Attack vectors: Since TPM+PIN is an interactive mode, you will be required to produce the correct PIN, which then must be entered on the computer containing the TPM module. Note that brute-forcing the PIN may not be an option since all TPM vendors provide built-in protection against such attacks. Unless you are able to circumvent this protection, recovering the PIN may not be possible.
The following attack vectors are available.
- BitLocker Recovery Key. Same as above.
- Cold boot attack is only available if you know the PIN. If you don’t, the system won’t be able to boot past the volume unlock prompt.
- RAM dump. Same as above. If you have access to the user’s computer, and you are able to sign in on that computer or obtain a memory dump via a FireWire/Thunderbolt attack, you may be able to retrieve the encryption keys cached in memory with Elcomsoft Forensic Disk Decryptor.
TPM + USB Key
This option requires both the TPM and a USB flash drive (or CCID smartcard) to be present in order for the system to boot. This is not a standard configuration, but may be enforced by security policies.
Attack vectors: Since TPM+USB Key requires a key file stored on a USB drive, you will be required to present that USB key in order to decrypt the VMK.
The following attack vectors are available.
- BitLocker Recovery Key. Same as above.
- Cold boot attack is only available if you have the USB Key. If you don’t, the system won’t be able to boot past the volume unlock prompt.
- RAM dump. Same as above. If you have access to the user’s computer, and you are able to sign in on that computer or obtain a memory dump via a FireWire/Thunderbolt attack, you may be able to retrieve the encryption keys cached in memory with Elcomsoft Forensic Disk Decryptor.
TPM + PIN + USB Key
Just as the name suggests, this option requires all three of the TPM, PIN code and USB key/smartcard in order to boot your computer. While this is probably the most secure option, the additional security benefits are hardly worth it compared to the TPM + PIN option if you consider the reduced convenience and reliability (you’ll have to use the recovery key if a USB key or smart card gets lost or corrupted).
Attack vectors: Since this protector requires both the PIN code and the key file stored on a USB drive, you will be required to produce both to satisfy the TPM module and release the decrypted VMK.
The following attack vectors are available.
- BitLocker Recovery Key. Same as above.
- Cold boot attack is only available if you have both the PIN and the USB Key. If you don’t, the system won’t be able to boot past the volume unlock prompt.
- RAM dump. Same as above. If you have access to the user’s computer, and you are able to sign in on that computer or obtain a memory dump via a FireWire/Thunderbolt attack, you may be able to retrieve the encryption keys cached in memory with Elcomsoft Forensic Disk Decryptor.
USB Key
This is one of the more interesting options since it is often used by users whose computers are not equipped with a TPM module or Intel PTT.
Attack vectors: There is still no password to attack (wait for the next option!), so you will require the USB key in order to decrypt the VMK. However, the VMK can be decrypted on any computer as this time the TPM is out of the question.
The following attack vectors are available.
- BitLocker Recovery Key. Same as above.
- Cold boot attack is only available if you have the USB Key. If you don’t, the system won’t be able to boot past the volume unlock prompt.
- RAM dump. Same as above. If you have access to the user’s computer, and you are able to sign in on that computer or obtain a memory dump via a FireWire/Thunderbolt attack, you may be able to retrieve the encryption keys cached in memory with Elcomsoft Forensic Disk Decryptor.
Password only
Just like the previous option, “password only” authentication is frequently used if no TPM or Intel PTT is available. Note that the “password” option is different from the “PIN” as there is no enforceable limit on the number of password attempts without a TPM, which allows a brute-force attack on the password.
Attack vectors: We are finally there. Password only is the only BitLocker protector allowing for a brute force (or dictionary) attack. Similar to the previous case, the VMK can be decrypted on any computer as this time the TPM is out of the question.
The following attack vectors are available.
- BitLocker Recovery Key. Same as above.
- Cold boot attack is only available if you know the password. If you don’t, the system won’t be able to boot past the volume unlock prompt.
- RAM dump. Same as above. If you have access to the user’s computer, and you are able to sign in on that computer or obtain a memory dump via a FireWire/Thunderbolt attack, you may be able to retrieve the encryption keys cached in memory with Elcomsoft Forensic Disk Decryptor.
