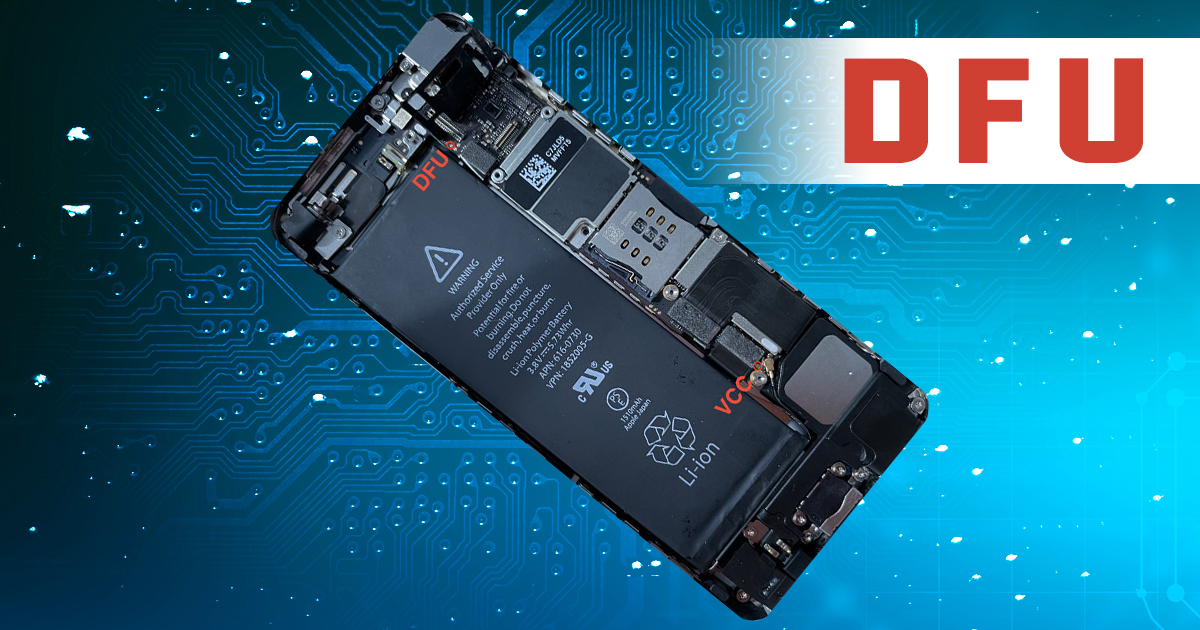
August 24th, 2021 by Oleg Afonin
iMessage, Hangouts, Skype, Telegram, Signal, WhatsApp are familiar, while PalTalk, Pigin, Psi Jabber client, Gadu-Gadu, Gajim, Trillian, BigAnt or Brosix are relatively little known. The tools from the first group are not only more popular but infinitely more secure compared to the tools from the second group. In this publication we’ll review the authentication methods used by the various instant messengers, and attempt to extract a password to the user’s account.
Read the rest of this entry »