Forget battery issues. Yes, Apple issued an apology for slowing down the iPhone and promised to add better battery management in future versions of iOS, but that’s not the point in iOS 11.3. Neither are ARKit improvements or AirPlay 2 support. There is something much more important, and it is gong to affect everyone.
Apple iOS is (and always was) the most secure mobile OS. FBI forensic expert called Apple “evil genius” because of that. Full disk encryption (since iOS 4), very reliable factory reset protection, Secure Enclave, convenient two-factor authentication are just a few things to mention. Starting with iOS 8, Apple itself cannot break into the locked iPhone. While in theory they are technically capable of creating (and signing, as they hold the keys) a special firmware image to boot the device, its encryption is not based on a hardware-specific key alone (as was the case for iOS 7 and older, and still the case for most Androids). Instead, the encryption key is also based on the user’s passcode, which is now 6 digits by default. Cracking of the passcode is not possible at all, thanks to Secure Enclave. Still, in come cases, Apple may help law enforcement personnel, and they at least provide some trainings to FBI and local police.
The are three common extraction methods to acquire the iPhone data:
- Logical acquisition
- Physical acquisition
- Cloud acquisition
Let’s start with the last one. Cloud acquisition is nice as it does not require access to the device itself, and it does not matter whether the device is locked or not. Proper iCloud credentials are required, and if 2FA is enabled, then you also need to have the second factor. At least two workaround exists: first, you can access the account using authentication token instead of password, or get into the account from the trusted computer; and second, if the device itself is available, iCloud password can be reset. That way we can get a device backup from the cloud, as well as quite a lot of synced data (we’ll be adding even more soon, wait for Phone Breaker news).
Physical acquisition is probably even better – you can obtain virtually everything from the device, more than with other methods. This includes comprehensive location data and application-specific records. However, it requires the device to be unlocked, and you should be able (technically and legally) to install a jailbreak. For now, jailbreaks are available for most versions of iOS up to 11.1.2, but not for iOS 11.2 or later; we have the software to perform physical acquisition of jailbroken iPhones (iOS Forensic Toolkit), and right now are adding support for the latest jailbreaks. Still, if the iPhone is locked, the main question is: can you unlock it?
Logical acquisition is the most compatible method – and also the easiest. This is in fact jut creating an iTunes backup of the device, and though it contains less data than available via physical acquisition, the most important data is there: contacts, messages, call logs, Internet browsing history and much more.
The major problem is, however, that the phone should be unlocked in order the backup to be created. The is a workaround for this though: if you have access to the computer with which the particular iOS device has a “trusted relationship” established, you can get just one specific file from it, and use that file to acquire the backup from the locked device.
The other problem is that a backup created this way may have a password set. This password is a property if the device, you will have to break it, which is nearly impossible task for iOS 10.2+ (recovery speed is just hundreds passwords per second even on fast hardware). With iOS 11, Apple allows this password to be reset, but that can be done only for unlocked device, of course.
The other way to get some data from the locked iPhone (or unlocked, but with backup password set), again with the pairing record, is accessing media files (photos and videos). That will not give you access to the other records such as messages, but still something – especially taking in mind that media files may contain EXIF data with location information. Finally, we can get info on applications inmstalled on the device.
Oh, you did not know about pairing (lockdown) records? We write about that several times, but it worth repeating. When you connect iOS device to the new computer, it prompts you whether you trust it or not. If yes, you will have to unlock the device first, iTunes creates the pair of records (on on the iPhone, the other on PC) that allows iTunes to communicate with the iPhone even if it is locked. The purpose? Just the convenience, to prevent you from unlocking the device every time you connect it (to sync, copy media files, create backups etc). More info is available at The iPhone is Locked-Down: Dealing with Cold Boot Situations.
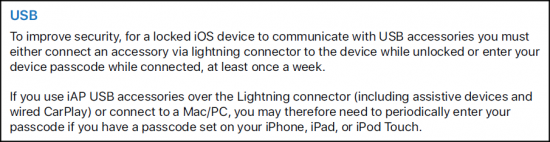
In iOS 11, serious improvement has been made there. iOS 11 requires the iPhone to be unlocked with a passcode, not with Touch ID (and if that operation is performed as a part of investigation process, it makes a problem: the passcode is harder to get). See New Security Measures in iOS 11 and Their Forensic Implications for details
With iOS 11.3, Apple has tightened the security even more. Now the pairing record expires after a week.
In 2017, over 30 thousand phones have been expected only by border agents. According to new DHS policy on border search, US Customts now have the full power to search all travellers’ electoric devices, but not cloud services.
This is not (only) about border control, of course. iPhone (as well as any other smartphone) is one of the most comprehensive sources of the evidence, and law enforcement officers all over the world need to unlock them every day, investigating the crimes from the sexual harrasments to terrorosm. For modern devices and iOS versions, logical acquisition using lockdown records was one of the most effective methods.
But not anymore.
Is that good or bad news? Obviously, good for privacy, but probably bad for the community in general. We do not judge.