- Brute force. Yes, we are finally there. You may use Elcomsoft Forensic Disk Decryptor to extract encryption metadata from the captured disk image and pass it along to Elcomsoft Distributed Password Recovery for attack. Alternatively, you can use Elcomsoft System Recovery to boot the user’s computer without removing the hard drives, then extract encryption metadata and pass it along to Elcomsoft Distributed Password Recovery.
Breaking BitLocker Password
Whether or not you’ll be able to break the BitLocker volume depends on multiple factors, such as the type of protector (TPM, password, key etc.), the availability of recovery information (BitLocker Recovery Key) or memory dump/hibernation file/page file, as well as whether you have the complete PC or just the disk/image. We have already posted about the different vectors of attack, namely: extracting the BitLocker Recovery Key from the user’s Microsoft Account and dumping and analyzing the computer’s RAM/hibernation/page files.
The RAM dump/hibernation file/page file attack
This attack is universal, and works regardless of the type of protector. Whether the volume is encrypted with TPM, USB key, password, or any combination thereof, the VMK will remain in the computer’s volatile memory (and possibly in the page/hibernation file) at all times while the encrypted volume is mounted.
The attack: How to Instantly Access BitLocker, TrueCrypt, PGP and FileVault 2 Volumes and Breaking BitLocker Encryption: Brute Forcing the Backdoor (Part I)
Extracting hibernation/page files with Elcomsoft System Recovery: A Bootable Flash Drive to Extract Encrypted Volume Keys, Break Full-Disk Encryption
BitLocker recovery keys
In many situations (e.g. the use of BitLocker Device Encryption on portable devices), BitLocker recovery keys are be stored in the user’s Microsoft Account. Extracting those keys from their account allows instantly mounting or decrypting protected volumes regardless of the type of protector.
The attack: Breaking into Microsoft Account: It’s No Google, But Getting Close (scroll down to BitLocker recovery keys).
The password
Finally, we are there. BitLocker passwords are used to protect volumes stored on external devices (including regular BitLocker and BitLocker To Go). The password is also the default when it comes to protecting fixed, non-system volumes. In other words, BitLocker passwords are extremely likely to be used on anything but the system volume. Passwords on bootable (system) volumes are rarely encountered as BitLocker’s default policy is TPM only. Using a password (without TPM) is blocked by the default security policy. While users may edit the policy and enable password-only BitLocker protection on the boot volume, this is fairly uncommon.
The attack is broken into two distinct stages.
- Extracting hash values (encryption metadata) from the encrypted volume(s). This step is required, as it is much easier (and significantly better from the security standpoint) to pass the a very small hash file with encryption metadata instead of the whole container. Depending on your situation, you may use either Elcomsoft Forensic Disk Decryptor (supplied with EDPR) or Elcomsoft System Recovery (available stand-alone or as part of Elcomsoft Desktop Forensic Bundle).
- Perform the attack (brute-force, dictionary or hybrid) with Elcomsoft Distributed Password Recovery.
Step 1.1: Extracting BitLocker encryption metadata with Elcomsoft Forensic Disk Decryptor
Use Elcomsoft Distributed Password Recovery to extract encryption metadata from BitLocker-protected forensic disk images. The encryption metadata will be saved into a small file that you can safely transfer to the computer where you’ll be performing the actual attack on the password. In order to extract the encryption metadata, do the following.
- Launch Elcomsoft Forensic Disk Decryptor.
- Select “Extract/prepare data for further password recovery“.
