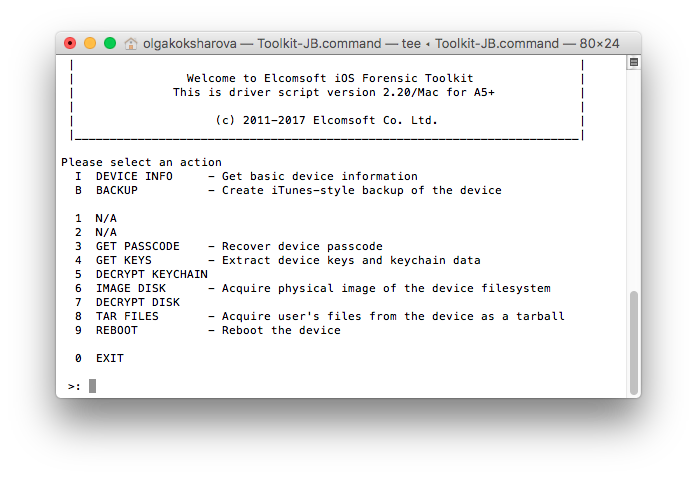
March 6th, 2026 by Oleg Afonin
Spoiler: you are probably already using AI agents, even if marketing hasn’t yelled at you about it yet. Forget the dark ages of 2023 when large language models (LLMs) just confidently hallucinated fake server logs and nonexistent IP addresses. Today’s AI can spin up a virtual environment, navigate web pages, scrape data, and logically process what it finds. Let’s cut through the noise and talk about what “agents” actually are, how “Deep Research” operates, and how to spin up your own pocket investigator that doesn’t come with corporate safety bumpers.
Read the rest of this entry »