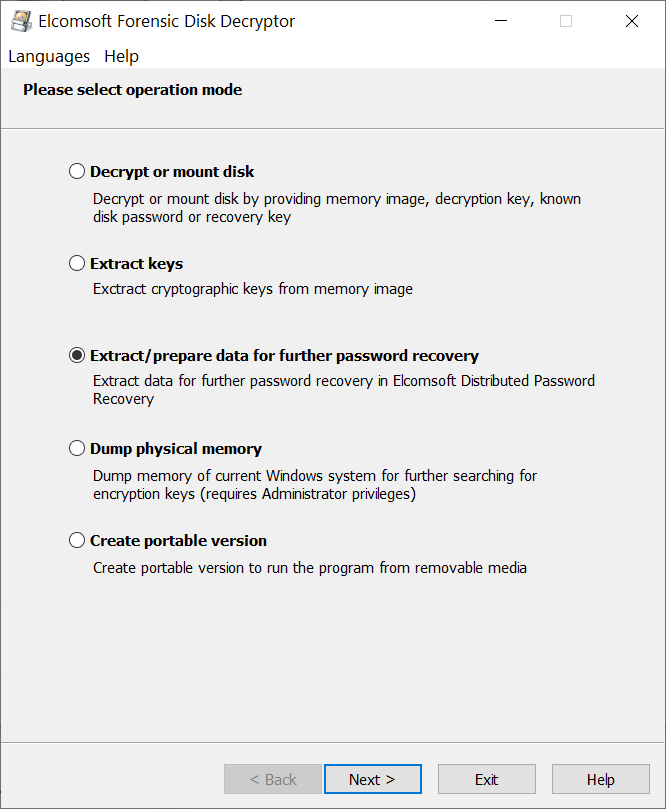
- Open the physical device or disk image containing BitLocker volume(s). In the example below, we’re dealing with a physical device.
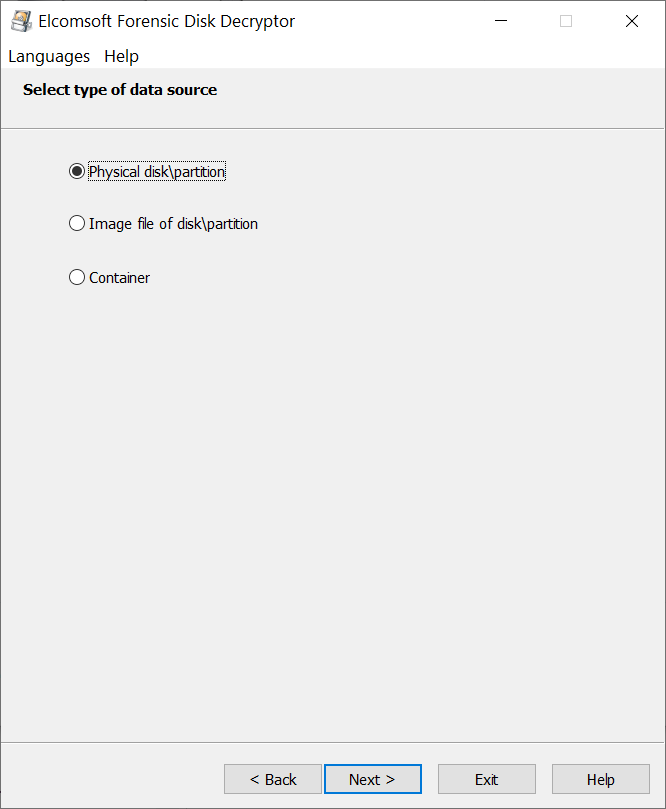
- EFDD will display the list of encrypted volumes. Select the volume you are about to extract hashes from.
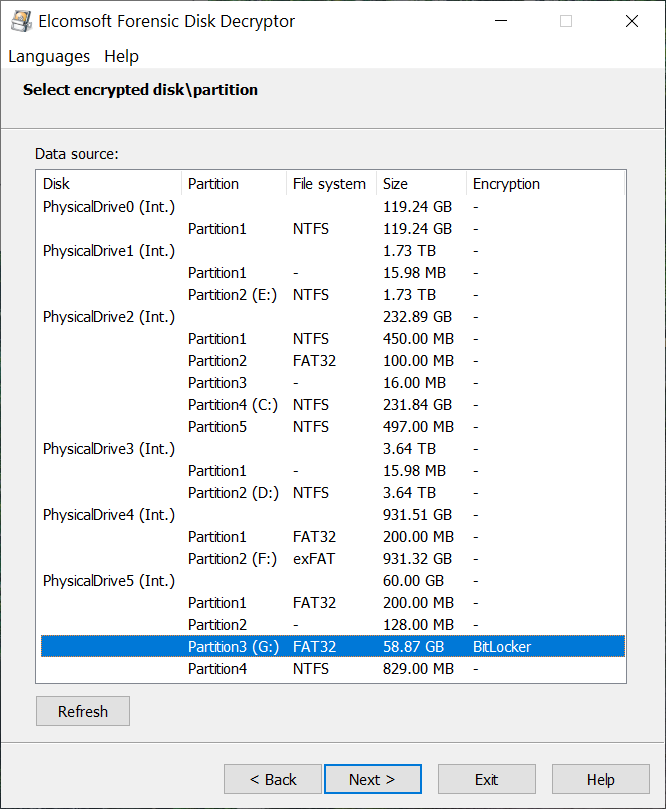
- Click Next to extract the encryption metadata and save it into a file.
Important: You will be able to perform a password attack if and only if the BitLocker volume is protected with a password. All other types of protectors (TPM, TPM+PIN, USB Key etc.) do not have a password to recover and are not supported. Attacking a BitLocker volume protected with a different type of protector would be a waste of time. Therefore, EFDD will warn you if the partition you are about to extract is protected with a non-password type of protector:
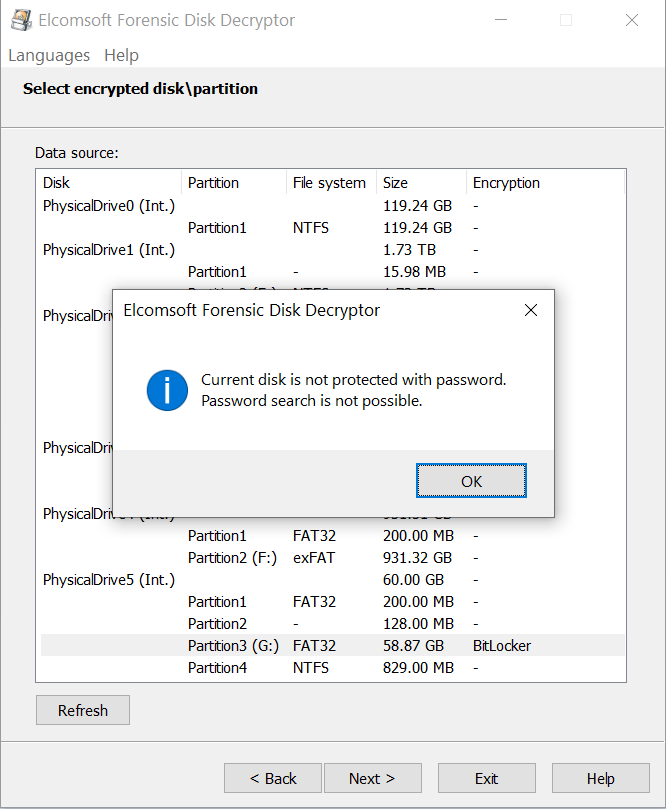
If this is the case, consider a different attack vector.
Step 1.2: Extracting BitLocker encryption metadata with Elcomsoft System Recovery
The traditional acquisition approach requires disassembling the computer, removing and imaging all of its storage devices. However, all one really needs to start the attack on the password of an encrypted volume is a few kilobytes worth of encryption metadata. The metadata can be extracted significantly faster without removing the hard drives.
Elcomsoft System Recovery allows starting the investigation sooner by booting the computer from a portable flash drive with read-only access to computer’s storage devices. The tool automatically detects full disk encryption on all built-in and removable drives, and allows extracting encryption metadata that is required to brute-force the original password to encrypted disk volumes. Since crypto-containers, by design, are making attacks on the passwords extremely slow, we recommend executing a dictionary-based distributed attack with Elcomsoft Distributed Password Recovery.
In order to extract encryption metadata with Elcomsoft System Recovery, do the following.
- Install Elcomsoft System Recovery to your computer (not the suspect’s computer).
- Create a bootable flash drive. Make sure to specify the correct configuration of the target system (BIOS or UEFI, 32-bit or 64-bit). In general, we recommend using a high-speed flash stick of at least 32GB. Instructions on creating a bootable ESR flash drive are available here.
- Boot the target system from the flash drive you have just created.
- Elcomsoft System Recovery will be launched once the boot sequence is complete. From the following window, select Disk tools.
- Select Copy Drive encryption keys.
- Elcomsoft System Recovery will automatically detect full-disk encryption on all fixed and removable drives.
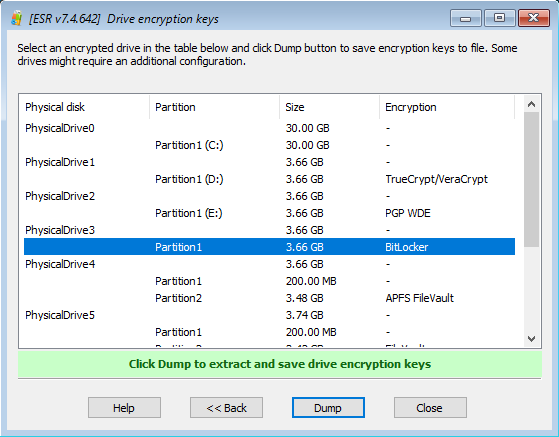
- Select the volume(s) to process.
- Once you have finished dumping the encryption metadata, transfer the files to Elcomsoft Distributed Password Recovery to recover the original plain-text password. Note that password attacks may take significant time even with powerful hardware.
Important: You will be able to perform a password attack if and only if the BitLocker volume is protected with a password. All other types of protectors (TPM, TPM+PIN, USB Key etc.) do not have a password to recover and are not supported. Attacking a BitLocker volume protected with a different type of protector would be a waste of time. Therefore, ESR will warn you if the partition you are about to extract is protected with a non-password type of protector:
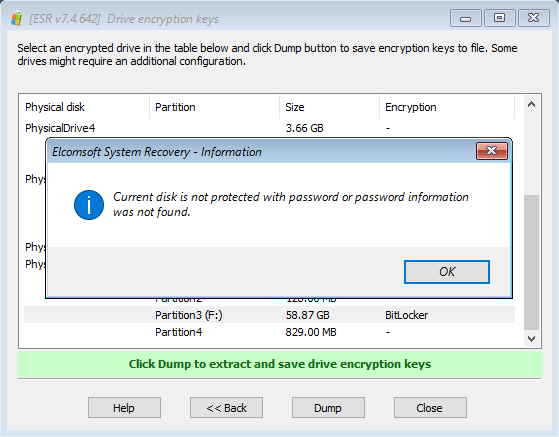
Step 2: Attacking BitLocker password with Elcomsoft Distributed Password Recovery
In order to recover the BitLocker volume password, do the following.
- Launch Elcomsoft Distributed Password Recovery
- Open encryption metadata (the hash file) produced by either Elcomsoft Forensic Disk Decryptor or Elcomsoft System Recovery during the previous step.
- Configure and launch the attack.
While the three steps appear simple, running the default brute-force attack is one of the least effective ways to break BitLocker encryption. We strongly recommend configuring a smart attack based on patterns observed in the user’s existing passwords. Microsoft did an excellent work to protect BitLocker containers against brute-forcing the password. However, we have significant advances in password recovery attacks compared to what we had some ten years back. Brute-forcing a password today becomes significantly faster due to the use of GPU acceleration, distributed and cloud computing. Up to 10,000 computers and on-demand cloud instances can be used to attack a single password with Elcomsoft Distributed Password Recovery.
Brute force attacks became not just faster, but much smarter as well. The user’s existing passwords are an excellent starting point. These passwords can be pulled from the user’s Google Account, macOS, iOS or iCloud keychain, Microsoft Account, or simply extracted from the user’s computer. The user’s existing passwords give a hint at what character groups are likely used:
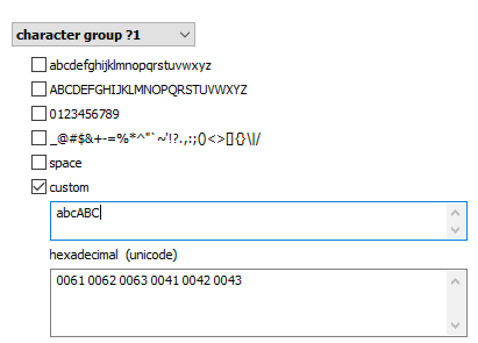
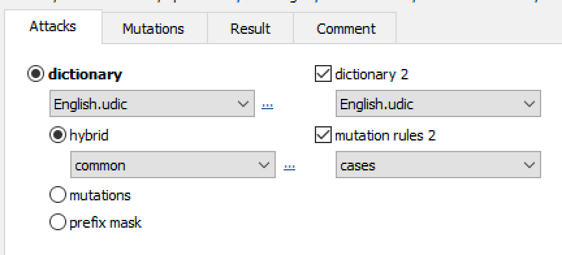
Elcomsoft Distributed Password Recovery offers a number of options to automatically try the most common variations of your password (such as the Password1, password1967 or pa$$w0rd):
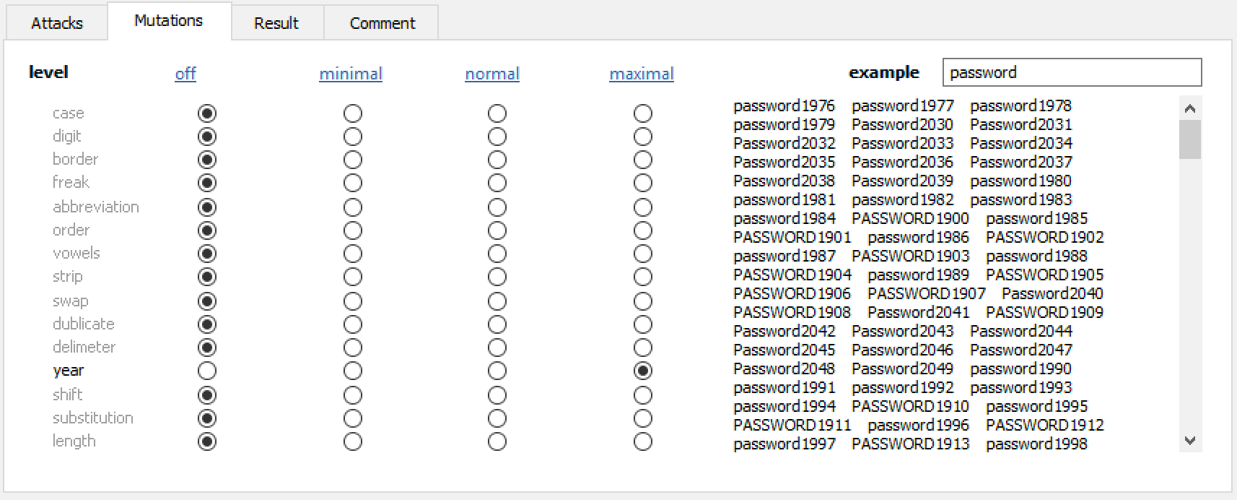
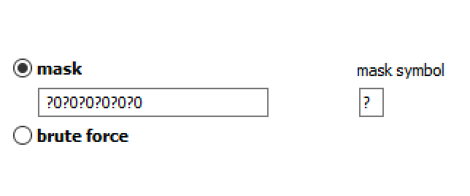
Masks can be used to try passwords matching established common patterns:
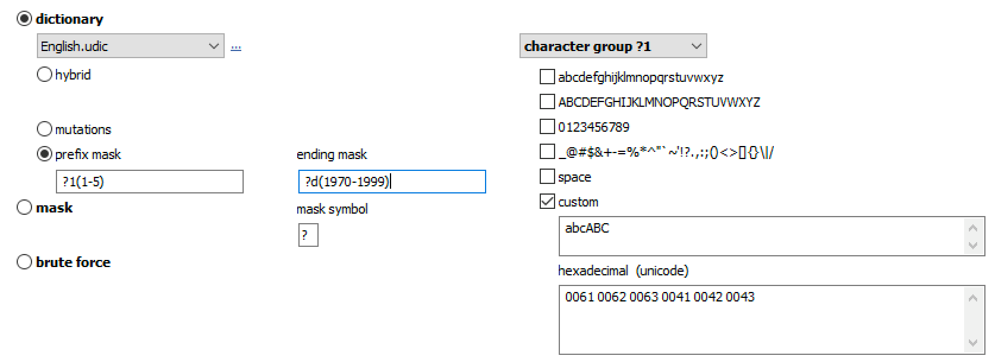
Advanced techniques allow composing passwords with up to two dictionaries and scriptable rules: